Boy, do now we have a doozy for you! Final week, Twitter claimed that it is not accountable for a leak that uncovered information from over 200 million customers. “There is no such thing as a proof that the information being bought on-line was obtained by exploiting a vulnerability of Twitter methods,” the social media large concluded after — er — a self “investigation.”
As we talked about earlier than, we’re skeptical about this. In spite of everything, are you able to actually belief an organization that makes use of an inside staff to totally — and honestly — examine its personal flaws? On prime of that, Alon Gal, founding father of Israel-based cybersecurity agency Hudson Rock who first blew the whistle concerning the information leak, is additionally leery about Twitter’s “investigation.” He nonetheless maintains that Twitter should not escape culpability for the information breach.
And it would not cease there. The anon behind Twitter’s 200 million+ information dump on Breached (a hackers’ discussion board) reached out to Laptop computer Magazine to inform us that Twitter, as we suspected, is “nearly definitely mendacity” — this is why.
Twitter’s data-breach debacle
Earlier than we flesh out Twitter’s questionable report, this is some background on the data-breach debacle. In January 2022, a hawk-eyed observer from Twitter’s bug bounty program instructed the social media large about an API vulnerability that exposes customers’ information. How might one exploit this flaw? Good query. This is how Twitter described it:
“By submitting an electronic mail deal with or telephone quantity to Twitter’s methods, Twitter’s methods would inform the particular person what Twitter account the submitted electronic mail addresses or telephone quantity was related to it. This difficulty got here from an replace to Twitter’s code in June 2021.”
