In the case of on-line safety, firewalls are a necessary instrument for shielding knowledge and networks from malicious cyberattacks. A firewall is a system designed to regulate entry between networks, computer systems, and different programs.
Firewall guidelines are an necessary a part of this safety system, as they decide which community visitors might be allowed to move via the firewall and which visitors might be blocked. By having a transparent set of firewall guidelines, companies can defend their programs from potential threats whereas permitting reliable customers to entry the companies they want.
What Are Firewall Guidelines?
Firewall guidelines are directions that management how a firewall machine handles incoming and outgoing visitors. They’re entry management mechanisms that implement safety in networks by blocking or permitting communication based mostly on predetermined standards. These standards embrace supply or vacation spot IP addresses, ports, protocols, and companies.
Relying on the sort of firewall, the principles might also dictate which customers or teams have entry to particular purposes or the place sure knowledge is allowed to journey inside the community. For the rule to be efficient, it have to be explicitly outlined and enabled within the firewall configuration.
How Do Firewall Guidelines Work?
A firewall evaluates every incoming and outgoing knowledge packet towards the firewall guidelines. If the packet matches one of many guidelines, the firewall permits the packet to move via to its vacation spot. In any other case, it rejects and (if programmed to) stories it.
Firewall guidelines are configured as entry management lists (ACLs), that are ordered lists of permissions defining visitors allowed or denied. A typical ACL contains an motion (permit, deny, or reject) adopted by circumstances or parameters visitors should meet earlier than the motion is utilized.
To make sure safety, firewalls typically use a “deny by default” coverage, which means that any visitors that doesn’t explicitly meet the factors specified by the firewall guidelines might be denied.
For a quite simple instance, you might need a rule that claims, “Permit any visitors from IP handle X to port Y.” When a packet arrives on the firewall, the firewall reads its supply and vacation spot. If the packet’s supply is X and its vacation spot Y, it passes via. If, then again, its supply is Z—or if its supply is unidentified—and vacation spot is Y, it’s denied.
The place Are Firewall Guidelines Usually Saved?
Firewall guidelines are saved in a firewall configuration file containing the principles and settings for a given firewall. The configuration file often resides on the server working the firewall.
The configuration file is accessed and modified by the community administrator, who provides new guidelines or modifies current ones as wanted. These adjustments are then saved and utilized to the firewall, to allow them to take rapid impact. Relying on the kind of firewall, the principles could also be saved in several areas, comparable to a registry and even an exterior database.
Firewall Guidelines Sequence
Firewall guidelines are utilized top-down, which means the firewall begins with the primary rule created and runs via the complete sequence so as of creation. SANS Institute’s firewall guidelines recommends the next order when creating and organising firewall guidelines:
- Anti-spoofing filters, for blocked personal addresses and inside addresses showing from the skin.
- Consumer allow guidelines, comparable to “permit HTTP to public net server.”
- Administration allow guidelines, comparable to “SNMP traps a community administration server.”
- Noise drops, comparable to “discard OSPF and HSRP chatter.”
- Deny and alert, to alert system directors about visitors that’s suspicious.
- Deny and log, to log remaining visitors for evaluation.
Prime 10 Finest Practices for Firewall Guidelines
To make sure the most effective safety attainable, it’s necessary to observe sure greatest practices when configuring firewalls, together with documenting guidelines throughout units, monitoring firewall logs, and implementing least-privileged entry.
1. Doc firewall guidelines throughout a number of units
Doc all firewall rule configurations and guarantee these paperwork are up to date incessantly. This allows directors to evaluation the present setup and make any crucial adjustments if any threats or vulnerabilities are detected within the community’s safety.
Documentation clarifies why the rule exists and the challenges it solves. That manner, directors can rapidly assess whether or not or not the rule ought to stay lively, which helps restrict the chance of attackers discovering a loophole. It additionally serves as an audit path for compliance functions.
2. Implement a deny by default coverage
All the time begin with a deny by default coverage (often known as deny any/any), which means deny all visitors except explicitly allowed. This ensures new threats can not penetrate the community unidentified. It’s higher to by chance block some reliable visitors after which manually override than to permit via a doubtlessly devastating menace.
3. Monitor firewall logs
Commonly monitoring firewall logs is crucial to sustaining good community safety. Logging permits directors to trace visitors move all through the community, search for suspicious exercise, and troubleshoot issues. Monitoring firewall logs additionally offers perception into who’s utilizing the system and for what objective.
By monitoring exercise ranges, it’s simpler to see if there’s a sudden improve or lower in utilization, which may point out an assault has occurred. Relying on the complexity of the group’s infrastructure, logs from particular person parts of the system, comparable to routers, servers, and switches, could be aggregated into one centralized place for evaluation and alerting.
