Virtualization companies supplier VMware on Tuesday shipped updates to deal with 10 safety flaws affecting a number of merchandise that might be abused by unauthenticated attackers to carry out malicious actions.
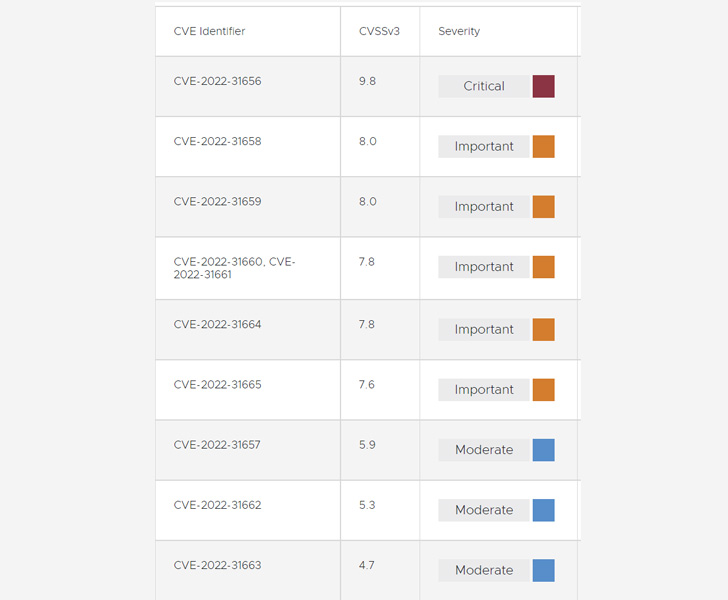
The problems tracked from CVE-2022-31656 by CVE-2022-31665 (CVSS scores: 4.7 – 9.8) have an effect on the VMware Workspace ONE Entry, Workspace ONE Entry Connector, Identification Supervisor, Identification Supervisor Connector, vRealize Automation, Cloud Basis, and vRealize Suite Lifecycle Supervisor.
Essentially the most extreme of the failings is CVE-2022-31656 (CVSS rating: 9.8), an authentication bypass vulnerability affecting native area customers that might be leveraged by a foul actor with community entry to acquire administrative entry.
Additionally resolved by VMware are three distant code execution vulnerabilities (CVE-2022-31658, CVE-2022-31659, and CVE-2022-31665) associated to JDBC and SQL injection that might be weaponized by an adversary with administrator and community entry.
Elsewhere, it has additionally remediated a mirrored cross-site scripting (XSS) vulnerability (CVE-2022-31663) that it stated is a results of improper person sanitization, which might result in the activation of malicious JavaScript code.
Rounding off the patches are three native privilege escalation bugs (CVE-2022-31660, CVE-2022-31661, and CVE-2022-31664) that allow an actor with native entry to escalate privileges to “root,” a URL injection vulnerability (CVE-2022-31657), and a path traversal bug (CVE-2022-31662).
Whereas profitable exploitation of CVE-2022-31657 makes it doable to redirect an authenticated person to an arbitrary area, CVE-2022-31662 might equip an attacker to learn recordsdata in an unauthorized method.
VMware stated it isn’t conscious of the exploitation of those vulnerabilities within the wild, however urged prospects utilizing the susceptible merchandise to apply the patches instantly to mitigate potential threats.