%20(1).jpg?width=400&name=RogerMasterClass-FeatureImage%20(1)%20(1).jpg) KnowBe4 simply launched its official steerage and suggestions relating to password coverage. It has been a venture within the works for a lot of months now, however we needed to verify we received it proper. Listed here are our official password suggestions:
KnowBe4 simply launched its official steerage and suggestions relating to password coverage. It has been a venture within the works for a lot of months now, however we needed to verify we received it proper. Listed here are our official password suggestions:
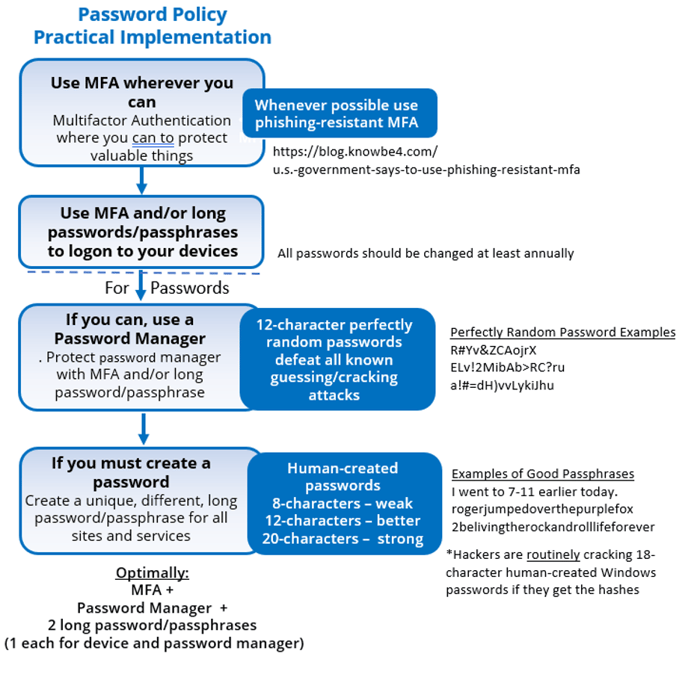
The abstract of our really helpful password coverage is:
- Use phishing-resistant MFA the place you’ll be able to
For those who can’t use MFA, then:
- Use a password supervisor to create lengthy and complicated passwords wherever you’ll be able to
- For those who should create your individual passwords, make them 20-characters or longer
The optimum suggestion is a state of affairs the place everybody would have one or two human-created lengthy passphrases/passsentences, if wanted, and use a password supervisor or MFA for all the pieces else. The human-created passphrases/passsentences can be those wanted to log into your system(s) and your password supervisor (if wanted for these cases).
Our Suggestions vs. NIST’s Suggestions
We all know plenty of readers are cringing on the thought of getting to create 20-character passwords to be actually safe, particularly in gentle of another official steerage from the Nationwide Institute of Requirements and Expertise (NIST), from 2017, the Digital Id Tips saying that lengthy and complicated passwords usually are not wanted.
NIST mentioned this as a result of it’s a identified truth that almost all assaults in opposition to passwords (e.g., social engineering, theft and bypass) don’t care what your password is. A hacker can trick somebody out of their very lengthy and complicated password as simply as a easy password and malware and hackers can steal both sort with equal effort. As a result of most password assaults don’t care how lengthy or complicated your password is and since customers being compelled to create many lengthy and complicated passwords are much more more likely to reuse the identical ones throughout a number of web sites and providers, which is a far larger danger to most organizations. NIST recommends no official minimal password size, no required complexity and even no compelled obligatory password modifications.
NIST’s new recommendation (new as in printed in 2017), went in opposition to all their earlier recommendation, and in opposition to a lot of the world’s typical understanding of what passwords needed to be to lower cybersecurity danger. It was such a controversial second that also, over 5 years later, most regulatory guides and necessities don’t permit quick, non-complex and by no means altering passwords.
We don’t advocate NIST’s password coverage suggestions both. Allow us to clarify why.
NIST is true, individuals who must create lengthy and complicated passwords shall be incentivized to reuse them throughout a number of unrelated websites and providers. We don’t want folks to must create lengthy and actually complicated passwords both, despite the fact that it’s the neatest thing they might do risk-wise, if they might do it.
The one two assault situations the place the size and complexity of a password are essential are guessing on the password (normally inside an internet login immediate) and password hash cracking. The speed at which an attacker can guess at a specific password in an internet assault is proscribed by the what number of guesses the attacker could make in a specific time interval. Oftentimes, password guessing is proscribed by some type of rate-throttling mechanism, like account lockout, the place after too many unhealthy guesses, the concerned account is locked out (both for a pre-set time period or till somebody unlocks it). In lots of networks, password guessing in opposition to a person account is likely to be restricted to solely a handful of guesses each quarter-hour. However there are numerous situations the place attackers have been in a position to guess at an nearly unfettered velocity approaching over 100,000 occasions a day.
That feels like plenty of guessing, and it’s, however a 12-character, human-created password with complexity guessed at on an internet portal begins to turn out to be tough for even unfettered attackers to efficiently guess until they’re given a really lengthy time period (e.g., over a 12 months) to try this unfettered guessing. However to be safer in opposition to password guessing, you must go longer. A really, completely random password turns into unguessable at round 11 characters, even when the attacker is allowed to guess trillions of occasions a second for many years.
With password hash cracking, the attacker has been in a position to beforehand acquire the potential sufferer’s password cryptographic hash (which takes a number of extra exploits) after which the hacker makes use of a really quick password hash guessing answer to attempt to guess on the plaintext password given the password’s hash. There are lots of password hash cracking “rigs” which may guess at many trillions of guesses a second. There are doubtless many tons of of attackers with the native functionality to guess at hashes at tens of trillions of guesses a second and that type of functionality may be bought from many various cloud distributors for pretty low cost sums. The very best velocity current password hash cracking rigs are regarded as on the 100 trillion guesses per second. Might your password/password hash survive if guessed at many trillions of occasions a second? Most individuals’s passwords wouldn’t stand for very lengthy.
However once more, a very, completely random password turns into unguessable at round 11 characters. So, we advocate 12-character completely random passwords to defeat all at the moment identified password guessing and cracking assaults.
We, like NIST, don’t want folks creating lengthy and complicated passwords. We imagine that the actually, completely random passwords created by password managers are simpler to make use of and higher lower danger than most human-created passwords. That’s the reason we advocate that customers use a trusted password supervisor to create and use completely random passwords, wherever doable, wherever phishing-resistant MFA can’t be used.
NIST is aware of about super-fast password hash cracking rigs, too, in addition to password managers. So, why does NIST not additionally advocate MFA and password managers? First, they do advocate utilizing MFA and permit it for use on all ranges of methods. They do say in NIST SP 800-63 to keep away from utilizing MFA linked to telephone numbers (e.g., SMS-based or voice-based MFA) for something however the lowest stage methods.
NIST doesn’t explicitly point out password managers (not less than in NIST SP 800-63 and different authentication-related paperwork I can discover), however they do advocate very excessive entropy (i.e., extremely random) passwords dozens of occasions, which password managers are uniquely suited to. NIST is usually dismissive of passwords (and PINs) fully, no matter entropy and make-up, aside from the bottom worth methods. It’s clear that NIST needs defenders to maneuver away from password-based authentication due to all of the threats and assaults in opposition to them.
Nevertheless, the most important cause we disagree with NIST’s extra relaxed password suggestions is that password hash theft and cracking has turn out to be a much bigger risk than ever earlier than. Sure, password theft assaults are a far larger proportion of assaults, and with these assaults, your password size and complexity don’t matter.
However we strongly imagine that NIST didn’t contemplate the relative danger of password hash theft on the general safety danger of most organizations. In a nutshell, password hash theft and cracking has turn out to be simpler to do than ever. And if an attacker can achieve entry to your system and/or community, it truly is recreation over for any human-created passwords shorter than 20 characters, particularly if operating on a Home windows system or community. Let’s clarify extra.
Password Hash Theft Strategies
Historically, when somebody sorts of their new password for the primary time into an working system (or functions that make the most of password hashes), the plaintext password is transformed to a cryptographic hash illustration of that plaintext password. It’s that password hash that’s saved inside the working system, normally in recordsdata positioned regionally or on the community, and which might be utilized in authentication. Attackers getting the hashes don’t get entry straight, instantly, to the person’s plaintext password, however entry to the password hash they will start attempting to crack it again to the plaintext password.
Historically, to ensure that an attacker to get somebody’s password hash, they needed to someway acquire tremendous elevated administrator or system entry to the working system after which go to the password hash storage recordsdata or run a script or software to acquire the hashes. It took the attacker getting tremendous admin entry to start the password hash crack course of. And though hackers routinely get this stage of entry on folks’s methods tens of 1000’s of occasions a day, it not less than offered some minimal bar that needed to be crossed first, earlier than the attacker might start to attempt to convert hashes into their associated plaintext passwords. And as soon as hackers had tremendous elevated admin entry, actually what might they not do? They may do something that was programmatically doable on the compromised system, together with merely get rid of the necessity to use passwords in any respect. It’s recreation over!