4. Group firewall guidelines to cut back complexity and maximize efficiency
Grouping firewall guidelines to simplify the rule construction is important to lowering complexity and optimizing the efficiency of a firewall. Grouping guidelines with related traits like supply or vacation spot addresses, protocols, ports, or companies will assist reduce the variety of guidelines required and make the general ruleset simpler to handle.
Moreover, segmenting the community into totally different zones and making use of firewall guidelines to every of these zones might help management visitors flows, scale back the probability of unintended publicity, and enhance the pace and efficiency of the firewall.
5. Configure application-level management
Configure firewalls to permit solely sure purposes and companies, comparable to net browsers and mail purchasers, versus each utility that makes an attempt to entry the community. This offers an extra layer of safety by proscribing what purposes can join with the community.
6. Use monitor mode
Monitor mode is a rule configuration that lets directors observe, however not block, community visitors earlier than making a firewall rule. It permits them to evaluation the present community visitors, determine and permit crucial visitors, and create guidelines to permit or deny further visitors.
When utilizing monitor mode, directors use IP addresses and ports to determine the visitors and guarantee it’s crucial. As soon as the visitors is recognized, directors can compile an inventory of supply IPs, vacation spot IPs, and vacation spot ports and start categorizing the visitors to create acceptable firewall guidelines.
7. Implement least-privileged entry
Limit consumer entry to the minimal privileges required to carry out their duties. This ensures that solely these customers who want entry to a specific service or useful resource can achieve it.
For instance, if a consumer doesn’t require FTP entry for his or her job duties, the administrator ought to configure the rule to stop it. This rule configuration limits the chance of each unintentional and intentional unauthorized entry to delicate data or sources.
8. Take away redundant firewall guidelines
Firewalls that haven’t been appropriately managed are likely to change into cluttered with redundant and pointless guidelines. Make sure that to usually examine for and take away any pointless or overlapping guidelines which may be clogging up the system and inflicting confusion.
9. Commonly evaluation the firewall guidelines
Similar to any safety measure, it’s important to maintain firewalls up-to-date with present threats. To do that, reviewing firewall guidelines and updating them usually is crucial. This contains guaranteeing all safety insurance policies stay constant and all threats are dealt with rapidly and successfully.
10. Block the next ports
SANS Institute’s firewall guidelines recommends blocking outbound visitors that makes use of the next ports:
| Service | Port | Port quantity |
| DNS Zone Transfers | TCP | 53 |
| TFTP Daemon | UDP | 69 |
| Hyperlink | TCP | 87 |
| BSD Unix | TCP | 512-514 |
| Small service | TCP and UDP | 20 and under |
| SMTP (besides exterior mail relays) | TCP | 25 |
| NetBIOS in Home windows NT | TCP and UDP | 135 |
| NetBIOS in Home windows NT | UDP | 137 and 138 |
| IMAP | TCP | 143 |
| LDAP | TCP and UDP | 389 |
| Syslog | UDP | 514 |
| Cisco AUX port | TCP | 2001 |
| Cisco AUX port (Stream) | TCP | 4001 |
| Cisco AUX port (binary) | TCP | 6001 |
| Frequent excessive order HTTP ports | TCP | 8000, 8080, and 8888 |
Blocking these ports might help scale back the chance of malicious exercise on a community by stopping unauthorized entry to sure companies. Moreover, many organizations block sure ports associated to on-line gaming and peer-to-peer (P2P) file sharing to reduce bandwidth utilization on their community.
5 Completely different Sorts of Firewall Guidelines
Relying on the kind of safety system in place, there could also be many various kinds of firewall guidelines that may apply. A number of the commonest firewall guidelines embrace:
- Entry guidelines: These guidelines move, block, or reject sure sorts of visitors based mostly on the supply and vacation spot addresses, protocol, and port quantity.
- Community handle translation (NAT) guidelines: NAT guidelines translate IP addresses from one community to a different, permitting for simpler visitors routing between networks. It can be used to safe personal networks from exterior threats.
- Stateful packet filtering: This firewall rule inspects every packet that passes via the firewall and retains monitor of the connection state. It compares the packet’s data with the prevailing connection state and permits or denies the packet based mostly on that comparability.
- Utility stage gateways: Also referred to as proxy servers, these act as gatekeepers between the web and an inside community. Proxy servers function on the utility layer 7 of the OSI mannequin. They defend the interior community by controlling entry to the exterior networks. Community admins can use them to limit entry to sure web sites, block sure sorts of content material, or restrict the units allowed to entry the community.
- Circuit-level gateways: These firewalls work on the OSI community mannequin’s session layer 5, the place connections are established and maintained. Circuit-level gateways are answerable for authenticating incoming TCP and IP packets and permitting or denying visitors based mostly on the configured guidelines.
