The U.S. Treasury Division on Friday introduced sanctions towards Iran’s Ministry of Intelligence and Safety (MOIS) and its Minister of Intelligence, Esmaeil Khatib, for participating in cyber-enabled actions towards the nation and its allies.
“Since at the very least 2007, the MOIS and its cyber actor proxies have performed malicious cyber operations focusing on a variety of presidency and private-sector organizations around the globe and throughout numerous important infrastructure sectors,” the Treasury mentioned.
The company additionally accused Iranian state-sponsored actors of staging disruptive assaults aimed toward Albanian authorities laptop methods in mid-July 2022, forcing it to droop its on-line companies.
The event comes months practically 9 months after the U.S. Cyber Command characterised the superior persistent menace (APT) generally known as MuddyWater as a subordinate factor inside MOIS. It additionally comes nearly two years following the Treasury’s sanctions towards one other Iranian APT group dubbed APT39 (aka Chafer or Radio Serpens).
Friday’s sanctions successfully prohibit U.S. companies and residents from participating in transactions with MOIS and Khatib, and non-U.S. residents that have interaction in transactions with the designated entities might themselves be uncovered to sanctions.
Coinciding with the financial blockade, the Albanian authorities mentioned the cyberattack on the digital infrastructure was “orchestrated and sponsored by the Islamic Republic of Iran by means of the engagement of 4 teams that enacted the aggression.”
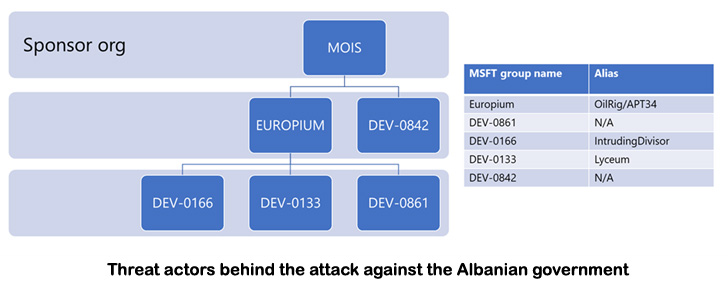
Microsoft, which investigated the assaults, mentioned the adversaries labored in tandem to hold out distinct phases of the assaults, with every cluster liable for a special side of the operation –
- DEV-0842 deployed the ransomware and wiper malware
- DEV-0861 gained preliminary entry and exfiltrated information
- DEV-0166 (aka IntrudingDivisor) exfiltrated information, and
- DEV-0133 (aka Lyceum or Siamese Kitten) probed sufferer infrastructure
The tech big’s menace intelligence groups additionally attributed the teams concerned in gaining preliminary entry and exfiltrating information to the Iranian MOIS-linked hacking collective codenamed Europium, which is also referred to as APT34, Cobalt Gypsy, Helix Kitten, or OilRig.
“The attackers liable for the intrusion and exfiltration of information used instruments beforehand utilized by different identified Iranian attackers,” it mentioned in a technical deepdive. “The attackers liable for the intrusion and exfiltration of information focused different sectors and international locations which are per Iranian pursuits.”
“The Iranian sponsored try at destruction had lower than a ten% complete affect on the client setting,” the corporate famous, including the post-exploitation actions concerned the usage of net shells for persistence, unknown executables for reconnaissance, credential harvesting strategies, and protection evasion strategies to show off safety merchandise.
Microsoft’s findings dovetail with earlier evaluation from Google’s Mandiant, which known as the politically motivated exercise a “geographic growth of Iranian disruptive cyber operations.”
Preliminary entry to the community of an Albanian authorities sufferer is claimed to have occurred as early as Might 2021 through profitable exploitation of a SharePoint distant code execution flaw (CVE-2019-0604), adopted by exfiltration of electronic mail from the compromised community between October 2021 and January 2022.
A second, parallel wave of electronic mail harvesting was noticed between November 2021 and Might 2022, possible by means of a software known as Jason. On high of that, the intrusions entailed the deployment of ransomware known as ROADSWEEP, ultimately resulting in the distribution of a wiper malware known as ZeroCleare.
Microsoft characterised the harmful marketing campaign as a “type of direct and proportional retaliation” for a string of cyberattacks on Iran, together with one staged by an Iranian hacktivist group that is affiliated to Mujahedin-e-Khalq (MEK) within the first week of July 2022.
The MEK, also referred to as the Individuals’s Mujahedin Group of Iran (PMOI), is an Iranian dissident group largely based mostly in Albania that seeks to overthrow the federal government of the Islamic Republic of Iran and set up its personal authorities.
“A number of the Albanian organizations focused within the harmful assault have been the equal organizations and authorities businesses in Iran that skilled prior cyberattacks with MEK-related messaging,” the Home windows maker mentioned.
Iran’s Overseas Ministry, nevertheless, has rejected accusations that the nation was behind the digital offensive on Albania, calling them “baseless” and that it is “a part of accountable worldwide efforts to cope with the specter of cyberattacks.”