Kerberoasting
However it turns on the market are not less than two, if no more, strategies a hacker can use to acquire somebody’s password hash with out being tremendous elevated. The primary is called Kerberoasting. With Kerberoasting, an attacker, with entry on a Microsoft Energetic Listing community, can use any common person account and extract the password hashes of any account with a Kerberos service principal identify (SPN). The definition of an SPN will not be essential. Simply know that lots of the most elevated accounts (e.g., service accounts) have SPNs, which implies an attacker breaking in as any sort of regular person (on a Home windows community) can typically simply get the password hashes for a number of elevated accounts, and from there, rapidly take over the remainder of the community.
This isn’t a theoretical danger. It’s executed by actual world hackers every single day. It’s executed by skilled penetration testers every single day. It’s executed by ransomware gangs every single day. It was not so frequent again in 2017 when NIST issued their official password coverage recommendation. It was identified do it (e.g., Kerberoasting) again then, however nearly nobody did it and there was not practically as many instruments to do it. At the moment, many hacking teams routinely do it and there are dozens of instruments and scripts devoted to doing it. Colloquially, it’s youngster’s play.
However not less than with Kerberoasting, the attacker must compromise not less than one common person account first to start the assault. There may be one other password hash theft methodology that doesn’t require that the attacker have first compromised every other account and may be carried out remotely over the Web. The creator of this text first wrote about this real-world password hash assault in 2019.
Captured Password Hashes through E-mail
In a nutshell, an attacker can craft a malicious URL hyperlink, current it to a person, and if the person clicks on it, it’s going to typically lead the sufferer’s electronic mail consumer or browser to show the person’s password hash. The attacker can then take the hash and crack it again to the person’s plaintext password. No particular privileges wanted. The attacker doesn’t even have to be on the sufferer’s community. The attacker can ship a simple-looking electronic mail, which if the sufferer clicks on, it causes their password’s hash to be despatched to the attacker.
Once I first wrote about this assault, which had already been round in the true world for just a few years, it was not utilized in the true world a lot. It was used, however actually solely by a handful of hackers and even then, pretty sparingly. Since 2019, it has turn out to be talked about in an increasing number of real-world assaults, together with these:
That is to say that it’s not a rarified assault, if it ever was.
As a result of folks’s password hashes may be obtained extra simply than ever, particularly on Home windows gadgets and networks, any group that wishes to have what the pc safety world considers “sturdy” laptop safety, ought to create passwords that are resistant in opposition to password hash cracking assaults. Meaning 12-character or longer completely random passwords or 20-character or longer human-created passwords. And since nobody actually needs to must create and use a bunch of actually lengthy passwords, we advocate utilizing phishing-resistant MFA and/or password managers every time you’ll be able to.
That’s it. That is the explanation for our suggestion of 20-character or longer passwords when created and utilized by a human. Something shorter simply will not be safe sufficient, particularly if you’re engaged on a Home windows system or community. Possibly in the future Microsoft will make it far harder for his or her password hashes to be stolen and cracked within the first place (and they’re attempting, but it surely takes a very long time to vary a giant ship’s course).
Be happy to ship any questions or feedback it’s important to rogerg@knowbe4.com
E-Ebook: What Your Password Coverage Ought to Be
 On this e-book, Roger A. Grimes, KnowBe4’s Knowledge-Pushed Protection Evangelist, particulars the professionals and cons of password use. Roger explains how the implementation of supporting frameworks, akin to MFA and password managers, may help you retain your group locked down.
On this e-book, Roger A. Grimes, KnowBe4’s Knowledge-Pushed Protection Evangelist, particulars the professionals and cons of password use. Roger explains how the implementation of supporting frameworks, akin to MFA and password managers, may help you retain your group locked down.
Obtain this e-book to study:
- What techniques unhealthy actors use to hack passwords (and keep away from them)
- The professionals and cons of password managers and multi-factor authentication and the way they affect your danger
- How you can craft a safe password coverage that addresses the commonest strategies of password assault
- How you can empower your finish customers to turn out to be your greatest final line of protection
PS: Do not wish to click on on redirected buttons? Reduce & Paste this hyperlink in your browser:
https://information.knowbe4.com/wp-password-policy-should-be

%20(1).jpg#keepProtocol)

