Disclaimer: This text is supposed to present perception into cyber threats as seen by the neighborhood of customers of CrowdSec.
What can tens of hundreds of machines inform us about unlawful hacker actions?
Do you do not forget that scene in Batman – The Darkish Knight, the place Batman makes use of a system that aggregates lively sound information from numerous cell phones to create a meta sonar feed of what’s going on at any given place?
It’s an attention-grabbing analogy with what we do at CrowdSec. By aggregating intrusion indicators from our neighborhood, we will supply a transparent image of what’s going on by way of unlawful hacking on the planet.
After 2 years of exercise and analyzing 1 million intrusion indicators day by day from tens of hundreds of customers in 160 nations, we begin having an correct “Batman sonar” world feed of cyber threats. And there are some attention-grabbing takeaways to stipulate.
A cyber menace with many faces
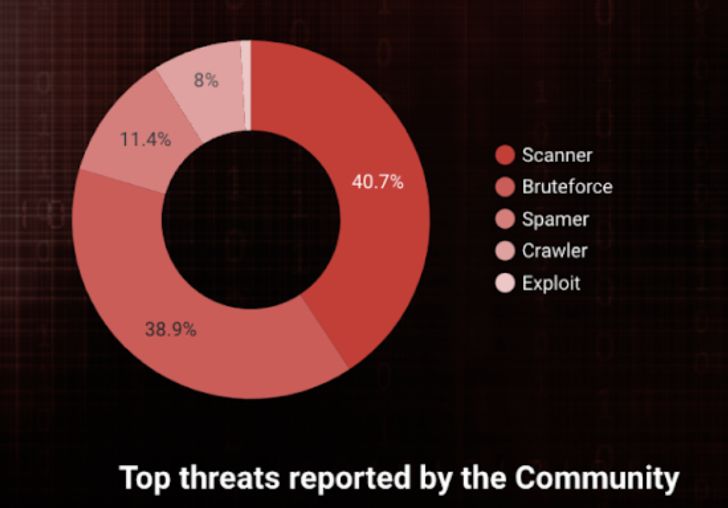
To start with, the worldwide cyber menace is extremely versatile. What can we see when trying on the varieties of assaults reported, their origin, and the Autonomous Techniques (AS) behind the malicious IP addresses?
Scanners and Brute pressure makes an attempt are nonetheless the most well-liked intrusion vectors our neighborhood sees and rank #1. Fairly logic, as surveillance is step one to a extra superior intrusion. The scanning actions seen by our neighborhood are principally port scans or HTTP-based probings.
Amongst the totally different intrusion sorts utilized by hackers, brute pressure makes an attempt on delicate providers (SSH, electronic mail, admin URLs, and so on.) is #2. Not breakthrough data, however when research present that brute pressure assaults are accounted for six% of cyber assaults on the planet, it’s not stunning to see it as dominant, particularly since it’s nonetheless one of many best and most cost-effective ones to automate and deploy (hey script kiddies). As a result of it’s fairly simple to counter, one would assume it hardly ever works, however hey, 6%!
Log4J continues to be not but a accomplished deal
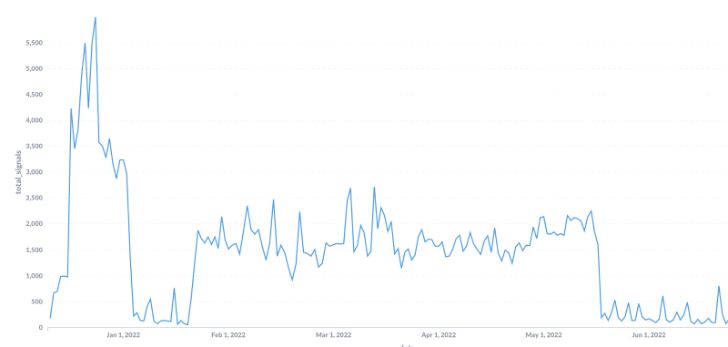
Amongst the most well-liked exploit makes an attempt our neighborhood sees, now we have Log4j. You certainly loved final 12 months’s storm on how a easy open-source logging utility for Apache with a vulnerability took over the cybersecurity world and precipitated countless complications to cybersecurity consultants. And, after all, the felony world was very happy to take advantage of it with automated scanning bots searching for weak providers.
Effectively, our neighborhood has witnessed the storm. As soon as the December peak following the disclosure handed, issues calmed down a little bit bit, however scanning actions for Log4j began once more, though at a decrease however fixed stage, fueled by bots.
The important thing message is that should you assume you might be protected as a result of the “advertising” storm handed, assume twice.
There’s nonetheless a really aggressive exercise trying to make use of the vulnerability.
