Password safety is just as sturdy because the password itself. Sadly, we are sometimes reminded of the hazard of weak, reused, and compromised passwords with main cybersecurity breaches that begin with stolen credentials. For instance, in Might 2022, the favored wedding ceremony planning website, Zola, was the sufferer of a major cybersecurity breach the place hackers used an assault referred to as credential stuffing. It resulted in fraudulent exercise tied to buyer accounts. Let us take a look at the Zola breach and why it emphasizes the necessity for organizations to bolster their password safety and shield towards varied kinds of password assaults.
What occurred with the Zola assault?
As a substitute of going after Zola’s core business-critical infrastructure, hackers went after buyer accounts with the Might assault. Attackers used an age-old approach known as credential stuffing to compromise a number of Zola buyer accounts. With entry to the compromised accounts, they tried to buy present vouchers which they might then use.
A Zola spokesperson talked about that round 3,000 accounts, or round .1 % of Zola accounts, have been compromised. Customers noticed lots of of {dollars} value of present playing cards or financial presents taken from their accounts. Hackers even modified the e-mail related to customers’ Zola accounts in lots of instances, stopping them from logging in. Compromised Zola accounts have been shortly positioned on the market on the darkish internet. Different customers reported fraudulent expenses on bank cards related to Zola accounts.
Emily Forrest, Zola Director of Communications, talked about the next in an announcement concerning the compromise:
“These hackers probably gained entry to these set of uncovered credentials on third-party websites and used them to attempt to log in to Zola and take dangerous actions. Our crew jumped into motion instantly to make sure that all {couples} and visitors on Zola are protected…We perceive the disruption and stress that this induced a few of our {couples}, however we’re pleased to report that every one tried fraudulent money fund switch makes an attempt have been blocked. All money funds have been restored.”
As a part of their remediation of the assault, Zola, along with forcing customers to reset their account passwords, quickly disabled cellular apps related to the platform. They’ve since reactivated the cellular app platforms. Nonetheless, though Zola permits connecting checking account data to Zola accounts, they nonetheless don’t require multi-factor authentication as a part of their safety provisions.
What went mistaken from a safety perspective with the Zola assault?
Hindsight is commonly 20/20 relating to autopsy evaluation of cybersecurity breaches. Nonetheless, there have been many issues that would have been completed and could be completed shifting ahead to stop assaults just like the Zola hack from being carried out.
Extra firms now require multi-factor authentication to be enabled in your account to make the most of their providers. Arguably, any service geared towards gathering cash into an account or that permits connecting a checking account or bank card ought to require multi-factor. With multi-factor enabled, even when an attacker has legit credentials, corresponding to a username and password, with an extra issue required, they nonetheless don’t have every little thing wanted to authenticate and log in.
The assault on Zola helps underscore that firms should additionally monitor accounts for suspicious actions. For instance, expecting suspicious geolocations, the variety of logins from a single supply, or different metrics can assist establish and remediate nefarious actions.
What’s credential stuffing?
Credential stuffing is a hacking approach that has been round a protracted whereas and performs upon the weak spot of password reuse amongst end-users. It’s outlined as the automated injection of stolen username and password pairs. What does this imply? It’s human nature to reuse passwords throughout a number of websites, providers, and purposes. This method makes it simpler to recollect logins throughout varied platforms. Hackers use this logic to defeat password authentication used throughout most platforms. In the event that they compromise or discover leaked credentials related to a consumer/e mail/password mixture in a single platform, they will strive the identical credentials throughout a number of platforms.
It may be efficient even when they do not know the consumer/e mail tackle has an account related. For instance, suppose they will entry a number of compromised credential units (usernames, passwords). In that case, they are going to probably discover legitimate consumer accounts throughout a number of providers the place customers have used the identical username/password mixture.
Notice the next alarming statistics associated to credential reuse:
- Some 50% of IT professionals admitted to reusing passwords on work accounts
- There was a surprisingly larger share of IT staff reusing credentials than non-privileged customers (39% comparatively)
- In a research that spanned three months, Microsoft discovered that some 44 million of its customers had used the identical password on multiple account
- In a 2019 Google research, they discovered that 13% of individuals reuse the identical password throughout all accounts, 52% % use the identical one for a number of on-line accounts, and solely 35% use a distinct password for each account
One other alarming state of affairs that organizations should think about is that end-users might use the identical passwords for his or her company Lively Listing environments as they do for his or her private accounts. Whereas companies cannot management and implement password insurance policies for end-users private accounts, monitoring for breached passwords and password reuse throughout their company Lively Listing infrastructure is essential.
Defending Lively Listing towards breached passwords and password reuse
On-premises Lively Listing Area Providers (AD DS) doesn’t have built-in safety towards breached passwords or password reuse. For instance, suppose each single account in Lively Listing has the identical password, and the password meets the configured password coverage. In that case, there is no such thing as a notification or approach to forestall this with native Lively Listing Password Coverage performance.