An Instance of a Firewall Rule
Firewall rulesets could be configured to dam or permit visitors based mostly on standards comparable to supply handle, supply port, vacation spot handle, vacation spot port, and a sign of whether or not the visitors needs to be permitted or denied.
| Supply handle | Supply port | Vacation spot handle | Vacation spot port | Motion |
| 192.168.1.2 | 80 | 10.10.10.20 | 22 | Permit |
| 10.10.0.0/24 | Any | 192.168.0.0/24 | 443 | Deny |
| Any | Any | Any | Any | Deny |
The above instance firewall guidelines would allow visitors from 192.168.1.2 on port 80 to 10.10.10.20 on port 22, whereas denying visitors from 10.10.0.0/24 to 192.168.0.0/24 on port 443 and denying any incoming visitors from any supply handle and port.
By defining a algorithm, directors can management which visitors is allowed and which visitors is blocked, thus offering an extra layer of safety to their community.
8 Steps to Create Firewall Rule in pfSense
pfSense is an open-source firewall and router distribution based mostly on FreeBSD. It’s designed to be a firewall, digital personal community (VPN), router, and wi-fi entry level (WAP). It helps many widespread community applied sciences comparable to IPv4, IPv6, OpenVPN, Snort, and pfBlockerNG. It’s primarily used as a firewall and router to safe networks in industrial and enterprise environments.
Right here’s the best way to create a firewall rule in pfSense.
Step 1: Log in to the pfSense net interface.
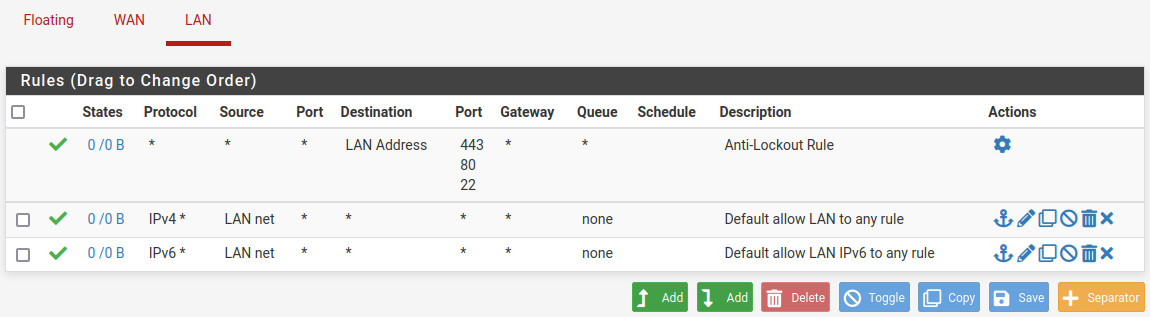
Step 2: Navigate to Firewall, then choose Guidelines.
Step 3: Choose the pfSense community machine (e.g., WAN or LAN machine) of your desire.
Step 4: Click on the Add button to create a brand new rule. The Add button on the left with the up arrow will create the rule on the prime of the listing, whereas the Add button on the suitable with the down arrow will create a rule on the backside of the listing.
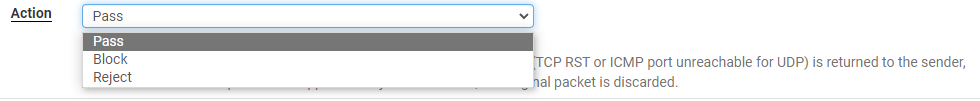
Step 5: Choose an motion to take when the rule is matched (move, block, reject).
- Cross means the rule will permit the visitors.
- Block means the rule will block the visitors from passing via.
- Reject means the rule will reject the visitors and ship again an error message.
