ACM.28 Testing our KMS Administrator Permissions with the AWS CLI
It is a continuation of my collection on Automating Cybersecurity Metrics.
You’ll have used a task profile with MFA earlier than. I actually have, however I take advantage of MFA a bit otherwise than the best way I used it on this venture from the best way I used MFA with function profiles prior to now.
After I began utilizing MFA to check some code I developed, I hit numerous highway blocks and spent a good period of time troubleshooting points beneath because of error messages that didn’t inform me precisely what the issue was.
The final word supply of the first error message began in one other submit. I assumed I had resolved the issue by fixing some syntax errors in a CloudFormation template, however that was solely a partial decision:
Unusual edits to a KMS Key Coverage
This all began after I needed to check use of my KMS key for encryption and I seen that one in every of my ARNs in my key coverage was edited to some unusual worth. I nonetheless don’t know what brought about that. I didn’t deploy that worth, however regardless of the trigger, I redeployed the template for the important thing coverage and it was superb once more.
I had already determined that in some unspecified time in the future I used to be going to take away extraneous customers I quickly added within the above submit and use the important thing administrator to deploy keys as was my unique plan away. For those who recall I used to be permitting the person I initially ran the script with to be a key administrator, and the basis person:
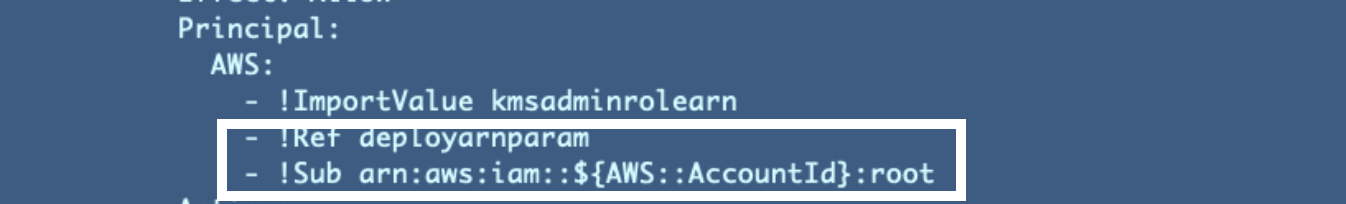
After eradicating these two customers from my key coverage I had every kind of issues deploying my key and including a key alias as detailed on this submit:
One key level within the above trial and error troubleshooting was that I couldn’t implement MFA in my key coverage since I’m utilizing a task. The one purpose that labored in my prior submit was (I feel) as a result of I included the basis person, which may move the MFA indicator in a request as I defined in earlier posts. The function can’t.
I lastly bought all my insurance policies working and deploying efficiently, however a part of the best way I resolved the issues was by fixing the AWS CLI configuration after I needed to implement MFA Within the coverage to imagine the function that was allowed to take actions on the important thing.