Furthermore, many organizations are federating Lively Listing Area Providers on-premises with Single Signal-On (SSO) cloud options. Sadly, it means all the weak passwords, breached passwords, and passwords reused throughout your group are actually federated to be used with cloud providers, additional weakening your safety posture.
Constructed-in Lively Listing Password Insurance policies cannot shield you towards:
- Incremental passwords
- Leetspeak passwords
- Simply guessed however “advanced” passwords
- Breached passwords
- Passwords related to your enterprise or business
Bolster Lively Listing password safety with Specops
With the shortcomings of built-in capabilities supplied by Lively Listing Area Providers (AD DS), organizations must bolster their Lively Listing password safety utilizing a third-party answer. Specops Password Coverage is a strong answer that gives companies with the instruments and capabilities required to extend their password safety and general cybersecurity stance.
Specops Password Coverage seamlessly integrates with current Lively Listing Password Insurance policies and provides lacking password safety features to assist shield your group from many assaults, together with credential stuffing. Notice the next key options supplied by Specops Password Coverage:
- You’ll be able to create customized dictionary lists to dam phrases frequent to your group
- Stop using greater than 2 billion compromised passwords with Specops Breached Password Safety
- Discover and take away compromised passwords in your atmosphere
- Customers get informative messaging from Specops at failed password modifications, decreasing calls to the helpdesk
- Actual-time, dynamic suggestions at password change with the Specops Authentication consumer
- Size-based password expiration with customizable e mail notifications
- Block consumer names, show names, particular phrases, consecutive characters, incremental passwords, reusing a part of a password
- Granular, GPO-driven concentrating on for any GPO stage, laptop, consumer, or group inhabitants
- Passphrase help
- Over 25 languages supported
- Use Common Expressions for extra granular password insurance policies
Organizations can begin defending their consumer’s passwords with Breached Password Safety with just some clicks within the Specops Password Coverage configuration settings. With the constantly verify for leaked passwords and drive customers to vary them setting, you possibly can leverage Specop Password Coverage’s enhanced honeypot intelligence for probably the most late-breaking breached passwords obtainable.
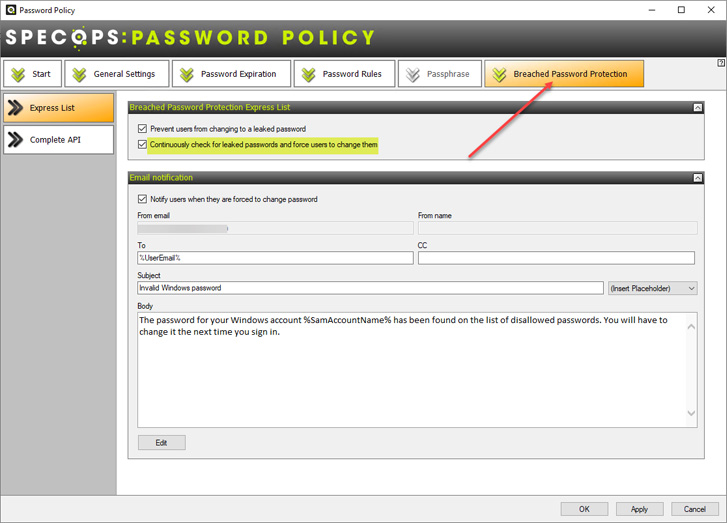 |
| Configuring Specops Password Coverage Breached Password Safety |
Specops gives the instruments wanted to fight password dangers corresponding to reused passwords simply.
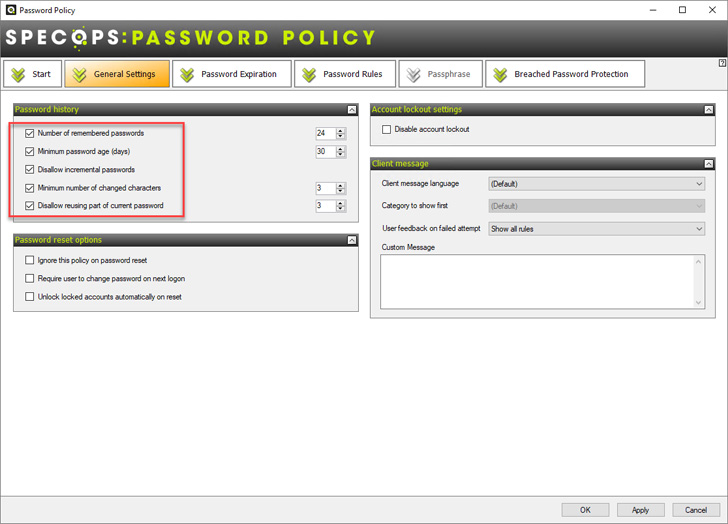 |
| Stopping incremental passwords and requiring a minimal variety of modifications to an current password |
Wrapping Up
The Zola hack helps to emphasise the significance of stopping customers from reusing passwords in business-critical environments. It results in credential stuffing, password guessing, breached passwords, and plenty of different kinds of password assaults. Specops Password Coverage is a strong software permitting organizations to successfully forestall password reuse, incremental passwords, and a minimal variety of modifications to current passwords on the subsequent password change.


