A never-before-seen distant entry trojan dubbed ZuoRAT has been singling out small workplace/residence workplace (SOHO) routers as a part of a complicated marketing campaign concentrating on North American and European networks.
The malware “grants the actor the power to pivot into the native community and acquire entry to further programs on the LAN by hijacking community communications to keep up an undetected foothold,” researchers from Lumen Black Lotus Labs mentioned in a report shared with The Hacker Information.
The stealthy operation, which focused routers from ASUS, Cisco, DrayTek, and NETGEAR, is believed to have commenced in early 2020 throughout the preliminary months of the COVID-19 pandemic, successfully remaining below the radar for over two years.
“Customers and distant staff routinely use SOHO routers, however these gadgets are hardly ever monitored or patched, which makes them one of many weakest factors of a community’s perimeter,” the corporate’s menace intelligence workforce mentioned.
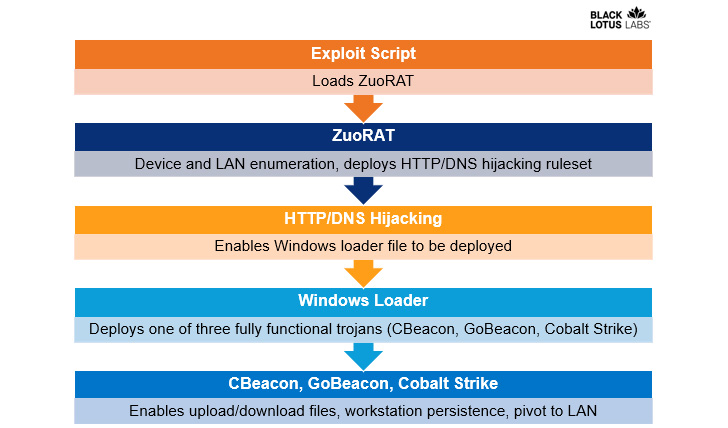
Preliminary entry to the routers is obtained by scanning for identified unpatched flaws to load the distant entry instrument, utilizing it acquire entry to the community and drop a next-stage shellcode loader that is used to ship Cobalt Strike and customized backdoors akin to CBeacon and GoBeacon which are able to working arbitrary instructions.
Along with enabling in-depth reconnaissance of goal networks, site visitors assortment, and community communication hijacking, the malware has been described as a closely modified model of the Mirai botnet, whose supply code leaked in October 2016.
“ZuoRAT is a MIPS file compiled for SOHO routers that may enumerate a number and inside LAN, seize packets being transmitted over the contaminated machine, and carry out person-in-the-middle assaults (DNS and HTTPS hijacking based mostly on predefined guidelines),” the researchers mentioned.
Additionally included is a perform to reap TCP connections over ports 21 and 8443, that are related to FTP and net searching, probably enabling the adversary to maintain tabs on the customers’ web exercise behind the compromised router.
Different capabilities of ZuoRAT permit the attackers to watch DNS and HTTPS site visitors with an purpose to hijack the requests and redirect the victims to malicious domains utilizing preset guidelines which are generated and saved in short-term directories in an try to withstand forensic evaluation.
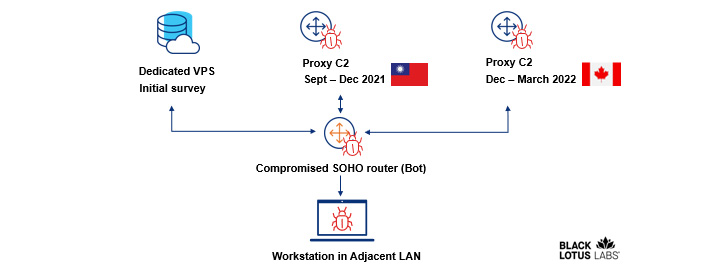
That is not the one step taken by the hackers to hide its actions, for the assaults depend on an obfuscated, multi-stage C2 infrastructure that entails using a digital non-public server to drop the preliminary RAT exploit and leveraging the compromised routers themselves as proxy C2 servers.
To additional keep away from detection, the staging server has been noticed internet hosting seemingly innocuous content material, in a single occasion mimicking a web site known as “muhsinlar.internet,” a propaganda portal arrange for the Turkestan Islamic Social gathering (TIP), a Uyghur extremist outfit originating from China.
The identification of the adversarial collective behind the marketing campaign stays unknown, though an evaluation of the artifacts has revealed attainable references to the Chinese language province of Xiancheng and using Alibaba’s Yuque and Tencent for command-and-control (C2).
The flowery and evasive nature of the operation coupled with the ways used within the assaults to stay undercover level towards potential nation-state exercise, Black Lotus Labs famous.
“The capabilities demonstrated on this marketing campaign — having access to SOHO gadgets of various makes and fashions, gathering host and LAN info to tell concentrating on, sampling and hijacking community communications to achieve probably persistent entry to in-land gadgets and deliberately stealth C2 infrastructure leveraging multistage siloed router to router communications — factors to a extremely subtle actor,” the researchers concluded.