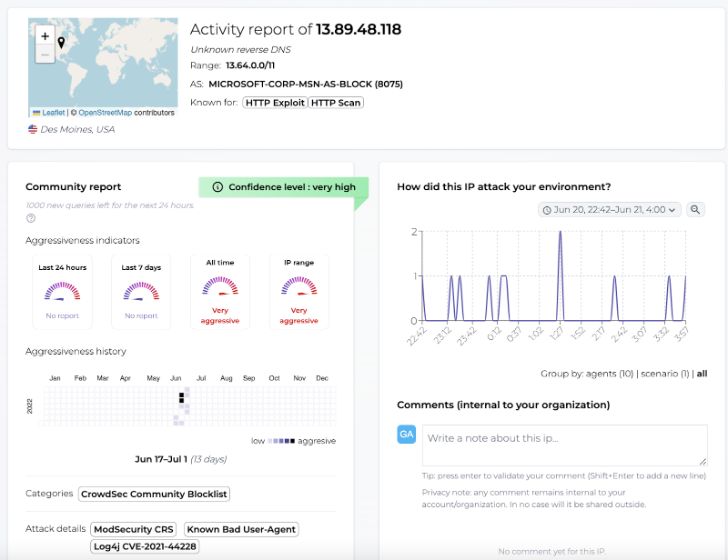
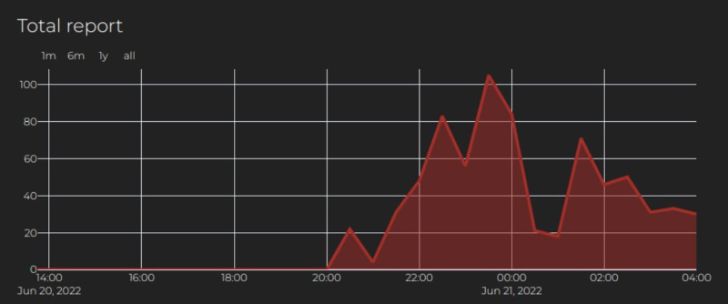
As an illustration, a few weeks in the past, a big spectrum of our neighborhood was scanned because the IP deal with 13.89.48.118 was reported by greater than 500 customers in lower than 12 hours. It joined 20000+ different IP addresses on the neighborhood blocklist for remediation.
IP addresses: cyber criminals’ core useful resource
IP addresses are hardly ever malevolent ceaselessly and their fame can change from at some point to a different. With the neighborhood continuously sharing data on them, any replace could be instantaneously transferred to customers. In the long term, it offers invaluable information on the aggressiveness period of IP addresses.
This can be a snapshot of the variety of IP addresses that landed within the CrowdSec information lakes (flagged as malicious). What’s attention-grabbing to notice is that cybercriminals are certainly altering the IPs they’re utilizing to commit their assaults:
* solely 2,79% of those are everlasting members of our database
* 12,63% of all collected IPs change each single week
* The day by day renewal charge sits at 1.8%
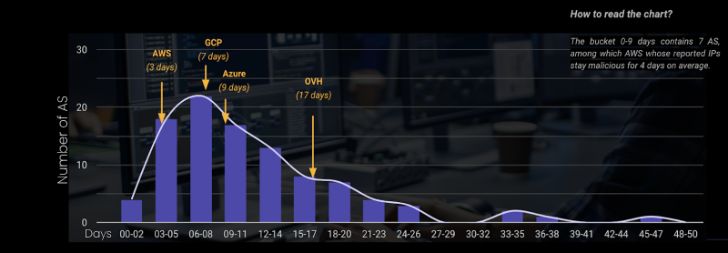
**Autonomous methods have totally different approaches to mitigating compromised IPs**
Every IP is a part of a pool of addresses managed by an AS (Autonomous System). An AS is an intensive community or group of networks which have a unified routing coverage. Each pc or machine that connects to the Web is linked to an AS. Usually, every AS is operated by a single massive group, equivalent to an Web service supplier (ISP), a big enterprise expertise firm, a college, or a authorities company, and is, as such, liable for the IP addresses.
Every aggressive IP shared by the CrowdSec neighborhood is enriched by its AS. This, mixed with the information on aggressiveness period, can present a transparent image of how AS handle compromised IPs.
Whereas trying merely on the variety of compromised property is likely to be an angle, it would not be essentially honest. Not all operators are equal in dimension, and a few are internet hosting “riskier” providers (hey outdated PHP CMS) than others.
The typical malevolent period of all of the IPs in the identical AS signifies the operator’s due diligence in figuring out and coping with compromised property. The distribution of the common period is proven with arrows pointing to the place of probably the most reported AS for the main cloud suppliers. As an illustration, at AWS, compromised addresses stay compromised for a median of three days. Azure 9 days. On the finish of the chart, AS from China or Russia (shock…) “are much less fast” to behave upon compromised IPs.
This text is supposed to present an outline of the menace exercise and intelligence CrowdSec customers see day by day. Please seek the advice of the total model of the report right here if you would like extra particulars.