A brand new variant of the Android banking trojan named Xenomorph has surfaced within the wild, the newest findings from ThreatFabric reveal.
Named “Xenomorph third era” by the Hadoken Safety Group, the menace actor behind the operation, the up to date model comes with new options that permit it to carry out monetary fraud in a seamless method.
“This new model of the malware provides many new capabilities to an already feature-rich Android banker, most notably the introduction of a really intensive runtime engine powered by Accessibility providers, which is utilized by actors to implement an entire ATS framework,” the Dutch safety agency mentioned in a report shared with The Hacker Information.
Xenomorph first got here to gentle a 12 months in the past in February 2022, when it was discovered to focus on 56 European banks via dropper apps printed on the Google Play Retailer.
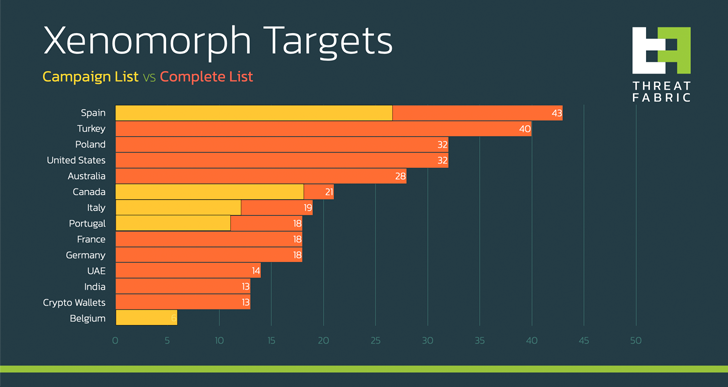
In distinction, the newest iteration of the banker – which has a devoted web site promoting its options – is designed to focus on greater than 400 banking and monetary establishments, together with a number of cryptocurrency wallets.
ThreatFabric mentioned it detected samples distributed through Discord’s Content material Supply Community (CDN), a method that has witnessed a surge since 2020. Two of the Xenomorph-laced apps are listed under –
- Play Defend (com.nice.calm)
- Play Defend (meritoriousness.mollah.presser)
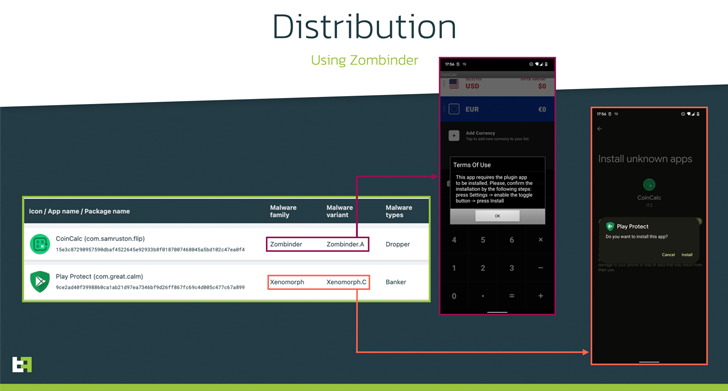
“Xenomorph v3 is deployed by a Zombinder app ‘certain’ to a professional foreign money converter, which downloads as an ‘replace’ an software posing as Google Defend,” ThreatFabric defined.
Zombinder refers to an APK binding service marketed on the darkish net since March 2022, whereby the malware is delivered through trojanized variations of professional apps. The providing has since been shut down.
Targets of the newest marketing campaign transcend its European focus (i.e., Spain, Italy, and Portugal) to incorporate Belgian and Canadian monetary entities.
Uncover the Hidden Risks of Third-Get together SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be part of our webinar to be taught concerning the varieties of permissions being granted and easy methods to decrease danger.
Xenomorph, like banking malware, is thought to abuse Accessibility Providers to carry out fraud via overlay assaults. It additionally packs in capabilities to robotically full fraudulent transactions on contaminated gadgets, a method referred to as Automated Switch System (ATS).
With banks shifting away from SMS for two-factor authentication (2FA) to authenticator apps, the Xenomorph trojan incorporates an ATS module that permits it to launch the app and extract the authenticator codes.
The Android malware additional boasts of cookie-stealing features, enabling the menace actors to carry out account takeover assaults.
“With these new options, Xenomorph is now capable of utterly automate the entire fraud chain, from an infection to funds exfiltration, making it probably the most superior and harmful Android Malware trojans in circulation,” the corporate mentioned.