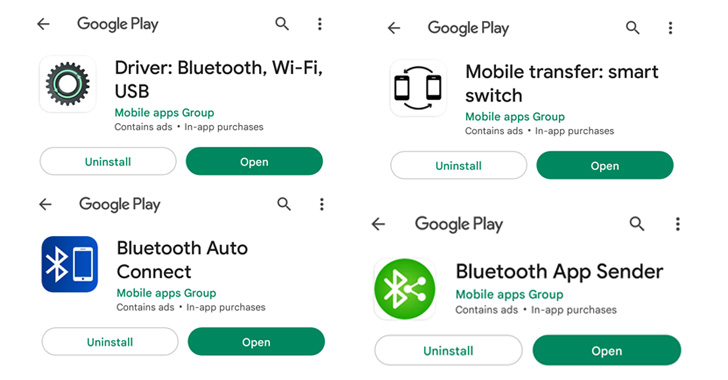
A set of 4 Android apps launched by the identical developer has been found directing victims to malicious web sites as a part of an adware and information-stealing marketing campaign.
The apps, revealed by a developer named Cell apps Group and at the moment obtainable on the Play Retailer, have been collectively downloaded over a million occasions.
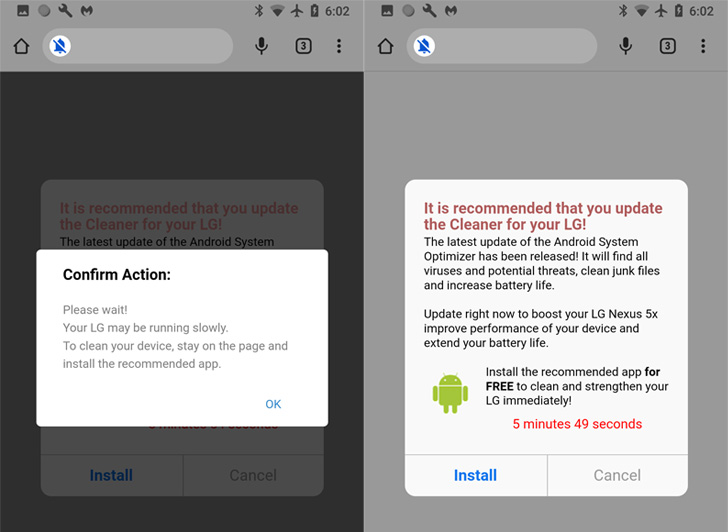
In accordance with Malwarebytes, the web sites are designed to generate revenues by means of pay-per-click adverts, and worse, immediate customers to put in cleaner apps on their telephones with the aim of deploying extra malware.
The listing of apps is as follows –
- Bluetooth App Sender (com.bluetooth.share.app) – 50,000+ downloads
- Bluetooth Auto Join (com.bluetooth.autoconnect.anybtdevices) – 1,000,000+ downloads
- Driver: Bluetooth, Wi-Fi, USB (com.driver.finder.bluetooth.wifi.usb) – 10,000+ downloads
- Cell switch: good swap (com.cell.quicker.switch.good.swap) – 1,000+ downloads
It is no shock that malicious apps have devised new methods to get previous Google Play Retailer safety protections. One of many extra fashionable ways adopted by menace actors is to introduce time-based delays to hide their malicious conduct.
Malwarebytes’ evaluation discovered the apps to have an roughly four-day ready interval earlier than opening the primary phishing web site in Chrome browser, after which proceed to launch extra tabs each two hours.
The apps are a part of a broader malware operation known as HiddenAds, which has been lively since no less than June 2019 and has a monitor document of illicitly incomes revenues by redirecting customers to ads.
The findings additionally come as researchers from Guardio Labs disclosed particulars of a malvertising marketing campaign dubbed Dormant Colours that leverages rogue Google Chrome and Microsoft Edge extensions to hijack consumer search queries to an actor-controlled area.