The web of issues (IoT) is a catch-all time period for the rising variety of electronics that are not conventional computing units, however are related to the web to ship information, obtain directions or each.
There’s an extremely broad vary of ‘issues’ that fall underneath the IoT umbrella: Web-connected ‘sensible’ variations of conventional home equipment akin to fridges and lightweight bulbs; devices that would solely exist in an internet-enabled world akin to Alexa-style digital assistants; and internet-enabled sensors which are reworking factories, healthcare, transportation, distribution facilities and farms.
What’s the web of issues?
The IoT brings web connectivity, information processing and analytics to the world of bodily objects. For customers, this implies interacting with the worldwide data community with out the middleman of a keyboard and display (Alexa, for instance).
In enterprise settings, IoT can carry the identical efficiencies to manufacturing processes and distribution programs that the web has lengthy delivered to data work. Billions of embedded internet-enabled sensors worldwide present an extremely wealthy set of knowledge that firms can use to enhance the protection of their operations, monitor property and cut back handbook processes.
Knowledge from machines can be utilized to foretell whether or not tools will break down, giving producers advance warning to stop lengthy stretches of downtime. Researchers also can use IoT units to assemble information about buyer preferences and conduct, although that may have severe implications for privateness and safety.
How massive is the IoT?
In a phrase: monumental. Priceonomics breaks it down: There have been greater than 50 billion IoT units in 2020, and people units generated 4.4 zettabytes of knowledge. (A zettabyte is a trillion gigabytes.) By comparability, in 2013 IoT units generated a mere 100 billion gigabytes. The sum of money to be made within the IoT market is equally staggering; estimates on the worth of the market in 2025 vary from $1.6 trillion to $14.4 trillion.
In its International IoT Market Forecast, IoT Analytics Analysis predicts there will likely be 27 billion energetic IoT connections (excluding computer systems, laptops, telephones, cellphones and tablets) by 2025. Nevertheless, the corporate did decrease its forecast based mostly on the continued chip scarcity, which it expects to influence the variety of related IoT units past 2023.
How does the IoT work?
The primary component of an IoT system is the machine that gathers information. Broadly talking, these are internet-connected units, so that they every have an IP deal with. They vary in complexity from autonomous cell robots and forklifts that transfer merchandise round manufacturing facility flooring and warehouses, to easy sensors that monitor the temperature or scan for fuel leaks in buildings.
In addition they embrace private units akin to health trackers that monitor the variety of steps people take every day.
Within the subsequent step within the IoT course of, collected information is transmitted from the units to a gathering level. Transferring the information will be performed wirelessly utilizing a variety of applied sciences or over wired networks. Knowledge will be despatched over the web to a knowledge middle or the cloud. Or the switch will be carried out in phases, with middleman units aggregating the information, formatting it, filtering it, discarding irrelevant or duplicative information, then sending the vital information alongside for additional evaluation.
The ultimate step, information processing and analytics, can happen in information facilities or the cloud, however generally that’s not an possibility. Within the case of essential units akin to shutoffs in industrial settings, the delay of sending information from the machine to a distant information middle is just too nice. The round-trip time for sending information, processing it, analyzing it and returning directions (shut that valve earlier than the pipes burst) can take too lengthy.
In such instances edge computing can come into play, the place a wise edge machine can mixture information, analyze it and trend responses if mandatory, all inside comparatively shut bodily distance, thereby decreasing delay. Edge units even have upstream connectivity for sending information to be additional processed and saved.
A rising variety of edge computing use instances, akin to autonomous automobiles that must make split-second selections, is accelerating the event of edge applied sciences that may course of and analyze information instantly with out going to the cloud.