KMS Administrator Person
To be able to implement MFA I’ve to have a person with an MFA system assigned. I created a KMS Administrator Person through CloudFormation scripts within the iam listing of the GitHub repository. I added a coverage to the person that permits it to execute the sts:AssumeRole to imagine my KMS Administrator function however solely when an MFA situation is met. To create that person in your individual setting you may run the associated deploy.sh script.
Assign a Digital MFA system to your KMS admin person
Assign a digital MFA system to your new person. I defined why I’m utilizing a digital MFA system on this submit:
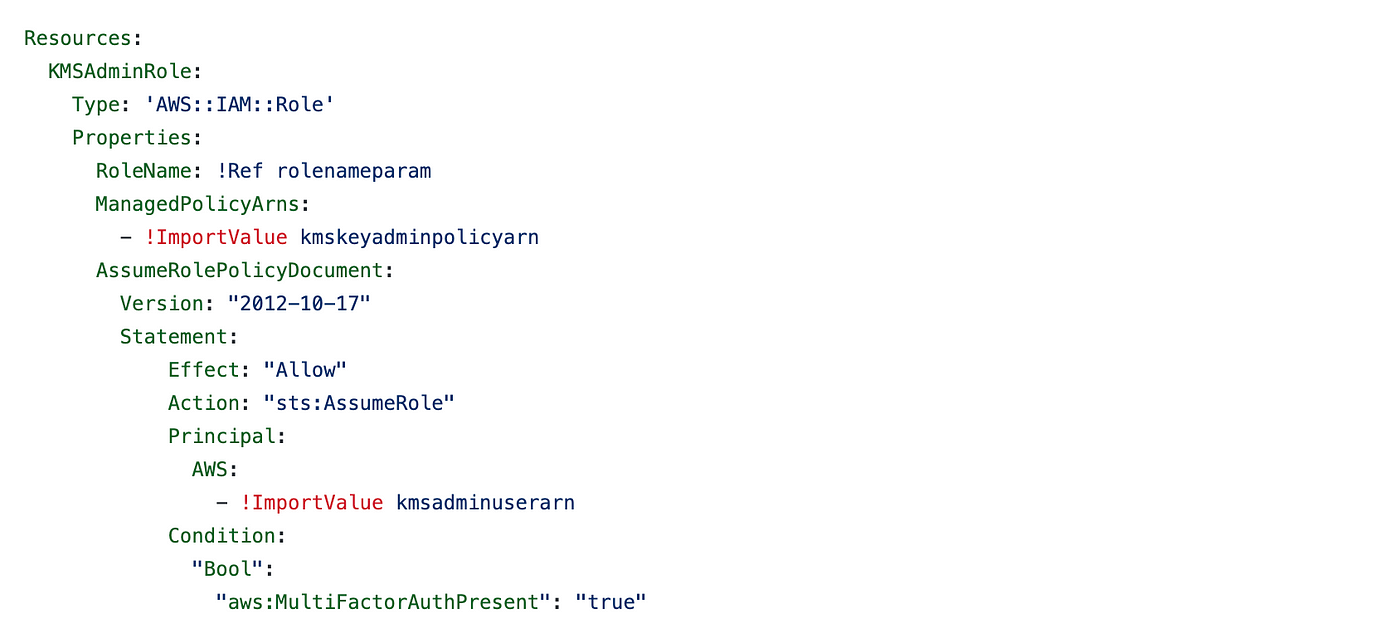
KMS Administrator Function Belief Coverage
We earlier outlined that KMS Administrator Function Belief Coverage (AssumeRolePolicyDocument) in our CloudFormation template. We create a parameter to move within the ARN of the identification that’s allowed to imagine that function. I’m presuming the customers that may assume this function will likely be in created in the identical account because the function within the template beneath and utilizing an ImportValue to get the output from the CloudFormation stack that created the person.
You possibly can deploy the up to date KMS function in your setting by operating the script within the KMS function folder:
Configure the AWS CLI profiles for our KMS Person and Function
As an alternative of 1 AWS CLI profile, I in the end needed to create two to get this working. I’m undecided in the event you completely require two however this fashion I bought higher error messages and it labored.
Run the next command to configure a profile to your KMS Person in your CLI configuration:
aws configure --profile kmsuser
Set your key id and secret key, area, and output. I added the ARN for my MFA system to this profile as nicely. You will get the ARN for an MFA system assigned to a person by navigating to IAM within the AWS profile. Then click on on Safety Credentials. Yow will discover the ARN for the assigned MFA system the place proven beneath.
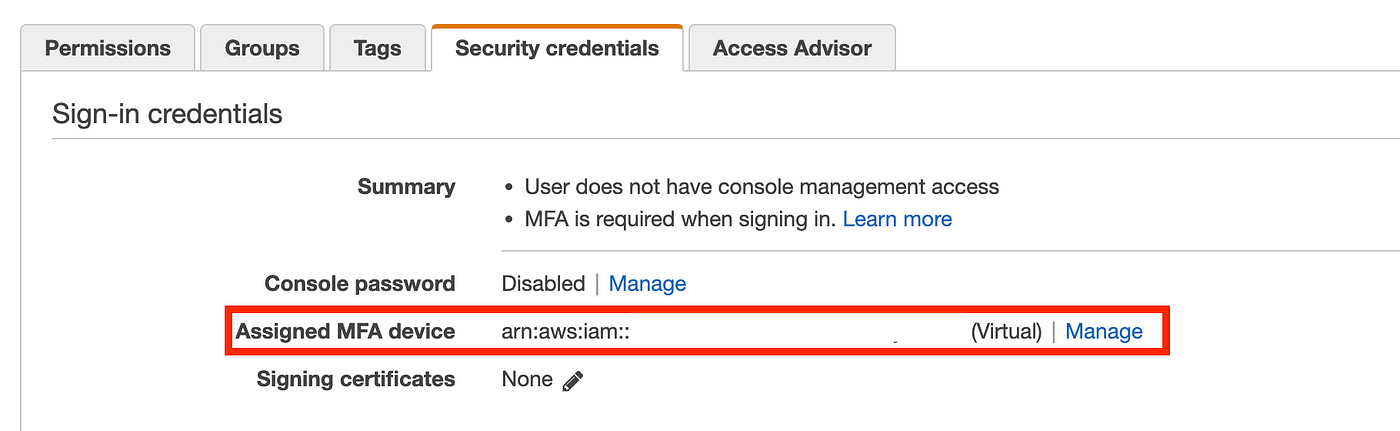
Whenever you run the aws configure command it updates a two information in your house listing. For some configuration gadgets it’s good to manually edit one of many file. One of many issues it’s important to add manually is the MFA ARN.
