U.S. cybersecurity and intelligence businesses have warned about China-based state-sponsored cyber actors leveraging community vulnerabilities to take advantage of private and non-private sector organizations since not less than 2020.
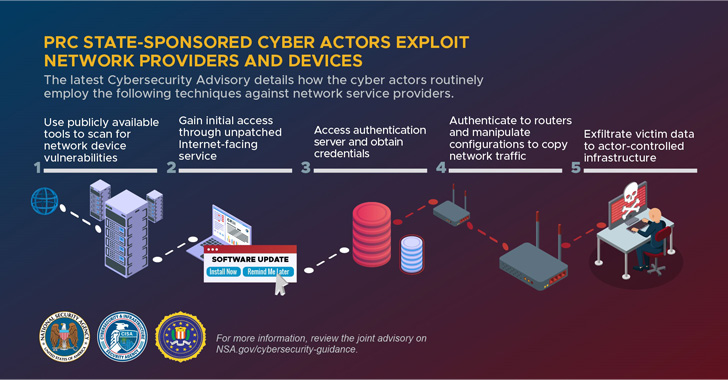
The widespread intrusion campaigns goal to take advantage of publicly recognized safety flaws in community units similar to Small Workplace/House Workplace (SOHO) routers and Community Connected Storage (NAS) units with the purpose of gaining deeper entry to sufferer networks.
As well as, the actors used these compromised units as route command-and-control (C2) visitors to interrupt into different targets at scale, the U.S. Nationwide Safety Company (NSA), the Cybersecurity and Infrastructure Safety Company (CISA), and the Federal Bureau of Investigation (FBI) stated in a joint advisory.
The perpetrators, in addition to shifting their techniques in response to public disclosures, are identified to make use of a mixture of open-source and customized instruments for reconnaissance and vulnerability scanning in addition to to obscure and mix their exercise.
The assaults themselves are facilitated by accessing compromised servers, which the businesses referred to as hop factors, from China-based IP addresses, utilizing them to host C2 domains, e-mail accounts, and talk with the goal networks.
“Cyber actors use these hop factors as an obfuscation approach when interacting with sufferer networks,” the businesses famous, detailing the adversary’s sample of weaponizing flaws in telecommunications organizations and community service suppliers.
Upon gaining a foothold into the community by way of an unpatched internet-facing asset, the actors have been noticed acquiring credentials for consumer and administrative accounts, adopted by working router instructions to “surreptitiously route, seize, and exfiltrate visitors out of the community to actor-controlled infrastructure.”
Final however not least, the attackers additionally modified or eliminated native log information to erase proof of their exercise to additional conceal their presence and evade detection.
The businesses didn’t single out a selected menace actor, however famous that the findings replicate Chinese language state-sponsored teams’ historical past of aggressively placing essential infrastructure to steal delicate information, rising key applied sciences, mental property, and personally identifiable data.
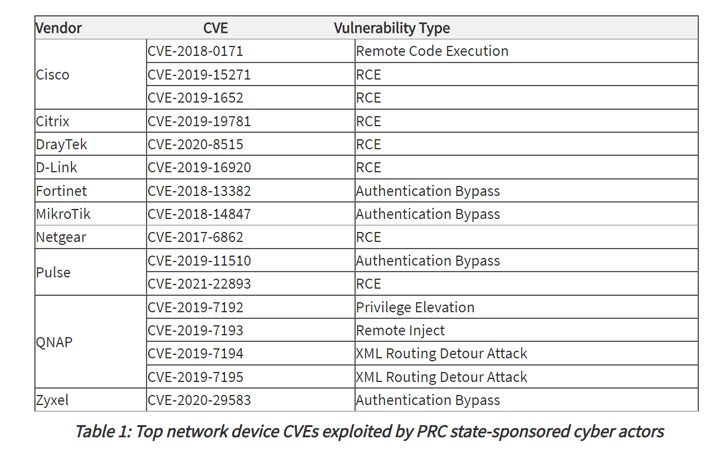
The disclosure additionally arrives lower than a month after the cybersecurity authorities revealed essentially the most routinely exploited preliminary entry vectors to breach targets, a few of which embody misconfigured servers, weak password controls, unpatched software program, and failure to dam phishing makes an attempt.
“Entities can mitigate the vulnerabilities listed on this advisory by making use of the out there patches to their techniques, changing end-of-life infrastructure, and implementing a centralized patch administration program,” the businesses stated.