Buyer engagement platform Twilio on Monday disclosed {that a} “subtle” risk actor gained “unauthorized entry” utilizing an SMS-based phishing marketing campaign aimed toward its employees to achieve data on a “restricted quantity” of accounts.
The social-engineering assault was bent on stealing worker credentials, the corporate mentioned, calling the as-yet-unidentified adversary “well-organized” and “methodical of their actions.” The incident got here to mild on August 4.
“This broad based mostly assault in opposition to our worker base succeeded in fooling some staff into offering their credentials,” it mentioned in a discover. “The attackers then used the stolen credentials to achieve entry to a few of our inner programs, the place they have been capable of entry sure buyer knowledge.”
The communications big has 268,000 energetic buyer accounts, and counts firms like Airbnb, Field, Dell, DoorDash, eBay, Glassdoor, Lyft, Salesforce, Stripe, Twitter, Uber, VMware, Yelp, and Zendesk amongst its shoppers. It additionally owns the favored two-factor authentication (2FA) service Authy.
Twilio, which remains to be persevering with its investigation into the hack, famous it is working instantly with prospects who have been impacted. It did not disclose the size of the assault, the variety of worker accounts that have been compromised, or what varieties of knowledge might have been accessed.
Phishing schemes, each leveraging e mail and SMS, are recognized to lean on aggressive scare techniques to coerce victims into handing over their delicate data. That is no exception.
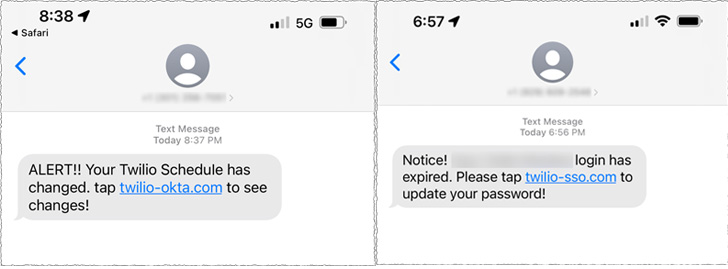
The SMS messages are mentioned to have been despatched to each present and former staff masquerading as coming from its IT division, luring them with password expiry notifications to click on on malicious hyperlinks.
The URLs included phrases corresponding to “Twilio,”https://thehackernews.com/2022/08/”Okta,” and “SSO” (quick for single sign-on) to extend the prospect of success and redirected the victims to a phony web site that impersonated the corporate’s sign-in web page. It is not instantly clear if the breached accounts have been secured by 2FA protections.
Twilio mentioned the messages originated from U.S. provider networks and that it labored with the telecom service and internet hosting suppliers to close down the scheme and the assault infrastructure used within the marketing campaign. The takedown efforts, nonetheless, have been offset by the attackers migrating to different carriers and internet hosting suppliers.
“Moreover, the risk actors appeared to have subtle skills to match worker names from sources with their cellphone numbers,” it famous.
The San Francisco-based agency has since revoked entry to the compromised worker accounts to mitigate the assault, including it is inspecting extra technical safeguards as a safety measure.
The disclosure arrives as spear-phishing continues to be a significant risk confronted by enterprises. Final month, it emerged that the $620 million Axie Infinity hack was the consequence of one in all its former staff getting tricked by a fraudulent job supply on LinkedIn.