A vulnerability in Siemens Simatic programmable logic controller (PLC) may be exploited to retrieve the hard-coded, international personal cryptographic keys and seize management of the units.
“An attacker can use these keys to carry out a number of superior assaults towards Siemens SIMATIC units and the associated TIA Portal, whereas bypassing all 4 of its entry stage protections,” industrial cybersecurity firm Claroty mentioned in a brand new report.
“A malicious actor might use this secret data to compromise the whole SIMATIC S7-1200/1500 product line in an irreparable approach.”
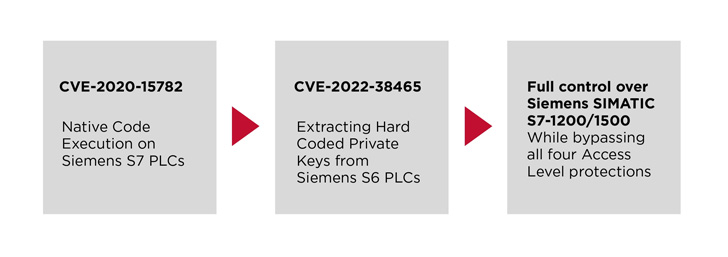
The vital vulnerability, assigned the identifier CVE-2022-38465, is rated 9.3 on the CVSS scoring scale and has been addressed by Siemens as a part of safety updates issued on October 11, 2022.
The record of impacted merchandise and variations is under –
- SIMATIC Drive Controller household (all variations earlier than 2.9.2)
- SIMATIC ET 200SP Open Controller CPU 1515SP PC2, together with SIPLUS variants (all variations earlier than 21.9)
- SIMATIC ET 200SP Open Controller CPU 1515SP PC, together with SIPLUS variants (all variations)
- SIMATIC S7-1200 CPU household, together with SIPLUS variants (all variations earlier than 4.5.0)
- SIMATIC S7-1500 CPU household, together with associated ET200 CPUs and SIPLUS variants (all variations earlier than V2.9.2)
- SIMATIC S7-1500 Software program Controller (all variations earlier than 21.9), and
- SIMATIC S7-PLCSIM Superior (all variations earlier than 4.0)
Claroty mentioned it was in a position to get learn and write privileges to the controller by exploiting a beforehand disclosed flaw in Siemens PLCs (CVE-2020-15782), permitting for the restoration of the personal key.
Doing so wouldn’t solely allow an attacker to override native code and extract the important thing, but additionally acquire full management over each PLC per affected Siemens product line.
CVE-2022-38465 mirrors one other extreme shortcoming that was recognized in Rockwell Automation PLCs (CVE-2021-22681) final yr and which might have enabled an adversary to remotely hook up with the controller, and add malicious code, obtain data from the PLC, or set up new firmware.
“The vulnerability lies in the truth that Studio 5000 Logix Designer software program could enable a secret cryptographic key to be found,” Claroty famous in February 2021.
As workarounds and mitigations, Siemens is recommending clients to make use of legacy PG/PC and HMI communications solely in trusted community environments and safe entry to TIA Portal and CPU to stop unauthorized connections.
The German industrial manufacturing firm has additionally taken the step of encrypting the communications between engineering stations, PLCs and HMI panels with Transport Layer Safety (TLS) in TIA Portal model 17, whereas warning that the “chance of malicious actors misusing the worldwide personal key as rising.”
The findings are the newest in a sequence of extreme flaws which have been found in PLCs. Earlier this June, Claroty detailed over a dozen points in Siemens SINEC community administration system (NMS) that may very well be abused to realize distant code execution capabilities.
Then in April 2022, the corporate unwrapped two vulnerabilities in Rockwell Automation PLCs (CVE-2022-1159 and CVE-2022-1161) that may very well be exploited to change person packages and obtain malicious code to the controller.