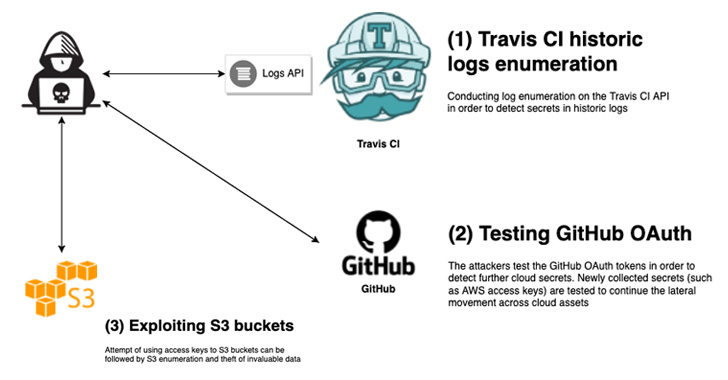
An unpatched safety problem within the Travis CI API has left tens of 1000’s of builders’ person tokens uncovered to potential assaults, successfully permitting risk actors to breach cloud infrastructures, make unauthorized code modifications, and provoke provide chain assaults.
“Greater than 770 million logs of free tier customers can be found, from which you’ll simply extract tokens, secrets and techniques, and different credentials related to fashionable cloud service suppliers comparable to GitHub, AWS, and Docker Hub,” researchers from cloud safety agency Aqua mentioned in a Monday report.
Travis CI is a steady integration service used to construct and check software program initiatives hosted on cloud repository platforms comparable to GitHub and Bitbucket.
The difficulty, beforehand reported in 2015 and 2019, is rooted in the truth that the API permits entry to historic logs in cleartext format, enabling a malicious celebration to even “fetch the logs that have been beforehand unavailable through the API.”
The logs go all the best way again to January 2013 and up till Might 2022, starting from log numbers 4,280,000 to 774,807,924, that are used to retrieve a novel cleartext log by means of the API.
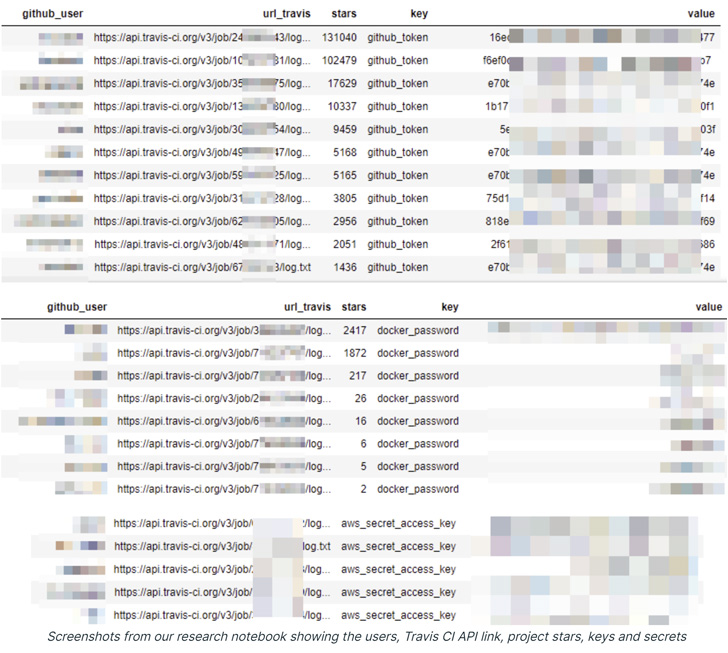
What’s extra, additional evaluation of 20,000 logs revealed as many as 73,000 tokens, entry keys, and different credentials related to varied cloud providers like GitHub, AWS, and Docker Hub.
That is regardless of Travis CI’s makes an attempt to rate-limit the API and routinely filter out safe setting variables and tokens from construct logs by displaying the string “[secure]” of their place.
One of many essential insights is that whereas “github_token” was obfuscated, 20 different variations of this token that adopted a unique naming conference — together with github_secret, gh_token, github_api_key, and github_secret — weren’t masked by Travis CI.
“Travis CI slowed down the speed of API calls, which hinders the flexibility to question the API,” the researchers mentioned. “On this case nonetheless, this was not sufficient. A talented risk actor can discover a workaround to bypass this.”
“Nevertheless, combining the convenience of accessing the logs through the API, incomplete censoring, accessing ‘restricted’ logs, and a weak course of for fee limiting and blocking entry to the API, coupled with numerous doubtlessly uncovered logs, ends in a essential scenario.”
Travis CI, in response to the findings, has mentioned the problem is “by design,” necessitating that customers comply with finest practices to keep away from leaking secrets and techniques in construct logs and periodically rotate tokens and secrets and techniques.
The findings are significantly vital within the wake of an April 2022 assault marketing campaign that leveraged stolen OAuth person tokens issued to Heroku and Travis CI to escalate entry to NPM infrastructure and clone choose non-public repositories.