Nonetheless, Twitter claimed that it patched the vulnerability in January 2022. Sadly, it was too little, too late. In July 2022, a hacker took to Breached to disclose that they had been in possession of a dataset that includes greater than 5 million Twitter customers (electronic mail addresses and telephone numbers had been uncovered). They managed to safe the information earlier than Twitter patched the safety flaw in January 2022.
Twitter then knowledgeable customers concerning the incident in August 2022. Now, this is the place it will get attention-grabbing. Utilizing the identical vulnerability patched in January 2022, in late December, a menace actor claimed that they managed to safe a knowledge dump of 400 million Twitter customers — and requested $200,000 for the dataset. (To be clear, that is one other occasion by which a menace actor exploited the infamous vulnerability earlier than the patch, seemingly a while in the course of the tail-end of 2021.)
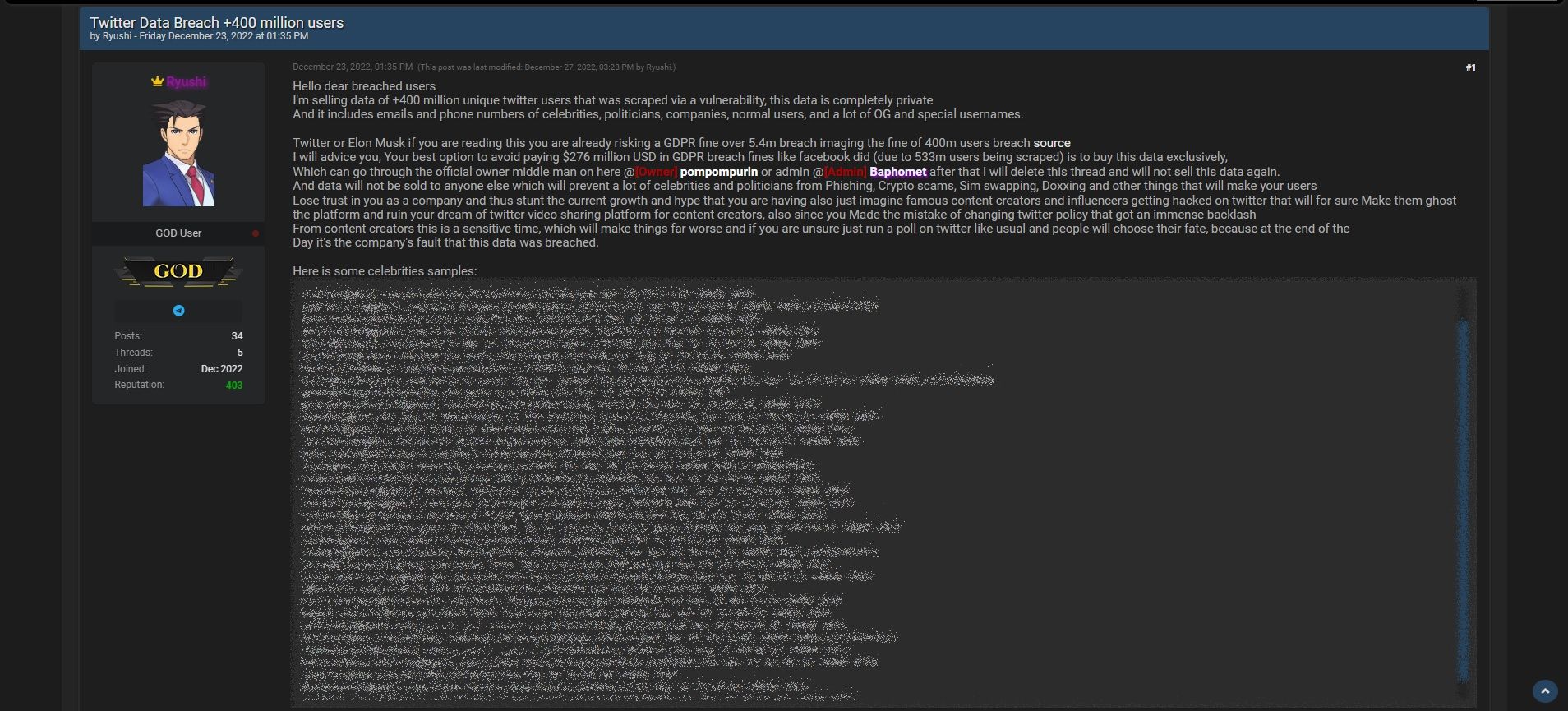
The menace actor (who calls himself “Ryushi”) made it clear that he ideally wished that $200,000 from Twitter:
“Twitter, or Elon Musk, in case you are studying this, you might be risking a GDPR advantageous over 5.4m breach imaging the advantageous of 400m customers breach supply,” Ryushi stated. “The best choice is to keep away from paying $276 million USD in GDPR breach fines like Fb did (as a result of 533m customers being scraped) is to purchase this information solely.”
Ryushi boasted that the dataset incorporates emails and telephone numbers of celebrities and politicians, together with Alexandria Ocasio-Cortez, Donald Trump Jr., Mark Cuban, Piers Morgan, and extra. (Bear in mind, nevertheless, that Breached member “StayMad” uncovered Ryushi for mendacity concerning the existence of telephone numbers within the dataset.)