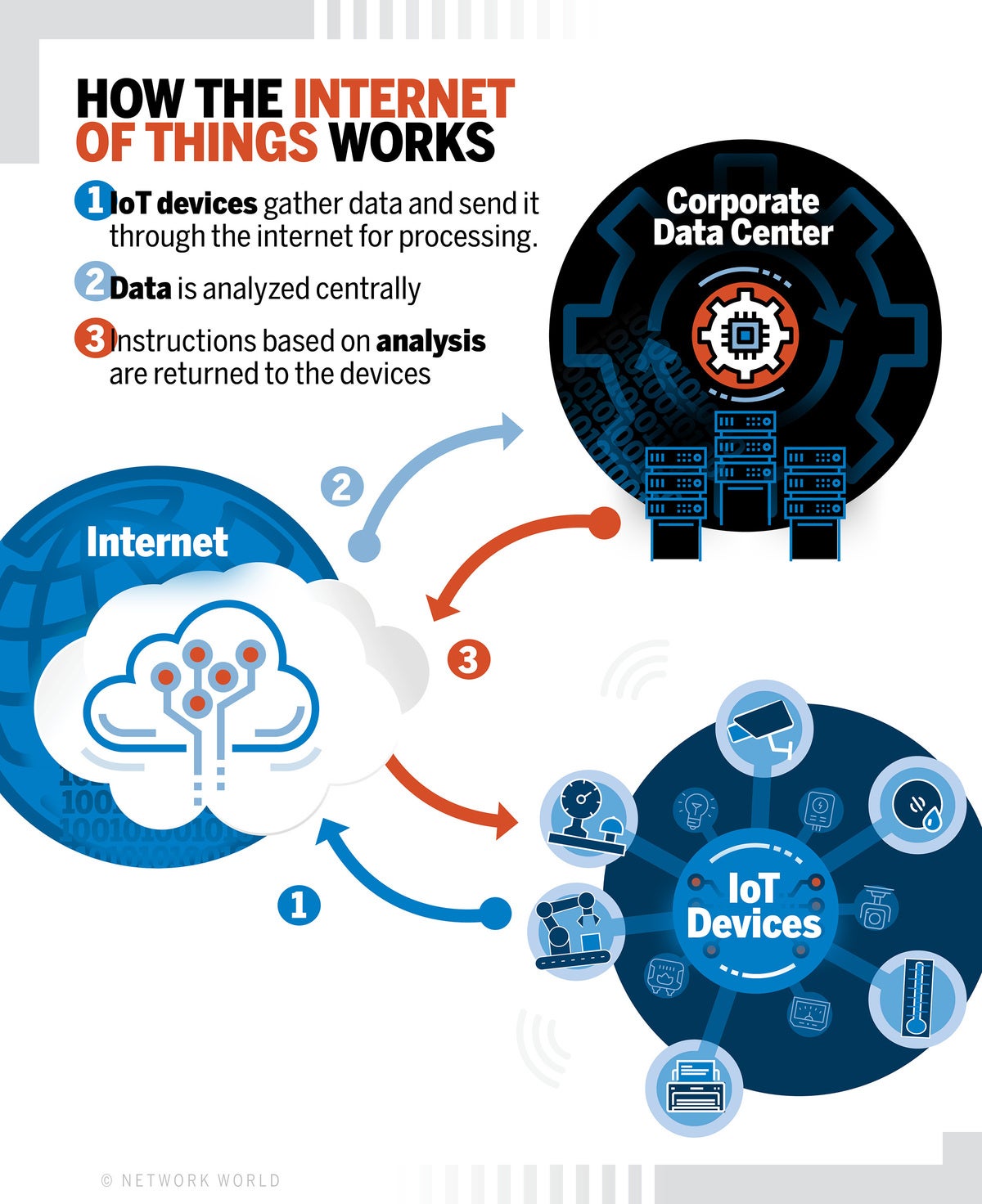 Community World / IDG
Community World / IDGHow the web of issues works.
