Simply earlier than final Christmas, in a first-of-a-kind case, JPMorgan was fined $200M for workers utilizing non-sanctioned functions for speaking about monetary technique. No point out of insider buying and selling, bare shorting, or any malevolence. Simply staff circumventing regulation utilizing, nicely, Shadow IT. Not as a result of they tried to obfuscate or conceal something, just because it was a handy device that they most popular over every other sanctioned merchandise (which JPMorgan actually has fairly a number of of.)
Visibility into unknown and unsanctioned functions has been required by regulators and likewise advisable by the Heart for Web Safety group for a very long time. But it looks as if new and higher approaches are nonetheless in demand. Gartner has recognized Exterior Assault Floor Administration, Digital Provide Chain Threat, and Id Risk Detection as the highest three developments to concentrate on in 2022, all of that are intently intertwined with Shadow IT.
“Shadow IDs,” or in different phrases, unmanaged worker identities and accounts in third-party providers are sometimes created utilizing a easy email-and-password-based registration. CASBs and company SSO options are restricted to a couple sanctioned functions and usually are not broadly adopted on most web sites and providers both. This implies, that a big a part of a corporation’s exterior floor –in addition to its consumer identities– could also be utterly invisible.
Above all, these Shadow IDs stay unmanaged even after staff go away the group. This may occasionally end in unauthorized entry to delicate buyer knowledge or different cloud-based providers. Worker-created, however business-related identities are unseen for many IDM/IAM instruments additionally. The graveyard of forgotten accounts belonging to ex-employees or deserted functions is rising on daily basis, to infinity.
And typically, the lifeless rise from their graves, as with the Joint Fee On Public Ethics, whose legacy system was breached this yr, regardless that it has been out of use since 2015. They rightfully notified their legacy customers as a result of they perceive that password reuse might stretch over a number of years, and based on Verizon, stolen credentials are nonetheless the highest contributor to all kinds of breaches and assaults. So when Shadow IDs are left behind, they create an eternal threat unseen and unmanaged by anybody.
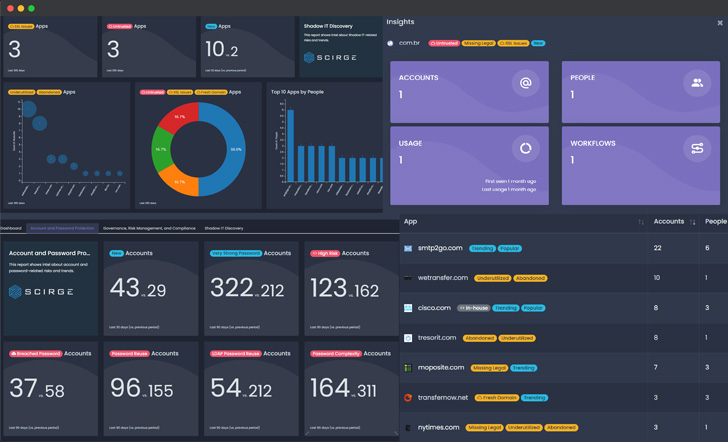
How you can Report on Shadow IT and Shadow IDs?
Sadly, community monitoring misses the mark, as these instruments are designed to filter malicious site visitors, present knowledge leakage safety and create category-based guidelines for looking. Nevertheless, they’re utterly blind to precise logins, and thus can not differentiate looking, personal accounts, and company software signups, (or phishing websites for that matter). To find and handle Shadow IDs and Shadow IT, there must be software and account-level monitoring in place, that may create a trusted, international supply of fact throughout the group.
Discovering these belongings by way of monitoring business-related credential utilization on any web site permits a unified view of unsanctioned or undesirable functions. Inventories of apps and accounts present visibility of the true scope of exterior providers and identities used throughout the group. Additionally, they permit the reviewing of third-party suppliers about their insurance policies, safety and authentication measures, and the way they’re managing and sustaining your knowledge.
It’s inconceivable to correctly categorize all the quarter-million new domains which can be registered every day throughout the globe, so monitoring people who present up on our endpoints is the proper strategy. As a side-effect, revealing logins on suspicious or new apps will give visibility into profitable phishing assaults that weren’t prevented on a gateway or client-side, and the place staff gave away vital credentials.
Scirge is a browser-based device that gives full visibility into Shadow IDs and Shadow IT, password hygiene for company and third-party enterprise net accounts, and even real-time worker training and consciousness. And it additionally has a totally free model for auditing your cloud footprint, so you may get an instantaneous view of the extent of Shadow IT amongst your staff.