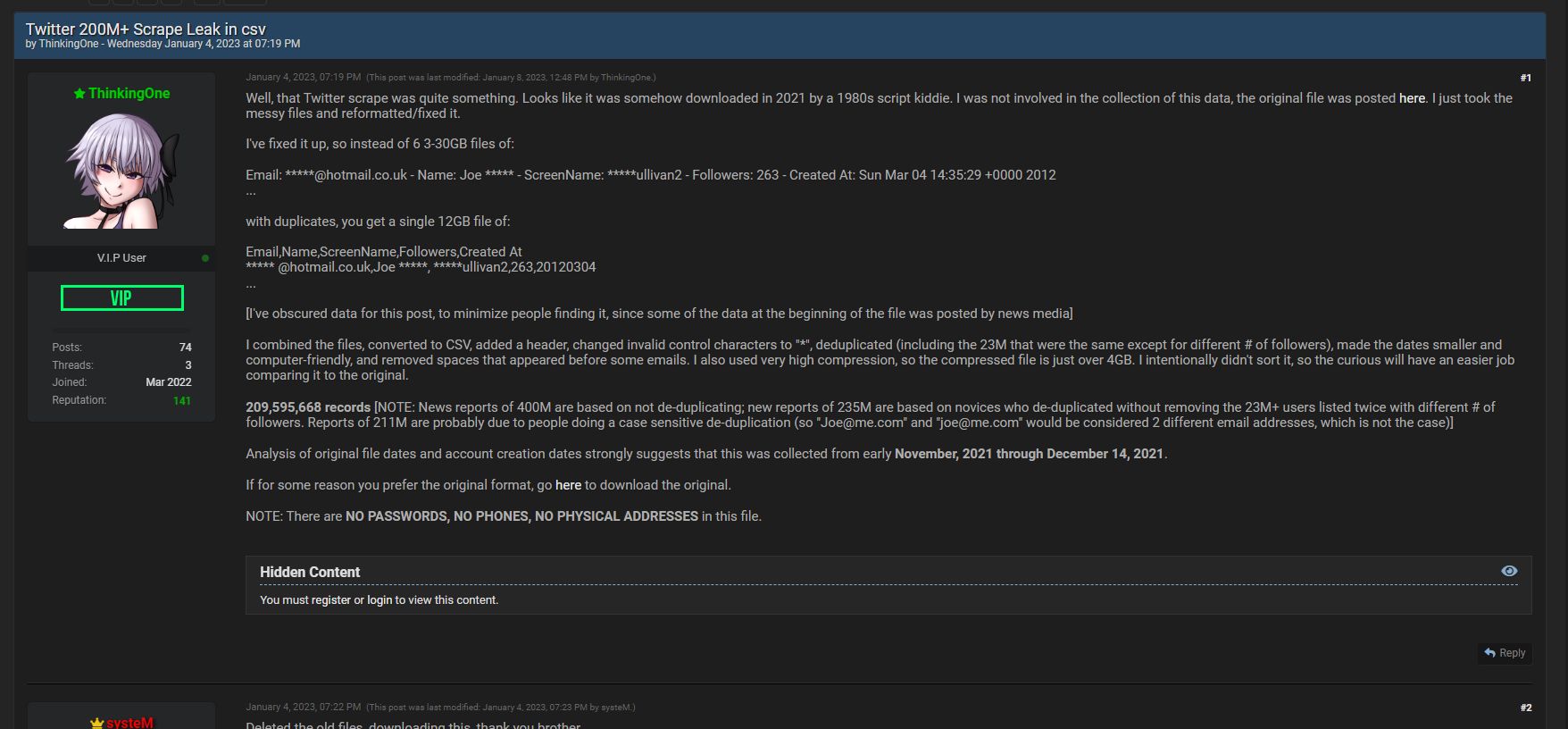
In early January, Breached member ThinkingOne — the anon who reached to us — revealed the identical dataset from Ryushi, however it was de-duplicated (redundant data eliminated). As such, the true variety of customers reportedly scraped from Twitter’s vulnerability is over 200 million, not 400 million (as initially reported by Ryushi).
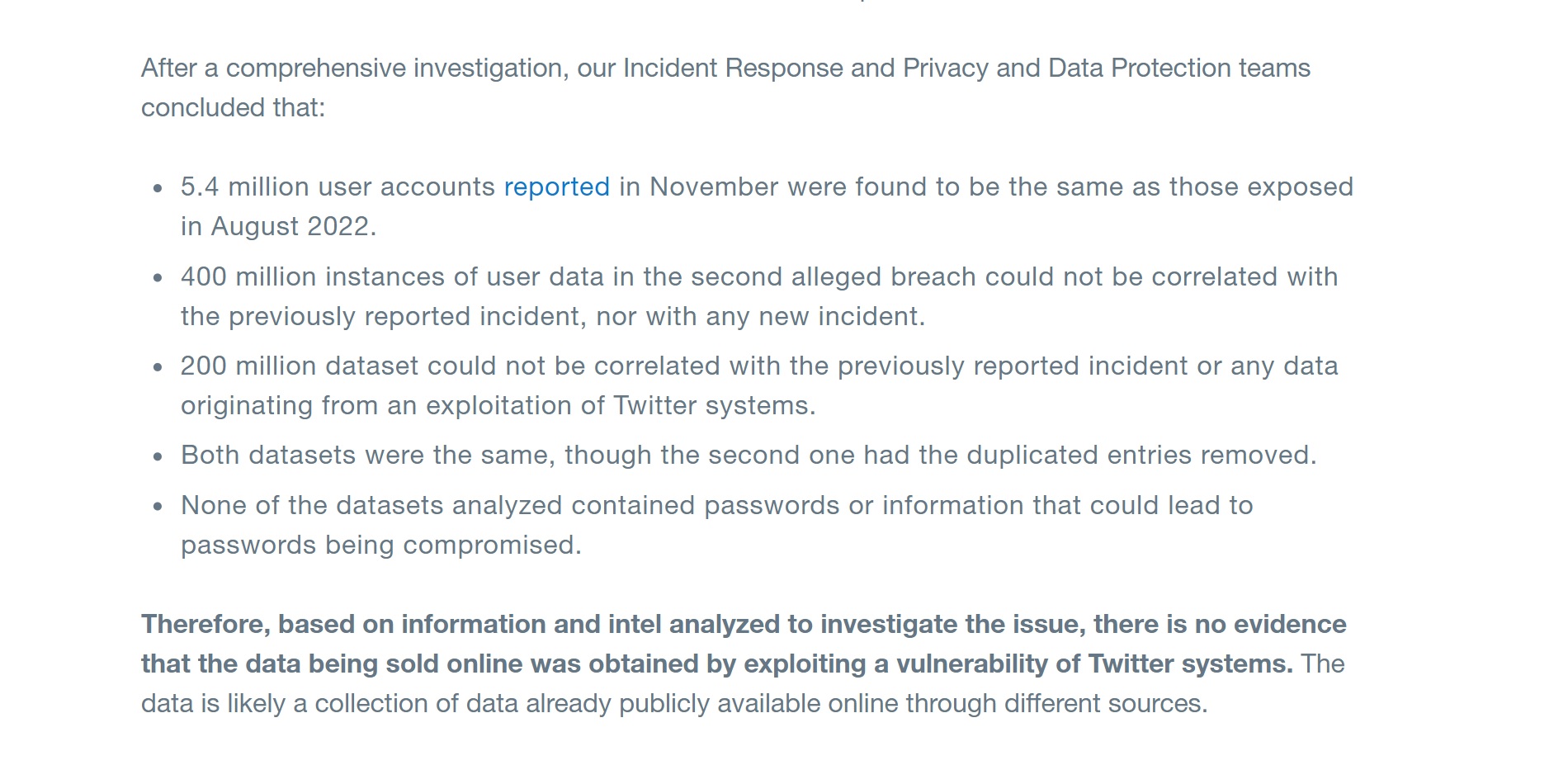
In response to this, Twitter revealed a weblog submit on Jan. 11 claiming that the dataset was NOT obtained by exploiting a safety flaw in its methods. Nonetheless, as we have talked about on the outset, we predict Twitter’s stuffed with it — and now we have extra data why we imagine the social media large is mendacity.
Why Twitter is probably going mendacity
After conducting a “thorough investigation,” the social media large concluded that the e-mail addresses and Twitter accounts featured within the dataset of over 200 million Twitter customers are seemingly a “assortment of knowledge already publicly accessible on-line by way of completely different sources,” including that it’s innocent for the leak.
Nonetheless, what Twitter is conveniently leaving out, in line with the anon who de-duplicated the infamous dataset (they go by the moniker ThinkingOne), is that there is a hyperlink between the emails and Twitter accounts within the information dump.
“[That link] will not be public, and if that hyperlink was obtained by way of Twitter, it will be a vulnerability/exploit (as they acknowledged in August 2022),” ThinkingOne instructed Laptop computer Magazine in an electronic mail.