To edit the AWS config file that will get up to date while you run AWS configure, sort this command (on Linux):
vi ~/.aws/config
The above command presumes you might be conversant in vi. You possibly can edit that file with another editor in the event you’re not. Notice that you’ll not see that listing as a result of it’s hidden and begins with a dot (.) in the event you sort this command from your property listing:
ls
However you’ll in the event you sort this command:
ls -al
So relying in your editor and whether or not or not it permits you to navigate to hidden information you might or might not be capable to see it or open it.
Extra about command line configuration right here:
After modifying the config file so as to add the KMS Person MFA system ARN, I added one other profile named kms. I added the function ARN, MFA system ARN, and I used the kmsuser for the source_profile. Right here’s my ultimate configuration:
Substitute the xx’s with the right values to your sources and setting.
[profile kmsuser]
area = xxxxxxxxxxx
output = json
mfa_serial=arn:aws:iam::xxxxxxxxx:mfa/KmsAdmin[profile kms]
role_arn=arn:aws:iam::xxxxxxx:function/KmsAdministrator
source_profile = kmsuser
mfa_serial=arn:aws:iam::xxxxxxxx:mfa/KmsAdmin
I extremely suggest all the time copying and pasting ARNs relatively than making an attempt to sort them as a result of difficult typos which might be arduous to identify can take a very long time to troubleshoot. For instance, after I began scripting this code the person identify for the important thing admin was KmsKeyAdmin. I later modified it to KmsAdmin and forgot to replace my profile. For those who get errors double test each worth in your configuration rigorously for typos or missed adjustments. For instance, I’ve spent hours not noticing that I didn’t have TWO colons (::) after iam within the above ARN. The error messages in such instances will not be useful.
Testing the kms profile
For those who recall in our final submit we had been making an attempt to deploy a KMS key. The script to deploy that secret’s the deploy_key_trigger.sh within the kms folder within the KMS listing. Now you can to attempt to run the script along with your AWS CLI kms profile.
The script requires three arguments:
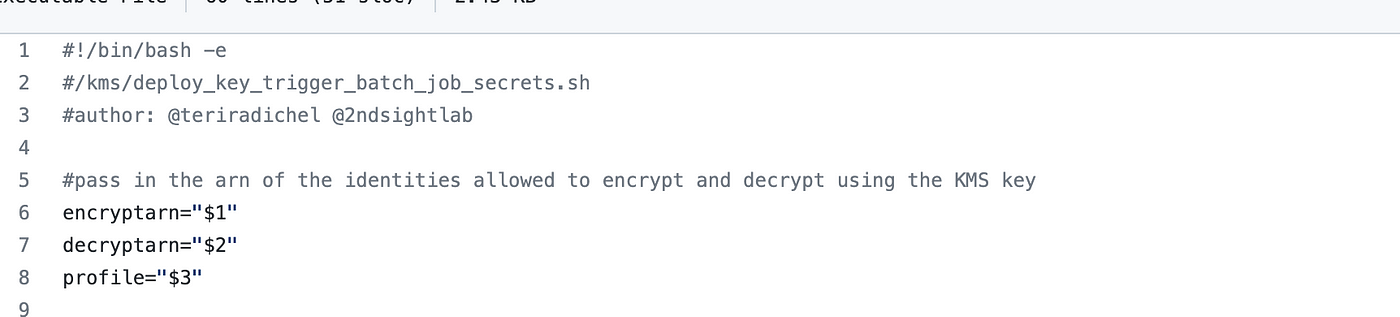
Cross within the the next arguments on the command line:
- Encrypt Function ARN
- Decrypt Function ARN
- Function profile (kms)
Yow will discover the ARNs within the outputs of the CloudFormation stacks we ran in earlier posts to create these roles.
./deploy_key_trigger.sh arn:aws:iam::xxxxxxxxxxxx:function/BatchRoleDeployBatchJobCredentials arn:aws:iam::xxxxxxxxxxxx:function/BatchJobTriggerRole kms
In case your AWS CLI profile is ready up accurately and also you’ve deployed the conditions in prior posts, then that ought to work.
You’ll be requested to enter an MFA code previous to executing the above script.
Additionally observe that I wrote about utilizing MFA with an exterior ID right here which we may add later if we deem it essential.
Arrange your IAM admin person and MFA
If you wish to run all of the take a look at scripts within the the basis listing of the GitHub repository (take a look at.sh) you’ll have to comply with the identical steps as above to deploy the IAM admin person, assign digital MFA, and configure the CLI.
There may be one distinction, nonetheless. As an alternative of getting the IAM admin assume an IAM administrator function, we’re going to permit that person to imagine the function for the batch job we’re creating to deploy the BatchJobAdmin credentials. Extra on that in upcoming weblog posts.
Observe for updates.
Teri Radichel
For those who preferred this story please clap and comply with:
Medium: Teri Radichel or Electronic mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, displays, and podcasts


