It seems that Akamai’s group of researchers unintentionally killed a newly found cryptocurrency mining botnet generally known as KmsdBot through the investigation.
As a result of a syntax error, the botnet was unable to ship instructions any longer, and consequently, it was destroyed.
KmsdBot and its C2 performance
KMSDBot is a cryptomining botnet that makes use of weak credentials and SSH to contaminate its victims with a crypto-mining malware after which deploy the miner. Other than this, the KmsdBot is supplied with command-and-control capabilities.
After certainly one of Akamai’s honeypots was contaminated with the botnet, the Akamai group assessed the scenario and reported on it.
A wide range of microarchitectures have been used within the botnet’s deployment to focus on Linux and Home windows gadgets, and on these gadgets, it deploy the next parts:-
It primarily targets corporations which are concerned in gaming and expertise, in addition to producers of luxurious automobiles.
It’s crucial to notice that the power to achieve C2 is arguably probably the most deadly side of any malicious entity, and KmsdBot is the one which has the C2 functionalities.
Occasion Data
Researchers from Akamai reported that the working mechanism of the botnet in a managed setting, they despatched instructions that mistakenly neutralized the malware.
A bot stopped sending instructions as quickly because it acquired a command that was improperly formatted. A attainable cause for this might be that this system was not constructed with an inside error-checking function that will test the instructions coming into its supply code for errors earlier than they have been executed.
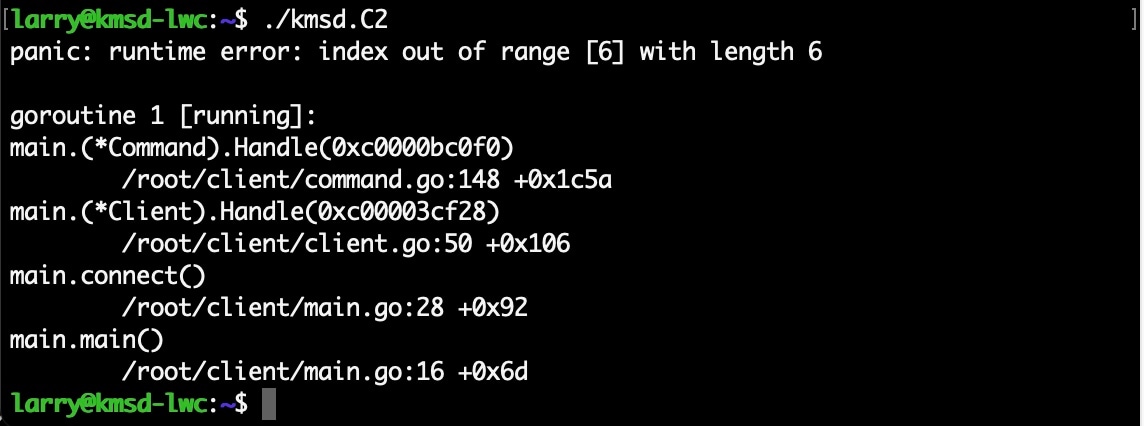
On the contaminated gadgets, the Go binary cease interacting with its C2 server, consequently when the instruction is given to the goal web site and not using a house between the port quantity.
A persistence mechanism shouldn’t be current within the botnet, as a consequence of its lack of performance. In brief, within the occasion of detection, the operators of the botnet might want to re-infect the goal machine.
Consequently, this may be seen for instance of how expertise is capricious, and the way even the one who is exploiting it could discover themselves exploited, too.
Safe Internet Gateway – Internet Filter Guidelines, Exercise Monitoring & Malware Safety – Obtain Free E-Ebook


