This month’s Patch Tuesday gives just a little one thing for everybody, together with safety updates for a zero-day flaw in Microsoft Home windows that’s beneath lively assault, and one other Home windows weak spot specialists say may very well be used to energy a fast-spreading pc worm. Additionally, Apple has additionally quashed a pair of zero-day bugs affecting sure macOS and iOS customers, and launched iOS 16, which gives a brand new privateness and safety characteristic known as “Lockdown Mode.” And Adobe axed 63 vulnerabilities in a spread of merchandise.
Microsoft at this time launched software program patches to plug a minimum of 64 safety holes in Home windows and associated merchandise. Worst when it comes to outright scariness is CVE-2022-37969, which is a “privilege escalation” weak spot within the Home windows Widespread Log File System Driver that enables attackers to realize SYSTEM-level privileges on a susceptible host. Microsoft says this flaw is already being exploited within the wild.
Kevin Breen, director of cyber risk analysis at Immersive Labs, mentioned any vulnerability that’s actively focused by attackers within the wild should be put to the highest of any patching record.
“To not be fooled by its comparatively low CVSS rating of seven.8, privilege escalation vulnerabilities are sometimes extremely wanted by cyber attackers,” Breen mentioned. “As soon as an attacker has managed to realize a foothold on a sufferer’s system, certainly one of their first actions shall be to realize a better stage of permissions, permitting the attacker to disable safety purposes and any system monitoring. There isn’t a recognized workaround thus far, so patching is the one efficient mitigation.”
Satnam Narang at Tenable mentioned CVE-2022-24521 — an identical vulnerability in the identical Home windows log file element — was patched earlier this yr as a part of Microsoft’s April Patch Tuesday launch and was additionally exploited within the wild.
“CVE-2022-37969 was disclosed by a number of teams, although it’s unclear if CVE-2022-37969 is a patch-bypass for CVE-2022-24521 at this level,” Narang mentioned.
One other vulnerability Microsoft patched this month — CVE-2022-35803 — additionally appears to be associated to the identical Home windows log file element. Whereas there aren’t any indications CVE-2022-35803 is being actively exploited, Microsoft means that exploitation of this flaw is extra doubtless than not.
Pattern Micro’s Dustin Childs known as consideration to CVE-2022-34718, a distant code execution flaw within the Home windows TCP/IP service that would permit an unauthenticated attacker to execute code with elevated privileges on affected techniques with out person interplay.
“That formally places it into the ‘wormable’ class and earns it a CVSS ranking of 9.8,” Childs mentioned. “Nonetheless, solely techniques with IPv6 enabled and IPSec configured are susceptible. Whereas excellent news for some, for those who’re utilizing IPv6 (as many are), you’re in all probability operating IPSec as properly. Positively take a look at and deploy this replace shortly.”
Cisco Talos warns about 4 crucial vulnerabilities fastened this month — CVE-2022-34721 and CVE-2022-34722 — which have severity scores of 9.8, although they’re “much less doubtless” to be exploited, in response to Microsoft.
“These are distant code execution vulnerabilities within the Home windows Web Key Trade protocol that may very well be triggered if an attacker sends a specifically crafted IP packet,” wrote Jon Munshaw and Asheer Malhotra. “Two different crucial vulnerabilities, CVE-2022-35805 and CVE-2022-34700 exist in on-premises cases of Microsoft Dynamics 365. An authenticated attacker might exploit these vulnerabilities to run a specifically crafted trusted answer bundle and execute arbitrary SQL instructions. The attacker might escalate their privileges additional and execute instructions because the database proprietor.”
 To not be outdone, Apple fastened a minimum of two zero-day vulnerabilities when it launched updates for iOS, iPadOS, macOS and Safari. CVE-2022-32984 is an issue within the deepest recesses of the working system (the kernel). Apple pushed an emergency replace for a associated zero-day final month in CVE-2022-32983, which may very well be used to foist malware on iPhones, iPads and Macs that visited a booby-trapped web site.
To not be outdone, Apple fastened a minimum of two zero-day vulnerabilities when it launched updates for iOS, iPadOS, macOS and Safari. CVE-2022-32984 is an issue within the deepest recesses of the working system (the kernel). Apple pushed an emergency replace for a associated zero-day final month in CVE-2022-32983, which may very well be used to foist malware on iPhones, iPads and Macs that visited a booby-trapped web site.
Additionally listed beneath lively assault is CVE-2022-32817, which has been fastened on macOS 12.6 (Monterey), macOS 11.7 (Large Sur), iOS 15.7 and iPadOS 15.7, and iOS 16. The identical vulnerability was fastened in Apple Watch in July 2022, and credit Xinru Chi of Japanese cybersecurity agency Pangu Lab.
“Apparently, this CVE can also be listed within the advisory for iOS 16, however it’s not known as out as being beneath lively exploit for that taste of the OS,” Pattern Micro’s Childs famous. “Apple does state in its iOS 16 advisory that ‘Further CVE entries to be added quickly.’ It’s potential different bugs might additionally affect this model of the OS. Both means, it’s time to replace your Apple gadgets.”
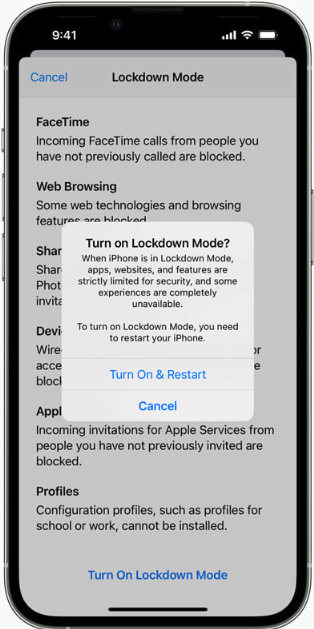
Apple’s iOS 16 contains two new safety and privateness options — Lockdown Mode and Security Test. Wired.com describes Security Test as a characteristic for customers who’re in danger for, or at the moment experiencing, home abuse.
“The software centralizes quite a few controls in a single place to make it simpler for customers to handle and revoke entry to their location knowledge and reset privacy-related permissions,” wrote Lily Hay Newman.
“Lockdown Mode, alternatively, is supposed for customers who doubtlessly face focused spy ware assaults and aggressive state-backed hacking. The characteristic comprehensively restricts any nonessential iOS options so there are as few potential factors of entry to a tool as potential. As extra governments and repressive entities around the globe have begun buying highly effective commodity spy ware to focus on people of specific significance or curiosity, iOS’s common safety defenses haven’t been capable of hold tempo with these specialised threats.”
To activate Lockdown Mode in iOS 16, go to Settings, then Privateness and Safety, then Lockdown Mode. Security Test is situated in the identical space.
Lastly, Adobe launched seven patches addressing 63 safety holes in Adobe Expertise Supervisor, Bridge, InDesign, Photoshop, InCopy, Animate, and Illustrator. Extra on these updates is right here.
Don’t overlook to again up your knowledge and/or system earlier than making use of any safety updates. In case you expertise glitches or issues putting in any of those patches this month, please contemplate leaving a remark about it under; there’s a good likelihood different readers have skilled the identical and should chime in right here with helpful ideas.

