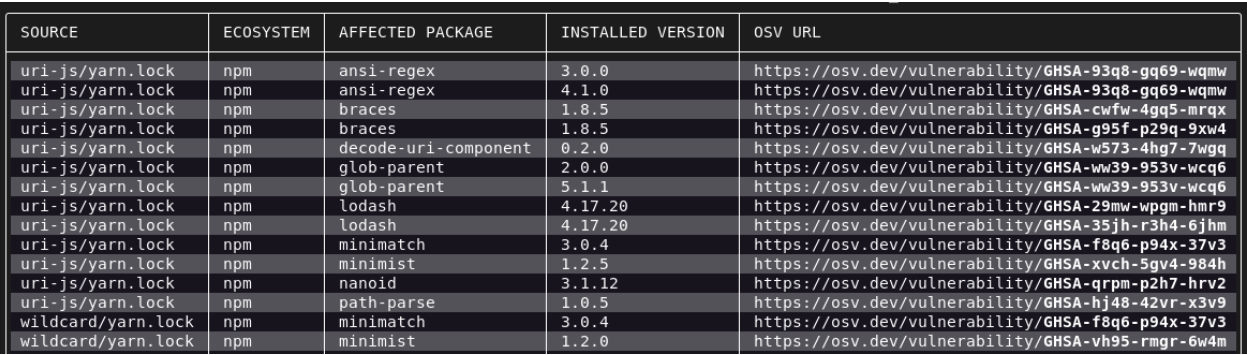
At present, we’re launching the OSV-Scanner, a free instrument that offers open supply builders quick access to vulnerability info related to their venture.
Final yr, we undertook an effort to enhance vulnerability triage for builders and shoppers of open supply software program. This concerned publishing the Open Supply Vulnerability (OSV) schema and launching the OSV.dev service, the primary distributed open supply vulnerability database. OSV permits all of the completely different open supply ecosystems and vulnerability databases to publish and eat info in a single easy, exact, and machine readable format.
The OSV-Scanner is the subsequent step on this effort, offering an formally supported frontend to the OSV database that connects a venture’s record of dependencies with the vulnerabilities that have an effect on them.
Software program initiatives are generally constructed on high of a mountain of dependencies—exterior software program libraries you incorporate right into a venture so as to add functionalities with out creating them from scratch. Every dependency probably comprises current identified vulnerabilities or new vulnerabilities that may very well be found at any time. There are just too many dependencies and variations to maintain observe of manually, so automation is required.
Scanners present this automated functionality by matching your code and dependencies towards lists of identified vulnerabilities and notifying you if patches or updates are wanted. Scanners convey unbelievable advantages to venture safety, which is why the 2021 U.S. Government Order for Cybersecurity included the sort of automation as a requirement for nationwide requirements on safe software program growth.
The OSV-Scanner generates dependable, high-quality vulnerability info that closes the hole between a developer’s record of packages and the knowledge in vulnerability databases. For the reason that OSV.dev database is open supply and distributed, it has a number of advantages as compared with closed supply advisory databases and scanners:
- Every advisory comes from an open and authoritative supply (e.g. the RustSec Advisory Database)
- Anybody can counsel enhancements to advisories, leading to a really top quality database
- The OSV format unambiguously shops details about affected variations in a machine-readable format that exactly maps onto a developer’s record of packages
- The above all ends in fewer, extra actionable vulnerability notifications, which reduces the time wanted to resolve them
Operating OSV-Scanner in your venture will first discover all of the transitive dependencies which might be being utilized by analyzing manifests, SBOMs, and commit hashes. The scanner then connects this info with the OSV database and shows the vulnerabilities related to your venture.
OSV-Scanner can also be built-in into the OpenSSF Scorecard’s Vulnerabilities test, which is able to lengthen the evaluation from a venture’s direct vulnerabilities to additionally embody vulnerabilities in all its dependencies. Which means that the 1.2M initiatives recurrently evaluated by Scorecard may have a extra complete measure of their venture safety.
