A sniffing assault in system hacking is a type of denial-of-service assault which is carried out by sniffing or capturing packets on the community, after which both sending them repeatedly to a sufferer machine or replaying them again to the sender with modifications. Sniffers are sometimes utilized in system hacking as a instrument for analyzing site visitors patterns in a state of affairs the place performing extra intrusive and damaging assaults wouldn’t be fascinating.
Sniffing Assault:
A sniffing assault may also be utilized in an try and get better a passphrase, comparable to when an SSH personal key has been compromised. The sniffer captures SSH packets containing encrypted variations of the password being typed by the consumer at their terminal, which may then be cracked offline utilizing brute drive strategies.
- The time period “sniffing” is outlined in RFC 2301 as: “Any act of capturing community site visitors and replaying it, often for the aim of espionage or sabotage.”
- This definition shouldn’t be correct for UNIX-based methods, since any site visitors will be sniffed so long as both the attacker has entry to community interfaces (NIC) or modifies packets that might not be altered in transit. Sniffing will be carried out utilizing a particular program like tcpdump, tcpflow, or LanMon that’s linked to a port over which the packets will be inspected remotely.
- One other sniffing assault known as ARP spoofing entails sending solid Deal with Decision Protocol (ARP) messages to the Ethernet information hyperlink layer. These messages are used to affiliate a sufferer machine’s IP deal with with a unique MAC deal with, main the focused machine to ship all its site visitors meant for the sufferer via an attacker-controlled host.
- That is used to each hijack classes and in addition trigger flooding of the community through a denial-of-service assault (see Smurf assault).
Each IP packet incorporates, along with its payload, two fields: an IP header, and an Ethernet header encapsulating it. - The mixture of those two headers is sometimes called a “packet” by those that work with web communications. An attacker can, subsequently, view and modify an IP packet’s IP header with out having to see its payload.
- The Ethernet header incorporates details about the vacation spot MAC deal with (the {hardware} deal with of the recipient machine) and the Ether Kind discipline incorporates a price indicating what sort of service is requested (e.g., priority or circulate management).
- The Ether sort could possibly be “0xFFFF”, indicating that no service fields have been included for the Ethernet body. This was utilized in Cisco’s implementation previous to model 8.0.
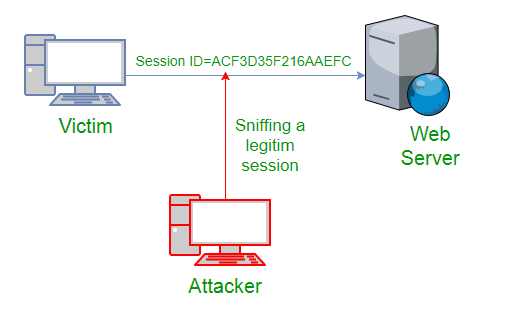
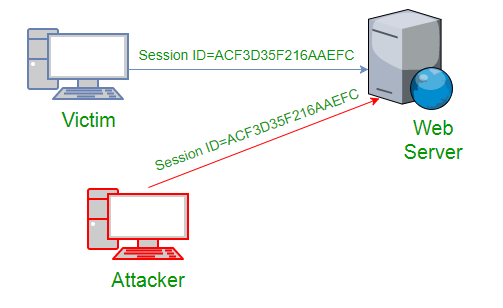
Key Factors:
There are a selection of various strategies that an attacker can use to carry out ARP spoofing. They embody:
- The attacker has entry to the “ARP cache” on their contaminated machine, which additionally incorporates different machines’ MAC addresses, however who don’t have or should not utilizing the identical IP addresses as different machines with the identical MAC addresses of their ARP caches.
- The attacker doesn’t know what methodology the opposite machines use for preserving a desk of MAC addresses, and so merely units up a community with many duplicate entries.
- The attacker sends out solid ARP messages, attempting to affiliate their contaminated machine with one other machine’s MAC deal with.
Countermeasures:
There are a selection of ways in which the attacker will be prevented from utilizing these strategies, together with:
- ARP spoofing shouldn’t be a really efficient assault, besides in networks which might be poorly secured.
- To ensure that an attacker to make use of this methodology as a type of masquerading, they have to be capable of ship packets on to the community (both via entry to Wi-Fi or by discovering a safety flaw). Due to this, the attacker’s IP deal with is more likely to change into identified in a short time.
- A sniffing assault is a type of assault the place the attacker tries to entry sure information over the community and sniffing is used as an important activity in capturing information. The time period “sniffing” comes from the motion of sniffing or smelling. The attacker will get maintain of this info through the use of particular software program known as “community analyzer”.
- Sniffing in Hacking: it’s thought-about to be an intrusion in your laptop system with out permission, with out your data, and with out authorized authorization. It’s known as hacking, which will be carried out by a number of strategies.
Conclusion:
In conclusion, it may be stated that sniffing is a technique used to extract info from the community with a purpose to get entry to a system or to disclaim entry.


