The speedy transfer to hybrid work led to by the pandemic drove the adoption of Zero Belief Community Entry (ZTNA) as a option to securely join customers with the functions that they should get work completed from anyplace. Nevertheless, as I described in my first article, preliminary implementations of ZTNA have been deeply flawed.
In my earlier submit, I talked about how the ZTNA 1.0 idea of “enable and ignore” is a recipe for catastrophe. This idea maintains that when a connection is established, all consumer and gadget conduct for that session is trusted implicitly and goes unchecked. Sadly, one other limitation of the “enable and ignore” method is that it prohibits safety inspection of the site visitors.
ZTNA 1.0 Lacks Safety Inspection
As a result of the “enable and ignore” mannequin lacks safety inspection, there isn’t a means for a ZTNA 1 .0 answer to detect any malicious or different compromised site visitors and reply accordingly. This implies there aren’t any in-line controls to reveal and examine the site visitors payload and decide if something malicious or unknown is being launched. Likewise, there isn’t a mechanism to take motion by blocking site visitors, terminating the session, or reporting something uncommon, on the very least.
This turns ZTNA 1.0 right into a “security-through-obscurity-only” method, which additional places organizations, their customers, apps, and information liable to malware, compromised gadgets, and malicious site visitors.
ZTNA 2.0 Allows Steady Safety Inspection
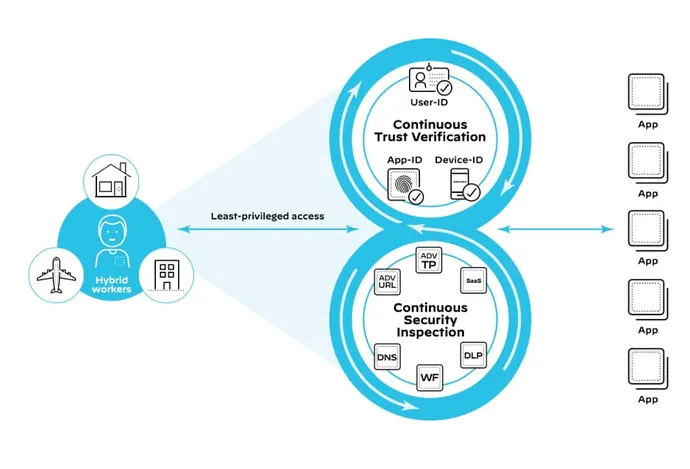
ZTNA 2.0, delivered by Prisma Entry, offers deep and ongoing inspection of all site visitors, to forestall all threats, together with zero-day threats. That is particularly essential in eventualities the place official consumer credentials have been stolen and used to launch assaults towards functions or infrastructure. ZTNA 2.0 provides full protections that safeguard towards even probably the most subtle threats, together with WildFire sandboxing, Superior URL Filtering, menace pPrevention, SaaS safety, DNS safety, and extra.
Our AI and ML-powered menace prevention applied sciences cease 95% of zero-day threats inline. This implies you don’t want a primary sufferer or have to attend for signatures to be up to date to be protected – your atmosphere is immediately protected.
The mixture of steady belief verification and steady safety inspection is a robust mannequin for delivering higher safety for right this moment’s hybrid workforces and overcoming a few of the shortcomings of ZTNA 1.0 options.
ZTNA 2.0 Is Zero Belief with Zero Exceptions
The shift to a dynamic, hybrid workforce mixed with direct-to-app entry has dramatically elevated the assault floor. Pursuing a real Zero Belief posture is one of the simplest ways to defend this new actuality, and making certain that safety inspection is performed in a sturdy and constant method is a vital step. That’s why steady safety inspection is a vital part of ZTNA 2.0.
Be sure you watch our ZTNA 2.0 digital occasion, the place we focus on improvements and greatest practices for securing the hybrid workforce with ZTNA 2.0.

Kumar Ramachandran serves as Senior Vice President of Merchandise for Safe Entry Service Edge (SASE) merchandise at Palo Alto Networks. Kumar co-founded CloudGenix in March 2013 and was its CEO, establishing the SD-WAN class. Previous to founding CloudGenix, Kumar held management roles in Product Administration and Advertising and marketing for the multi-billion greenback department routing and WAN optimization companies at Cisco. Previous to Cisco, he managed functions and infrastructure for corporations reminiscent of Citibank and Providian Monetary. Kumar holds an MBA from UC Berkeley Haas College of Enterprise and a Grasp’s in Laptop Science from the College of Bombay.


