Organizations and safety groups work to guard themselves from any vulnerability, and sometimes do not understand that danger can be introduced on by configurations of their SaaS apps that haven’t been hardened. The newly revealed GIFShell assault methodology, which happens by Microsoft Groups, is an ideal instance of how risk actors can exploit official options and configurations that have not been appropriately set. This text takes a take a look at what the strategy entails and the steps wanted to fight it.
The GifShell Assault Technique
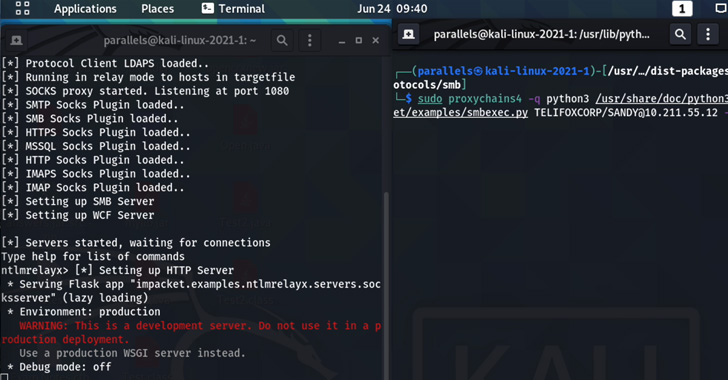
Found by Bobby Rauch, the GIFShell assault method permits dangerous actors to use a number of Microsoft Groups options to behave as a C&C for malware, and exfiltrate information utilizing GIFs with out being detected by EDR and different community monitoring instruments. This assault methodology requires a tool or consumer that’s already compromised.
The primary element of this assault permits an attacker to create a reverse shell that delivers malicious instructions through base64 encoded GIFs in Groups, and exfiltrates the output by GIFs retrieved by Microsoft’s personal infrastructure.
How does it work?
- To create this reverse shell, an attacker should first compromise a pc to plant the malware — which suggests the dangerous actor must persuade the consumer to put in a malicious stager, like with phishing, that executes instructions and uploads command output through a GIF url to a Microsoft Groups internet hook.
- As soon as the stager is in place, the risk actor creates their very own Microsoft Groups tenant and contacts different Microsoft Groups customers outdoors of the group.
- The risk actor can then use a GIFShell Python script to ship a message to a Microsoft Groups consumer that incorporates a specifically crafted GIF. This official GIF picture has been modified to incorporate instructions to execute on a goal’s machine.
- When the goal receives the message, the message and the GIF will probably be saved in Microsoft Staff’s logs. Necessary to notice: Microsoft Groups runs as a background course of, so the GIF doesn’t even have to be opened by the consumer to obtain the attacker’s instructions to execute.
- The stager screens the Groups logs and when it finds a GIF, it extracts and runs the instructions.
- Microsoft’s servers will join again to the attacker’s server URL to retrieve the GIF, which is known as utilizing the base64 encoded output of the executed command.
- The GIFShell server working on the attacker’s server will obtain this request and mechanically decode the information permitting the attackers to see the output of the command run on the sufferer’s machine.
Microsoft’s response
As reported by Lawrence Abrams in BleepingComputer, Microsoft agrees that this assault methodology is an issue, nonetheless, it “doesn’t meet the bar for an pressing safety repair.” They “might take motion in a future launch to assist mitigate this method.” Microsoft is acknowledging this analysis however asserting that no safety boundaries have been bypassed.
Whereas Rauch claims that certainly “two further vulnerabilities found in Microsoft Groups, an absence of permission enforcement and attachment spoofing”, Microsoft argues, “For this case… these all are put up exploitation and depend on a goal already being compromised.” Microsoft is asserting that this method is utilizing official options from the Groups platform and never one thing they’ll mitigate at present.
In accordance with Microsoft’s assertions, certainly that is the problem many organizations face — there are configurations and options that risk actors can exploit if not hardened. Just a few adjustments to your tenant’s configurations can forestall these inbound assaults from unknown Groups tenants.
The way to Shield In opposition to the GIFShell Assault
There are safety configurations inside Microsoft that, if hardened, may help to stop the sort of assault.
1 — Disable Exterior Entry: Microsoft Groups, by default, permits for all exterior senders to ship messages to customers inside that tenant. Many group admins doubtless usually are not even conscious that their group permits for Exterior Groups collaboration. You’ll be able to harden these configurations:
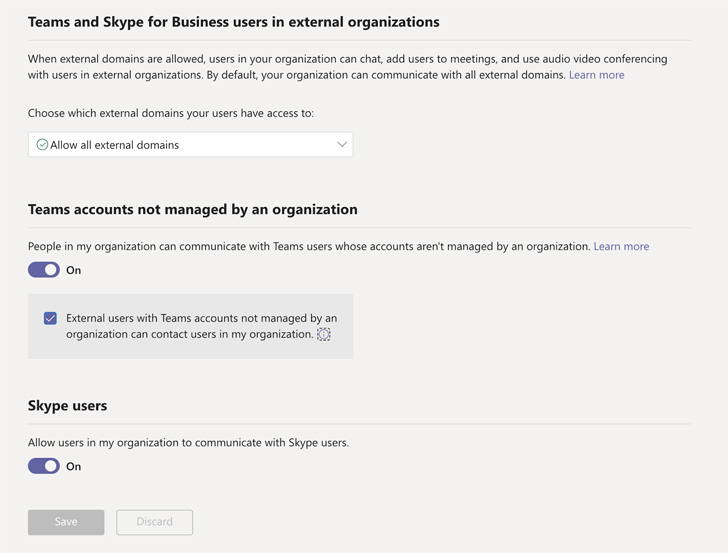 |
| Determine 1: Microsoft Groups Exterior Entry Configurations |
- Disable exterior area entry — Forestall folks in your group from discovering, calling, chatting, and establishing conferences with folks exterior to your group in any area. Whereas not as seamless of a course of as by Groups, this higher protects the group and is price the additional effort.