Examples of IoT units
Basically, any machine that may collect and transmit details about the bodily world can take part within the IoT ecosystem. Good residence home equipment, RFID tags, and industrial sensors are a number of examples. These sensors can monitor a variety of things together with temperature and strain in industrial programs, standing of essential components in equipment, affected person very important indicators, the usage of water and electrical energy, amongst many, many different prospects.
Manufacturing unit robots will be thought-about IoT units, in addition to autonomous automobiles and robots that transfer merchandise round industrial settings and warehouses. Municipalities exploring sensible metropolis ecosystems are utilizing IoT and machine-to-machine (M2M) sensors to allow functions akin to visitors monitoring, avenue gentle administration, and crime prevention by means of digital camera feeds.
Different examples embrace health wearables and residential safety programs. There are additionally extra generic units, just like the Raspberry Pi or Arduino, that allow you to construct your personal IoT endpoints. Regardless that you would possibly consider your smartphone as a pocket-sized pc, it could properly even be beaming information about your location and conduct to back-end providers in very IoT-like methods.
IoT machine administration
To be able to work collectively, all these units should be authenticated, provisioned, configured, and monitored, in addition to patched and up to date as mandatory. Too typically, all this occurs inside the context of a single vendor’s proprietary programs – or, it does not occur in any respect, which is much more dangerous. However the business is beginning to transition to a standards-based machine administration mannequin, which permits IoT units to interoperate and can make sure that units aren’t orphaned.
IoT communication requirements and protocols
When IoT devices discuss to different units, they’ll use all kinds of communication requirements and protocols, many tailor-made to units with restricted processing capabilities or low energy consumption. A few of these you have undoubtedly heard of — Wi-Fi or Bluetooth, for example — however many extra are specialised for the world of IoT. ZigBee, for instance, is a wi-fi protocol for low-power, short-distance communication, whereas message queuing telemetry transport (MQTT) is a publish/subscribe messaging protocol for units related by unreliable or delay-prone networks. (See Community World’s glossary of IoT requirements and protocols.)
The elevated speeds and bandwidth of 5G mobile networks are anticipated to learn IoT. In its International IoT Market Forecast, IoT Analytics Analysis predicted a compounded annual development price (CAGR) of 159% for 5G-based IoT units from 2021 by means of 2025.
IoT, edge computing and the cloud
![Network World - How Edge Computing Works [diagram]](https://images.idgesg.net/images/article/2017/09/nw_how_edge_computing_works_diagram_1400x1717-100736111-large.jpg?auto=webp&quality=85,70) Community World / IDG
Community World / IDGHow edge computing permits IoT.
For a lot of IoT programs, the stream of knowledge is coming in quick and livid, which has given rise to a brand new know-how class referred to as edge computing, which consists of home equipment positioned comparatively near IoT units, fielding the move of knowledge from them. These machines course of that information and ship solely related materials again to a extra centralized system for evaluation. As an example, think about a community of dozens of IoT safety cameras. As an alternative of bombarding the constructing’s safety operations middle (SoC) with simultaneous live-streams, edge-computing programs can analyze the incoming video and solely alert the SoC when one of many cameras detects motion.
And the place does that information go as soon as it’s been processed? Nicely, it’d go to your centralized information middle, however as a rule it would find yourself within the cloud. The elastic nature of cloud computing is nice for IoT situations the place information would possibly are available in intermittently or asynchronously.
Cloud distributors supply IoT platforms
The cloud giants (Microsoft, Amazon, Google) try to promote greater than only a place to stash the information your sensors have collected. They’re providing full IoT platforms, which bundle collectively a lot of the performance to coordinate the weather that make up IoT programs. In essence, an IoT platform serves as middleware that connects the IoT units and edge gateways with the functions you utilize to take care of the IoT information. That mentioned, each platform vendor appears to have a barely completely different definition of what an IoT platform is, the higher to distance themselves from the competitors.
