TTL safety in BGP
Whereas forming eBGP neighborship by way of Service supplier community, there may be safety danger concerned on possible assault from unsecured Web Service supplier area to secured buyer surroundings. A disadvantage to eBGP multihop is that by spoofing reputable packets in the direction of a BGP router at excessive quantity a DOS assault could also be achieved.
Cisco has devised technique to handle the menace on BGP communication to fulfill clear communication between buyer and supplier BGP interlock.
By default the Cisco IOS ship eBGP messages with a TTL worth of 1.We will nonetheless modify this worth utilizing the eBGP multi-hop function. If the TTL worth of 1 is shipped it requires the BGP neighbors to be straight related else the neighbourship received’t be established.
Utilizing eBGP multihop we are able to kind neighbourship with friends at some hops away quite than being straight related.
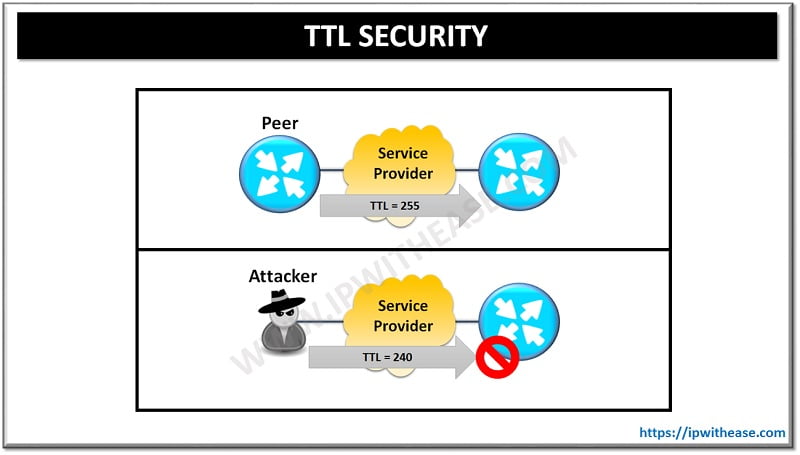
TTL-Safety is a mechanism we use to guard our eBGP session in opposition to such DOS assaults. BGP TTL Safety test can solely be used with eBGP classes and never with iBGP classes.TTL Safety and eBGP multihop are mutually unique and just one might be configured to kind straight related or multihop peering classes.eBGP
Associated- DOS vs DDOS Assault
We will configure the TTL-Safety function in opposition to an eBGP neighbor utilizing a easy command:
neighbor TTL-security hops
BGP by default sends packets to exterior neighbours with a TTL of 1 and accepts packets from exterior neighbours with a TTL of 0 or larger (as measured after the native router has decremented the TTL of the incoming packet).
The TTL-Safety adjustments the default conduct of originating by having BGP originate packets with a TTL of 255.
BGP Messages acceptance standards in case TTL Safety is configured:
TTL of the IP Packet ought to be larger than or equal to 255 – (Hop Depend Configured)
Associated – What’s TTL?
TOPOLOGY: TTL in Community Safety
On this topology we’ll kind neighborship over the R1 and R2’s loopback interface with ttl-security hop as 2.
R1 will settle for solely these packets from R2 which have the IP TTL worth of 253 a minimum of.
CONFIGURATIONS:
R1:
interface Loopback0
ip deal with 1.1.1.1 255.255.255.255
ip ospf 1 space 0
!
interface FastEthernet0/0
ip deal with 9.9.12.1 255.255.255.0
ip ospf 1 space 0
!
router bgp 100
bgp log-neighbor-changes
neighbor 2.2.2.2 remote-as 200
neighbor 2.2.2.2 ttl-security hops 2
neighbor 2.2.2.2 update-source Loopback0
R2:
interface Loopback0
ip deal with 2.2.2.2 255.255.255.255
ip ospf 1 space 0
!
interface FastEthernet0/0
ip deal with 9.9.12.2 255.255.255.0
ip ospf 1 space 0
!