- Disable unmanaged exterior groups begin dialog — Block Groups customers in your group from speaking with exterior Groups customers whose accounts usually are not managed by a company.
2 — Achieve Gadget Stock Perception: You’ll be able to guarantee your whole group’s units are absolutely compliant and safe through the use of your XDR / EDR / Vulnerability Administration answer, like Crowdstrike or Tenable. Endpoint safety instruments are your first line of protection in opposition to suspicious exercise resembling accessing the machine’s native groups log folder which is used for information exfiltration in GIFShell.
You’ll be able to even go a step additional and combine an SSPM (SaaS Safety Posture Administration) answer, like Adaptive Defend, together with your endpoint safety instruments to realize visibility and context to simply see and handle the dangers that stem from a lot of these configurations, your SaaS customers, and their related units.
The way to Automate Safety In opposition to These Assaults
There are two strategies to fight misconfigurations and harden safety settings: guide detection and remediation or an automatic SaaS Safety Posture Administration (SSPM) answer. With the multitudes of configurations, customers, units, and new threats, the guide methodology is an unsustainable drain on sources, leaving safety groups overwhelmed. Nevertheless, an SSPM answer, resembling Adaptive Defend, permits safety groups to realize full management over their SaaS apps and configurations. The suitable SSPM automates and streamlines the method of monitoring, detection and remediation for SaaS misconfigurations, SaaS-to-SaaS entry, SaaS associated IAM, and Gadget-to-SaaS consumer danger in compliance with each business and firm requirements.
In instances such because the GifShell assault methodology, Adaptive Defend’s misconfiguration administration options permits safety groups to repeatedly assess, monitor, determine and alert for when there’s a misconfiguration (see determine 1). Then they’ll rapidly remediate by the system or use a ticketing system of option to ship the pertinent particulars for quick remediation.
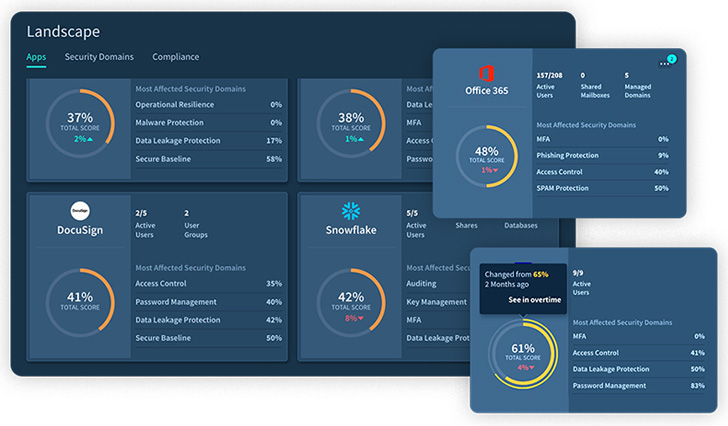 |
| Determine 2. Panorama View of SaaS App Hygiene |
Equally, Adaptive Defend’s Gadget Stock characteristic (seen in determine 2) can monitor units getting used company-wide and flag any Gadget-to-SaaS danger whereas correlating that data with the consumer roles and permissions and the SaaS apps in use. This permits safety groups to realize a holistic view of user-device posture to guard and safe high-risk units that may function a essential risk of their SaaS setting.
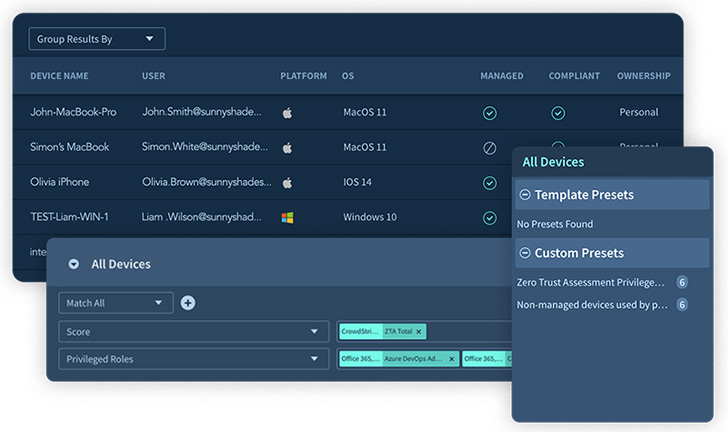 |
| Determine 3. Gadget Stock |
Be taught extra about how the Adaptive Defend SSPM can shield your SaaS app ecosystem.