One of many feedback I acquired after publishing the Use VRFs for VXLAN-Enabled VLANs claimed that:
I’m firmly of the assumption that VXLAN needs to be solely an entry layer/edge expertise and in case you are working your routing protocols inside the tunnel, you’ve already misplaced the plot.
That’s a fairly good guideline for typical information middle cloth deployments, however VXLAN is only a device that lets you construct multi-access Ethernet networks on high of IP infrastructure. You should use it to emulate E-LAN service or to construct networks just like what you may get with DMVPN (with none built-in safety). Immediately we’ll use it to construct a VRF Lite topology with two tenants (pink and blue).
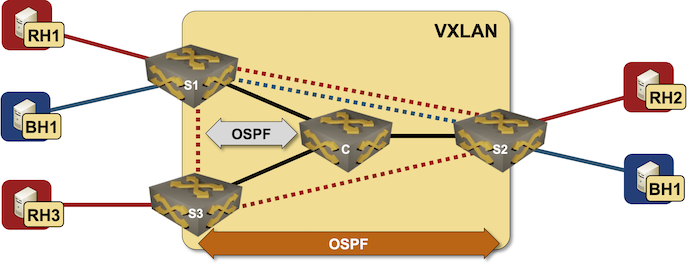
Lab topology
In our lab topology, we’ll outline two VRFs, two transport VLANs, and allow VXLAN transport for these VLANs (extra particulars in Creating VRF Lite Labs With netlab, VRF Lite Topology with VLAN Trunks and VXLAN Bridging Instance):
vrfs:
pink:
blue:
vlans:
red_transport:
vrf: pink
blue_transport:
vrf: blue
vxlan.vlans: [ red_transport, blue_transport ]
Subsequent, we’ll outline teams of gadgets:
- Linux hosts want no further configuration modules
- pe gadgets will run OSPF with the core gadgets and inside the VRFs. They can even want VXLAN transport.
- core gadgets run OSPF.
teams:
hosts:
members: [ rh1, rh2, rh3, bh1, bh2 ]
module: []
system: linux
pe:
module: [ vxlan,ospf ]
members: [ s1,s2,s3 ]
core:
members: [ c ]
module: [ ospf ]
Now for a trick: we’ll outline a bunch of PE-devices that gives companies to the pink tenant and one other group of PE-devices that gives companies to the blue tenant (extra particulars in VXLAN Router-on-a-Stick):
teams:
red_team:
module: [ vlan,vrf ]
members: [ s1, s2, s3 ]
vlans:
red_transport:
blue_team:
module: [ vlan,vrf ]
members: [ s1, s2 ]
vlans:
blue_transport:
Lastly, now we have to outline nodes and hyperlinks (you too can view the closing lab topology on GitHub).
nodes: [ rh1, rh2, rh3, bh1, bh2, s1, s2, s3, c ]
hyperlinks:
- s1-c
- s2-c
- s3-c
# Pink VRF
- rh1:
s1:
vrf: pink
- rh2:
s2:
vrf: pink
- rh3:
s3:
vrf: pink
# Blue VRF
- bh1:
s1:
vrf: blue
- bh2:
s2:
vrf: blue
Now we’re able to roll. Execute netlab up, watch for OSPF periods to be established, and discover the OSPF neighbors and routing tables on S1:
s1#sh ip ospf neighbor
Neighbor ID Occasion VRF Pri State Useless Time Handle Interface
10.0.0.9 1 default 0 FULL 00:00:31 10.1.0.1 Ethernet1
10.0.0.7 101 blue 0 FULL 00:00:33 172.16.1.7 Vlan1001
10.0.0.8 100 pink 1 FULL/DR 00:00:31 172.16.0.8 Vlan1000
10.0.0.7 100 pink 1 FULL/BDR 00:00:31 172.16.0.7 Vlan1000
s1#sh ip route vrf pink
VRF: pink
...
Gateway of final resort shouldn't be set
C 172.16.0.0/24 is straight related, Vlan1000
C 172.16.2.0/24 is straight related, Ethernet2
O 172.16.3.0/24 [110/20] by way of 172.16.0.7, Vlan1000
O 172.16.4.0/24 [110/20] by way of 172.16.0.8, Vlan1000
s1#sh ip route vrf blue
VRF: blue
...
Gateway of final resort shouldn't be set
C 172.16.1.0/24 is straight related, Vlan1001
C 172.16.5.0/24 is straight related, Ethernet3
O 172.16.6.0/24 [110/20] by way of 172.16.1.7, Vlan1001
For the 2 readers who haven’t put in netlab but: right here’s the Arista cEOS configuration for S1:
Cleaned-up Arista cEOS configuration for S1
vlan 1000
identify red_transport
!
vlan 1001
identify blue_transport
!
vrf occasion blue
rd 65000:2
!
vrf occasion pink
rd 65000:1
!
interface Ethernet1
description s1 -> c
no switchport
ip tackle 10.1.0.2/30
ip ospf community point-to-point
ip ospf space 0.0.0.0
!
interface Ethernet2
description s1 -> rh1 [stub]
no switchport
vrf pink
ip tackle 172.16.2.6/24
ip ospf community point-to-point
ip ospf space 0.0.0.0
!
interface Ethernet3
description s1 -> bh1 [stub]
no switchport
vrf blue
ip tackle 172.16.5.6/24
ip ospf community point-to-point
ip ospf space 0.0.0.0
!
interface Loopback0
ip tackle 10.0.0.6/32
ip ospf space 0.0.0.0
!
interface Management0
ip tackle 192.168.121.106/24
no lldp transmit
no lldp obtain
!
interface Vlan1000
description VLAN red_transport (1000) -> [s2,s3]
vrf pink
ip tackle 172.16.0.6/24
ip ospf space 0.0.0.0
!
interface Vlan1001
description VLAN blue_transport (1001) -> [s2]
vrf blue
ip tackle 172.16.1.6/24
ip ospf community point-to-point
ip ospf space 0.0.0.0
!
interface Vxlan1
vxlan source-interface Loopback0
vxlan udp-port 4789
vxlan vlan 1000 vni 101000
vxlan vlan 1001 vni 101001
vxlan vlan 1000 flood vtep 10.0.0.7 10.0.0.8
vxlan vlan 1001 flood vtep 10.0.0.7
!
ip routing
ip routing vrf blue
ip routing vrf pink
!
router ospf 1
router-id 10.0.0.6
max-lsa 12000
!
router ospf 100 vrf pink
router-id 10.0.0.6
interface unnumbered hey masks tx 0.0.0.0
passive-interface Ethernet2
max-lsa 12000
!
router ospf 101 vrf blue
router-id 10.0.0.6
interface unnumbered hey masks tx 0.0.0.0
passive-interface Ethernet3
max-lsa 12000
Need to run this lab by yourself, or attempt it out with totally different gadgets? No downside:

