Each of those Chinese language-backed cyber operations had been found by personal cybersecurity researchers, however US federal companies have been monitoring Chinese language cyber exercise as effectively. This week, the Nationwide Safety Company (NSA), Cybersecurity & Infrastructure Safety Company (CISA), and Federal Bureau of Investigation (FBI) printed a joint cybersecurity advisory detailing ways in which Chinese language state-sponsored hackers have been compromising community suppliers and units so as to eavesdrop on community exercise and steal credentials.
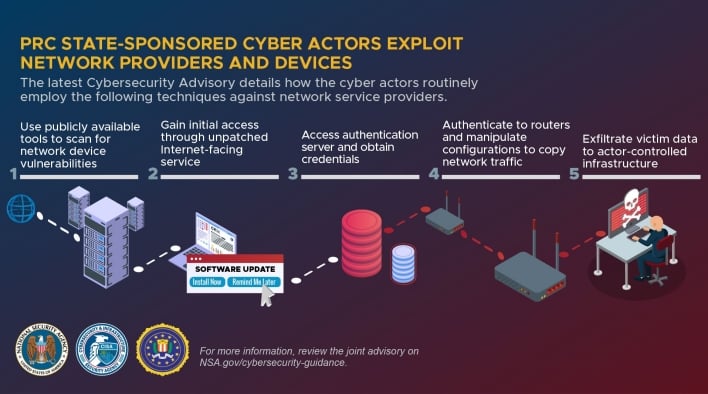
In keeping with the advisory, this cyber espionage is widespread and doesn’t solely goal massive community infrastructure, but additionally smaller, industrial community units, like routers and Community Hooked up Storage (NAS) units. The Chinese language hackers perform this exercise by exploiting identified vulnerabilities in community units. In lots of instances, the distributors who manufacture these community units have launched patches that repair the vulnerabilities, however community directors have uncared for to replace the units. The next desk lists the identified community units vulnerabilities mostly leveraged by Chinese language-backed hackers.
| Vendor | CVE Identifier |
Vulnerability Sort |
Severity |
| Cisco | CVE-2019-11510 | Distant Code Execution |
9.8 Crucial |
| CVE-2019-15271 | Distant Code Execution | 8.8 Excessive |
|
| CVE-2019-1652 | Distant Code Execution | 7.2 Excessive |
|
| Citrix | CVE-2019-19781 | Distant Code Execution | 9.8 Crucial |
| DrayTek | CVE-2020-8515 | Distant Code Execution | 9.8 Crucial |
| D-Hyperlink | CVE-2019-16920 | Distant Code Execution | 9.8 Crucial |
| Fortinet | CVE-2018-13382 | Authentication Bypass |
7.5 Excessive |
| MikroTik | CVE-2018-14847 | Authentication Bypass | 9.1 Crucial |
| Netgear | CVE-2017-6862 | Distant Code Execution |
9.8 Crucial |
| Pulse | CVE-2019-11510 | Authentication Bypass |
10 Crucial |
| CVE-2021-22893 | Distant Code Execution |
10 Crucial |
|
| QNAP |
CVE-2019-7192 | Privilege Elevation |
9.8 Crucial |
| CVE-2019-7193 | Distant Inject |
9.8 Crucial |
|
| CVE-2019-7194 | XML Routing Detour Assault |
9.8 Crucial |
|
| CVE-2019-7195 | XML Routing Detour Assault |
9.8 Crucial |
|
| Zyxel | CVE-2020-29583 | Authentication Bypass |
9.8 Crucial |
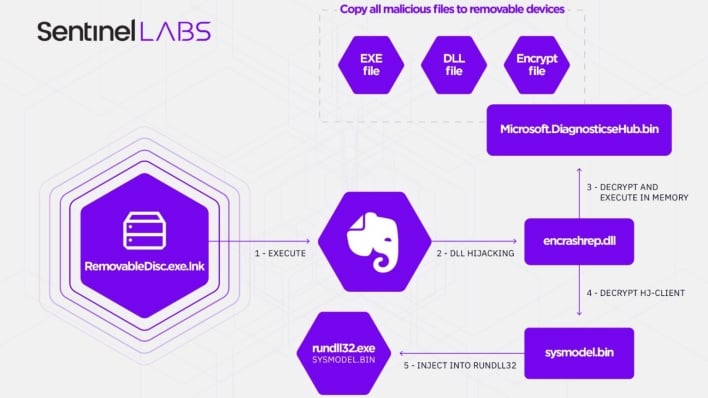
The Chinese language hacking group’s ways have been via a number of modifications since 2013. Round 2016, the group moved from malicious Microsoft Phrase paperwork to faux antivirus executables. Then, in 2018, Aoqin Dragon shifted to utilizing faux detachable units and remains to be utilizing that technique at current. The group makes use of “RemovableDisc” shortcuts that launch “RemovableDisc.exe.” This executable installs malware that runs on system startup as “Evernote Tray Software.” This malware installs two extra malware payloads. The primary payload copies the malware to all detachable units, and the second payload installs a backdoor that communicates with the hackers’ command-and-control (C2) infrastructure.