IoT and Huge Knowledge analytics
Think about a situation the place folks at a theme park are inspired to obtain an app that gives details about the park. On the similar time, the app sends GPS indicators again to the park’s administration to assist predict wait instances in strains. With that data, the park can take motion within the brief time period (by including extra workers to extend the capability of some sights, for example) and the long run (by studying which rides are essentially the most and least well-liked on the park).
The theme park instance is small potatoes in comparison with many real-world IoT data-harvesting operations. Many massive information operations use data harvested from IoT units, correlated with different information factors, to get perception into human conduct.
For instance, X-Mode launched a map based mostly on monitoring location information of people that partied at spring break in Ft. Lauderdale in March of 2020, even because the coronavirus pandemic was gaining velocity in the US, exhibiting the place all these folks ended up throughout the nation. The map was stunning not solely as a result of it confirmed the potential unfold of the virus, but in addition as a result of it illustrated simply how intently IoT units can monitor us. (For extra on IoT and analytics, click on right here.)
IoT and AI
The amount of knowledge IoT units can collect is much bigger than any human can take care of in a helpful method, and positively not in actual time. We have already seen that edge computing units are wanted simply to make sense of the uncooked information coming in from the IoT endpoints. There’s additionally the necessity to detect and take care of information that is perhaps simply plain fallacious.
Many IoT suppliers are providing machine studying and synthetic intelligence capabilities to make sense of the collected information. IBM’s Watson platform, for example, will be educated on IoT information units to provide helpful ends in the sphere of predictive upkeep — analyzing information from drones to tell apart between trivial injury to a bridge and cracks that want consideration, for example. In the meantime, Arm has introduced low-power chips that may present AI capabilities on the IoT endpoints themselves. The corporate additionally launched new IoT processors, such because the Cortex-M85 and Corstone-1000 that helps AI on the edge.
IoT and enterprise functions
Enterprise makes use of for IoT embrace holding monitor of shoppers, stock, and the standing of vital parts. Listed here are 4 industries which have been remodeled by IoT:
- Oil and fuel: Remoted drilling websites will be higher monitored with IoT sensors than by human intervention.
- Agriculture: Granular information about crops rising in fields derived from IoT sensors can be utilized to extend yields.
- HVAC: Local weather management programs throughout the nation will be monitored by producers.
- Brick-and-mortar retail: Clients will be micro-targeted with gives on their telephones as they linger in sure components of a retailer.
Extra typically, enterprises are in search of IoT options that may assist in 4 areas: vitality use, asset monitoring, safety, and buyer expertise.
Industrial IoT
The IIoT is a subset of the Web of Issues made up of related sensors and instrumentation for equipment within the transport, vitality, and industrial sectors. The IIoT consists of a number of the most well-established sectors of the IoT market, together with the descendants of some units that predate the IoT moniker. IIoT units are sometimes longer-lived than most IoT endpoints – some stay in service for a decade or extra – and in consequence could use legacy, proprietary protocols and requirements that make it troublesome to maneuver to fashionable platforms.
Client IoT
The transfer of IoT into shopper units is more moderen however far more seen to peculiar folks. Related units vary from health wearables that monitor our actions to internet-enabled thermometers. Most likely essentially the most distinguished IoT shopper product is the house assistant, akin to Amazon Alexa or Google Dwelling.
IoT safety and vulnerabilities
IoT units have earned a nasty status in terms of safety. PCs and smartphones are “normal use” computer systems designed to final for years, with advanced, user-friendly OSes that now have automated patching and security measures inbuilt.
IoT units, against this, are sometimes primary devices with stripped-down OSes. They’re designed for particular person duties and minimal human interplay, and can’t be patched, monitored or up to date. As a result of many IoT units are finally operating a model of Linux underneath the hood with varied community ports out there, they make tempting targets for hackers.
Maybe nothing demonstrated this greater than the Mirai botnet, which was created by a young person telnetting into residence safety cameras and child screens that had easy-to-guess default passwords, and which ended up launching one in all historical past’s largest DDoS assaults.