In different phrases, this is not only a random dataset of electronic mail addresses and Twitter handles. These electronic mail addresses are paired with the right Twitter handles. For instance, you probably have a Twitter account the place you are being your genuine self, however you’ve gotten one other the place you need to stay nameless, the dataset will seemingly reveal that you’re the proprietor of each accounts as a result of they’re linked to the identical electronic mail deal with.
ThinkingOne did attempt to give Twitter the advantage of the doubt, although, operating by way of one other risk of how one might get hold of a knowledge dump of Twitter handles with right pairings to electronic mail addresses with out exploiting a vulnerability:
“The one different believable risk I can consider is that somebody took a large electronic mail record, a large record of Twitter accounts and matched them probably utilizing information enrichment (e.g., actual names recognized to be related to the emails),” ThinkingOne stated, however added that this does not maintain water. “There are over 10,000 Twitter accounts with the true title of simply ‘Sarah’ and a username of ‘Sarah’ adopted by numbers. There’s simply no means somebody might know which was which.”
ThinkingOne stated that it is also attainable that Twitter equipped these electronic mail/username pairings to a third-party firm, and in consequence, it received leaked. But when that is the case, Twitter continues to be mistaken in saying that the information is “already publicly accessible.”
It is value noting {that a} New York resident, searching for class-action standing, sued Twitter for being negligent along with his private information and is requesting {that a} third-party safety auditor examine the information dump of greater than 200 million customers.
Twitter’s received a number of explaining to do, so we reached out to the social media large to get a remark. We’ve not heard again but, but when we do, we’ll replace this text.