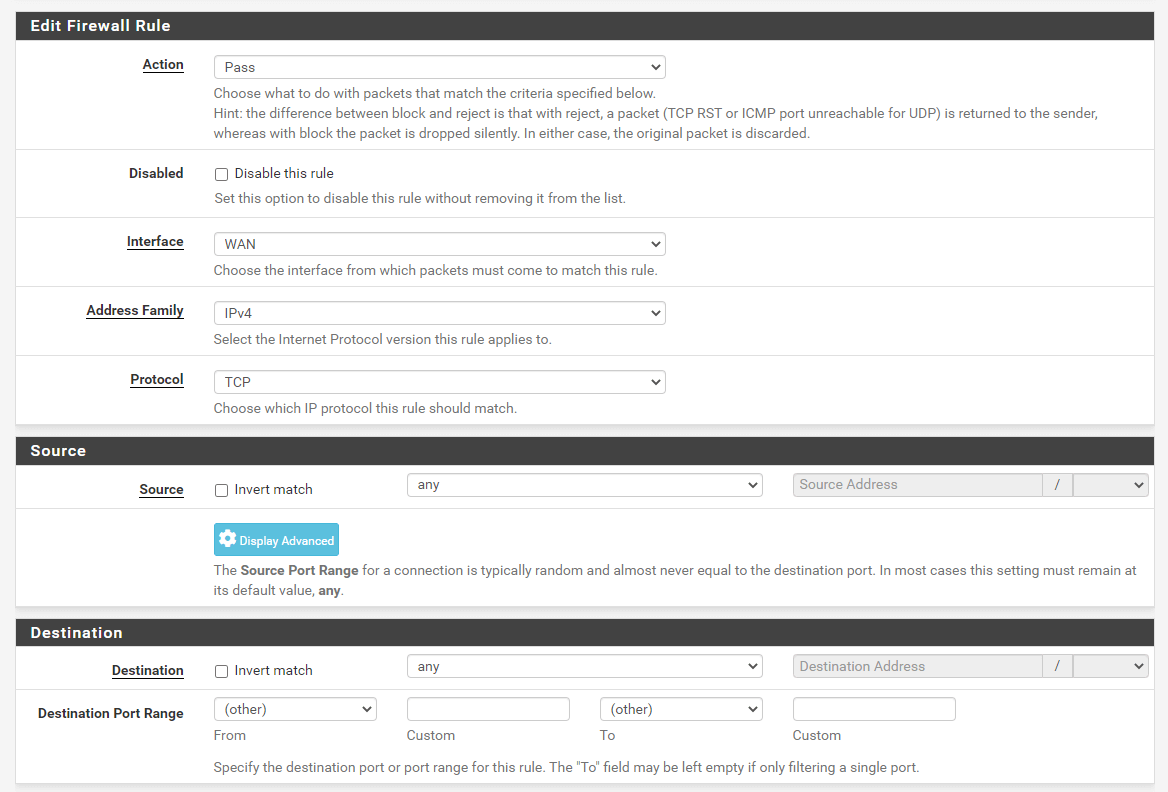
Step 6: Choose the suitable interface, protocol, and supply and vacation spot data.
- Interface: Select your most popular interface (e.g., WAN or LAN).
- Deal with household: Choose the right handle household: IPv4, IPv6, or each.
- Protocol: Choose the protocol you need to apply the rule to, comparable to TCP, UDP, or ICMP.
- Supply: Outline the visitors supply. It may be an IP handle, a community, PPPoE, or L2TPIP.
- Vacation spot: Much like the supply data, outline the vacation spot IP handle/vary.
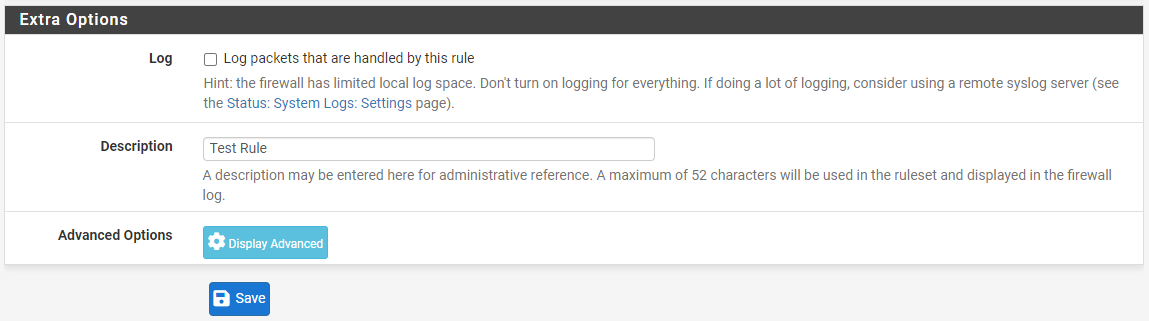
Step 7: Choose the suitable logging choices.
Step 8: Click on Save. The brand new rule ought to now be seen within the listing.
Backside Line: Bettering Your Safety With Firewall Guidelines
By understanding the various kinds of firewall guidelines and greatest practices for configuring them, you possibly can guarantee your enterprise networks are safe and functioning accurately. Take into account the particular wants of your group’s community and customers, and make sure the guidelines are configured accurately and consistent with trade requirements.
When creating firewall guidelines, it’s additionally important to contemplate their influence on general community efficiency. Too many restrictive guidelines may cause latency points, whereas overly permissive guidelines could create safety vulnerabilities. Be sure to take care when configuring firewall guidelines and usually evaluation them to make sure they continue to be updated.
Conventional firewalls are solely step one to a powerful safety posture on your community. A next-generation firewall will increase your safety throughout all layers.