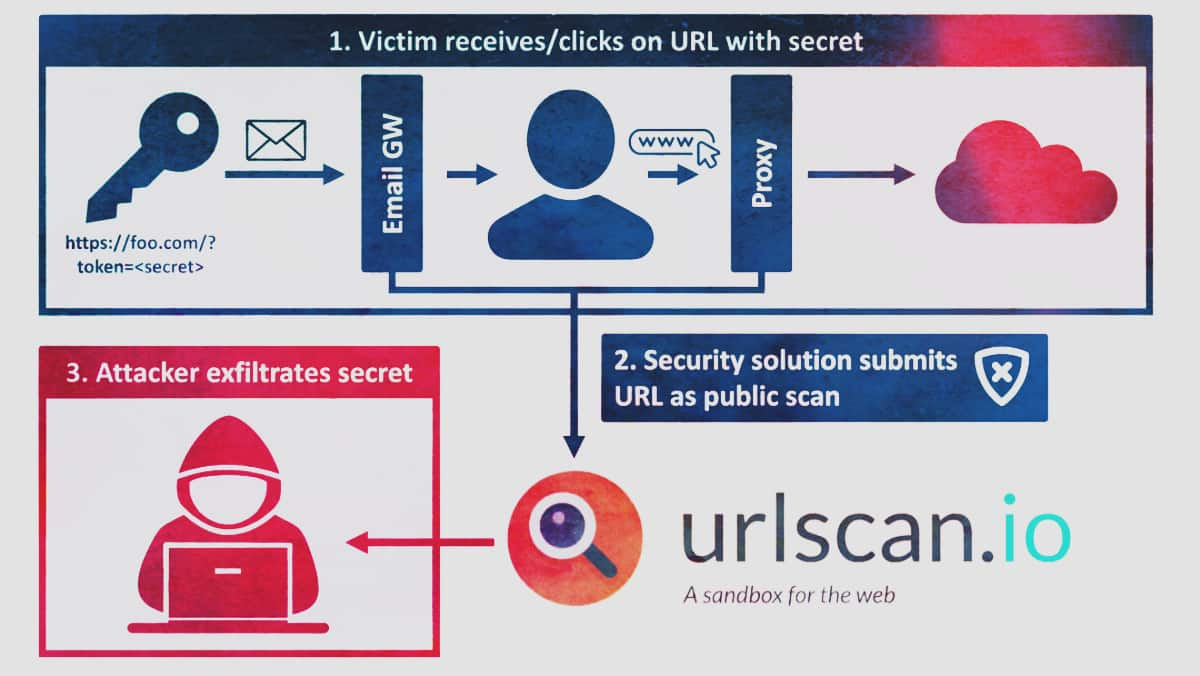
Berlin-based digital safety agency Optimistic Safety’s newest weblog submit revealed how Urlscan API has been leaking delicate URLs and information unintentionally. The corporate was alerted by an electronic mail from GitHub in February 2022.
It’s suspected that GitHub Pages URLs had been leaked unintentionally by way of a third-party whereas conducting metadata evaluation.
What’s Urlscan.io?
Urlscan.io is an internet site scanning and analyzing engine that accepts URL submissions and creates a trove of knowledge corresponding to IPs, domains, DOM data, screenshots, and cookies.
Based on Urlscan.io builders, the engine is sort of a sandbox for the net. It was created to let customers “simply and confidently” assess doubtlessly malicious web sites. The engine helps numerous enterprise prospects and open-source tasks. It comes with an API that integrates its scans into third-party merchandise.
What’s the Concern?
Given the API’s integration kind, corresponding to a safety instrument that scans all incoming emails and conducts a Urlscan on all hyperlinks, there could possibly be an enormous quantity and number of delicate information that an nameless consumer can simply seek for and retrieve.
An investigation was launched after GitHub’s notification concerning customers sharing their personal repository names and usernames to Urlscan.io for metadata evaluation robotically.
When pingbacks to leaked electronic mail IDs had been checked, researchers detected that misconfigured safety instruments submitting hyperlinks acquired in emails as public scans had been the basis reason for the issue. As an illustration, some API integrations use generic python-requests/2.X.Y. If consumer brokers ignored account visibility settings, it allowed scans to be mistakenly submitted as public.
Extent of Influence
Additional probe revealed that the problem could possibly be affecting urlscan.io dorks, setup pages, password reset hyperlinks, Telegram bots, assembly invites, DocuSign signing requests, shared Google Drive hyperlinks, PayPal, SharePoint, Discord, Zoom invoices, Cisco Webex assembly recordings, Dropbox file transfers package deal monitoring hyperlinks, and PayPal invoices, mentioned Fabian Bräunlein, Optimistic Safety co-founder within the report.
It’s price noting that the corporate additionally discovered juicy URLs belonging to Apple domains, and a few contained publicly-shared hyperlinks to iCloud information. Nonetheless, these have now been eliminated.
On your data, in relation to search engine marketing, a “juicy” URL is one that’s full of key phrases and phrases that assist enhance your rating in search engine outcomes pages.
Optimistic Safety acquired in contact with a lot of the leaked electronic mail addresses and acquired a response from an unnamed group. It traced the leak of a DocuSign work contract hyperlink to its misconfigured Safety Orchestration, Automation, and Response (SOAR) answer that Urlscan.io built-in.
Risk Mitigation Efforts
After finishing the problem evaluation in July, Optimistic Safety notified Urlscan.io about its findings and collaborated with its builders to deal with the problem. A brand new engine model was launched later that month with an enhanced scan visibility interface and team-wide visibility settings.
The corporate additionally printed its Scan Visibility Finest Practices to elucidate the dangers related to the three visibility settings customers chosen when submitting a URL- Public, Unlisted, and Non-public. After reviewing third-party SOAR instrument integrations, the builders added deletion guidelines and enhanced visibility settings within the consumer interface. In addition they included a report button for the deactivation of problematic search outcomes.
Associated Information
- Hackers can entry trove of stolen credentials on VirusTotal
- Leaked Amazon Prime Video Server Uncovered Customers Viewing Habits
- Delicate information of cyber safety agency & different companies leaked on-line
- Private particulars of 21M SuperVPN, GeckoVPN customers leaked on Telegram
- Man Unintentionally Destroyed Manufacturing Database on First Day of His Job