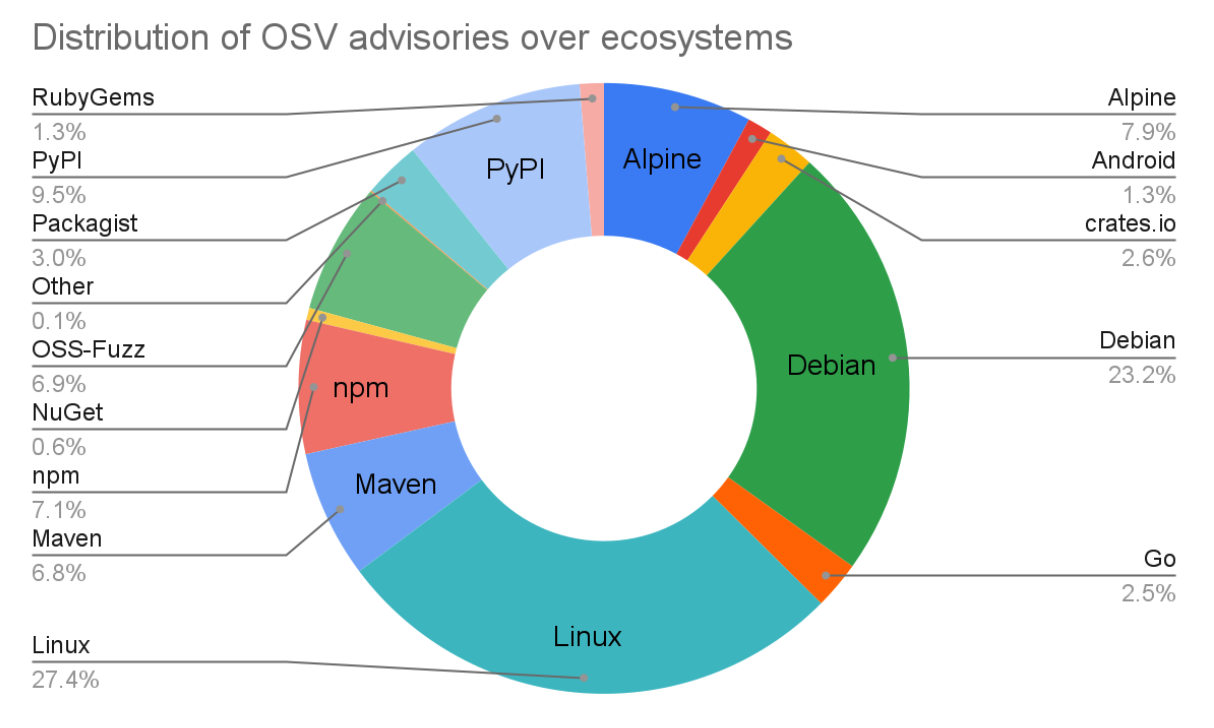
The OSV venture has made plenty of progress since our final submit in June final yr. The OSV schema has seen important adoption from vulnerability databases akin to GitHub Safety Advisories and Android Safety Bulletins. Altogether OSV.dev now helps 16 ecosystems, together with all main language ecosystems, Linux distributions (Debian and Alpine), in addition to Android, Linux Kernel, and OSS-Fuzz. This implies the OSV.dev database is now the largest open supply vulnerability database of its type, with a complete of over 38,000 advisories from 15,000 advisories a yr in the past.
The OSV.dev web site additionally had a whole overhaul, and now has a greater UI and supplies extra info on every vulnerability. Outstanding open supply initiatives have additionally began to depend on OSV.dev, akin to DependencyTrack and Flutter.
There’s nonetheless rather a lot to do! Our plan for OSV-Scanner isn’t just to construct a easy vulnerability scanner; we need to construct one of the best vulnerability administration instrument—one thing that may even decrease the burden of remediating identified vulnerabilities. Listed here are a few of our concepts for reaching this:
- Step one is additional integrating with developer workflows by providing standalone CI actions, permitting for simple setup and scheduling to maintain observe of recent vulnerabilities.
- Enhance C/C++ vulnerability help: One of many hardest ecosystems for vulnerability administration is C/C++, because of the lack of a canonical bundle supervisor to establish C/C++ software program. OSV is filling this hole by constructing a top quality database of C/C++ vulnerabilities by including exact commit degree metadata to CVEs.
- We’re additionally wanting so as to add distinctive options to OSV-Scanner, like the flexibility to make the most of particular operate degree vulnerability info by doing name graph evaluation, and to have the ability to routinely remediate vulnerabilities by suggesting minimal model bumps that present the maximal impression.
- VEX help: Robotically producing VEX statements utilizing, for instance, name graph evaluation.
You’ll be able to obtain and check out OSV-Scanner in your initiatives by following directions on our new web site osv.dev. Or alternatively, to routinely run OSV-Scanner in your GitHub venture, strive Scorecard. Please be happy to tell us what you assume! You can provide us suggestions both by opening a difficulty on our Github, or by means of the OSV mailing record.