router bgp 200
bgp log-neighbor-changes
neighbor 1.1.1.1 remote-as 100
neighbor 1.1.1.1 ttl-security hops 2
neighbor 1.1.1.1 update-source Loopback0
VERIFICATION:
We see the TTL worth minimal required is 253 which is 255 (Hop-Depend Configured)
R1# sh ip bgp neighbors 2.2.2.2
BGP model 4, distant router ID 2.2.2.2
BGP state = Established, up for 00:02:12
Final learn 00:00:22, final write 00:00:19, maintain time is 180, keepalive interval is 60 seconds
Neighbor classes:
1 lively, isn’t multisession succesful (disabled)
Neighbor capabilities:
Route refresh: marketed and acquired(new)
4-octets ASN Functionality: marketed and acquired
Deal with household IPv4 Unicast: marketed and acquired
Enhanced Refresh Functionality: marketed and acquired
Multisession Functionality:
Stateful switchover assist enabled: NO for session 1
Message statistics:
InQ depth is 0
OutQ depth is 0
Despatched Rcvd
Opens: 1 1
Notifications: 0 0
Updates: 1 1
Keepalives: 3 3
Route Refresh: 0 0
Complete: 5 5
Default minimal time between commercial runs is 30 seconds
For deal with household: IPv4 Unicast
Session: 2.2.2.2
BGP desk model 1, neighbor model 1/0
Output queue dimension : 0
Index 1, Promote bit 0
1 update-group member
Gradual-peer detection is disabled
Gradual-peer split-update-group dynamic is disabled
Despatched Rcvd
Prefix exercise: —- —-
Prefixes Present: 0 0
Prefixes Complete: 0 0
Implicit Withdraw: 0 0
Specific Withdraw: 0 0
Used as bestpath: n/a 0
Used as multipath: n/a 0
Outbound Inbound
Native Coverage Denied Prefixes: ——– ——-
Complete: 0 0
Variety of NLRIs within the replace despatched: max 0, min 0
Final detected as dynamic gradual peer: by no means
Dynamic gradual peer recovered: by no means
Refresh Epoch: 1
Final Despatched Refresh Begin-of-rib: by no means
Final Despatched Refresh Finish-of-rib: by no means
Final Acquired Refresh Begin-of-rib: by no means
Final Acquired Refresh Finish-of-rib: by no means
Despatched Rcvd
Refresh exercise: —- —-
Refresh Begin-of-RIB 0 0
Refresh Finish-of-RIB 0 0
Deal with monitoring is enabled, the RIB does have a path to 2.2.2.2
Connections established 1; dropped 0
Final reset by no means
Exterior BGP neighbor could also be as much as 2 hops away.
Transport(tcp) path-mtu-discovery is enabled
Sleek-Restart is disabled
Connection state is ESTAB, I/O standing: 1, unread enter bytes: 0
Connection is ECN Disabled
Minimal incoming TTL 253, Outgoing TTL 255
Native host: 1.1.1.1, Native port: 179
International host: 2.2.2.2, International port: 22265
Connection tableid (VRF): Minimal incoming TTL 253, Outgoing TTL Enqueued packets for retransmit: 0, enter: 0 mis-ordered: 0 (0 bytes)
Occasion Timers (present time is 0x3603C):
Timer Begins Wakeups Subsequent
Retrans 4 0 0x0
TimeWait 0 0 0x0
AckHold 5 3 0x0
SendWnd 0 0 0x0
KeepAlive 0 0 0x0
GiveUp 0 0 0x0
PmtuAger 0 0 0x0
DeadWait 0 0 0x0
Linger 0 0 0x0
iss: 3246214154 snduna: 3246214292 sndnxt: 3246214292 sndwnd: 16247
irs: 1717271364 rcvnxt: 1717271502 rcvwnd: 16247 delrcvwnd: 137
SRTT: 125 ms, RTTO: 1414 ms, RTV: 1289 ms, KRTT: 0 ms
minRTT: 104 ms, maxRTT: 312 ms, ACK maintain: 200 ms
Standing Flags: passive open, gen tcbs
Possibility Flags: nagle, path mtu succesful
Datagrams (max knowledge section is 1460 bytes):
Rcvd: 9 (out of order: 0), with knowledge: 5, whole knowledge bytes: 137
Despatched: 9 (retransmit: 0 fastretransmit: 0),with knowledge: 5, whole knowledge bytes: 137
Associated- BGP disable-connected-check