Phishing scams are sneaky and sometimes troublesome to detect. Most of these cyber assaults contain cybercriminals sending emails, texts, or web sites that look like from a trusted supply however are usually not. The objective of one of these social engineering tactic is to trick unsuspecting customers into giving up delicate info.
In reality, phishing is likely one of the most typical and profitable hacker assaults. One of many contributing elements is that 97% of persons are unable to acknowledge one of these rip-off.
On this weblog submit, we’ll have a look at various kinds of phishing and how one can keep away from being a sufferer of this type of cybercrime.
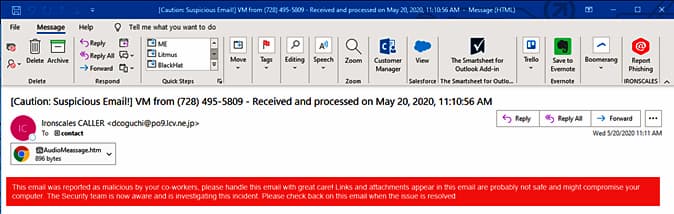
E-mail Phishing
The commonest type of phishing is e-mail phishing, which has been round for the reason that Nineteen Nineties. In reality, a phishing assault happens in a single out of each 99 emails, in line with an examination of greater than 55 million emails. These rip-off emails are despatched by hackers to any tackle they’ll discover. Usually, the e-mail service supplier warns you about potential phishing scams and requests that you just reply rapidly.
In some circumstances, an e-mail could ask you to click on on a hyperlink and confirm your account. Reliable firms won’t ever ask you to offer delicate info through e-mail. For those who get a message that appears suspicious, don’t open the e-mail or click on on any hyperlinks. As an alternative, contact the corporate by means of a special channel, equivalent to their customer support quantity or web site.
If you’d like some additional safety, attempt utilizing a program that may aid you detect phishing emails. Some e-mail safety options are designed to guard you towards phishing assaults. These instruments can scan your emails for suspicious hyperlinks, domains, and different indicators that the e-mail is likely to be a phishing rip-off. It’s a good way to forestall cybercriminals from getting what they need.
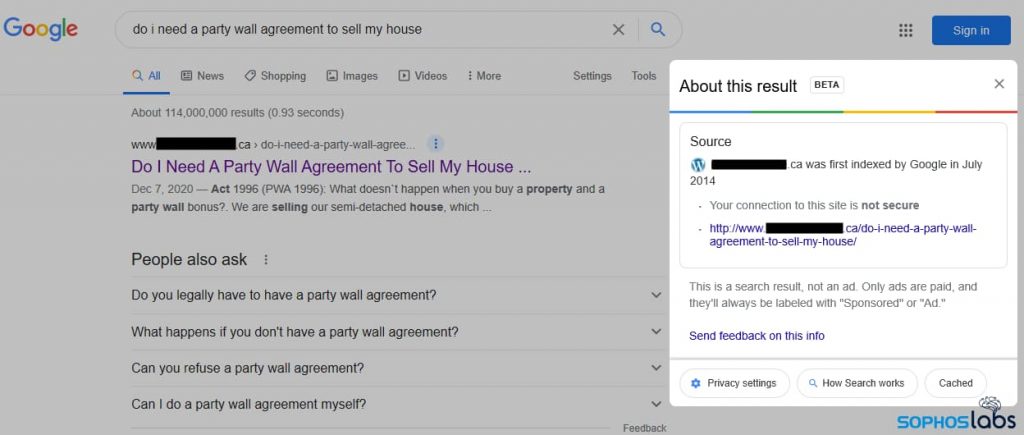
Search Engine Phishing
In search engine phishing, generally known as search engine marketing poisoning or search engine marketing Trojans (and recently ransomware), hackers try to rank extremely in a search engine. Your go to to the hacker’s web site is facilitated by clicking on the hyperlink that’s introduced inside the search engine.
In one of these state of affairs, you want to belief your cyber instincts. All the time listen if the web site URL is wrong or sounds suspicious. If in case you have any doubts, don’t go to it.
One other resolution right here can be to dam suspicious domains with an extension.
Anti-phishing extensions are useful as they’ll warn you in case you’re visiting a suspicious web site.
A number of the well-known anti-phishing companies which can be accessible to guard your privateness from on-line phishing makes an attempt embrace extensions like Netcraft and Cryptonite.
Vishing
Vishing, typically often called voice phishing, is the usage of telephones to hold out phishing assaults. A vishing cellphone name goals to trick you (it just lately tricked one in every of Cisco workers) into disclosing monetary and private info, together with account numbers and passwords.
The fraudster could assert that your account has been compromised, symbolize your financial institution or regulation enforcement, or provide to help you in putting in software program.
One of the simplest ways to guard your self from vishing is thru data, as even password managers can’t assist to keep away from human errors. Grasp up if an individual or a recording calls you and asks for private info. Name the corporate instantly to verify the request if the decision seems to be from a dependable supply.
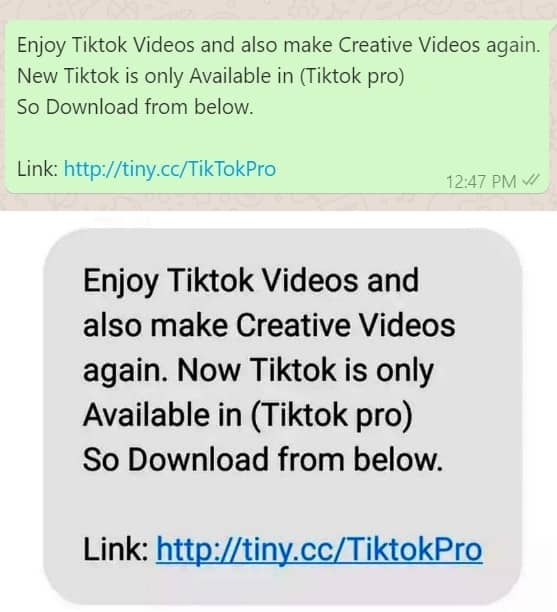
Smishing
Smishing is a sort of phishing assault the place SMS is used. Attributable to the truth that persons are extra inclined to consider a message acquired by means of a messaging app on their cellphone than one despatched through e-mail, it’s actually widespread.
Your title and site may very well be utilized by the smishing felony to deal with you particularly. The message could sound extra genuine due to that. Normally, a smishing message will include a hyperlink to the web site. The hyperlink might take you to a web site that steals login credentials or malware that may infect your cellphone instantly.
The malware can then be used to discreetly talk personal info to a server beneath the attacker’s management or to spy in your smartphone exercise. To keep away from that, it’s best to take into accout just a few issues to raised defend your self from these threats. Firstly:
- Don’t reply.
- Name your financial institution or service provider if uncertain.
- Keep away from opening hyperlinks despatched through textual content message.
- Ensure to verify the variety of the message, as unknown numbers are often pretend.
Conclusion
Info is energy, and data is the important thing to stopping your self from turning into a sufferer of phishing assaults. The extra you realize about these cyber-based threats, like phishing, vishing, and smishing, and the way they have an effect on your on-line life, the much less probably you’re to fall sufferer to 1.
Associated Information
- How you can detect phishing photographs in emails
- Phishing Scams: 5 Glorious Ideas That Will Defend You
- Scammers Leveraging Microsoft Group GIFs in Phishing Assaults
- Hoxhunt Primed to Unfold Gamified Phishing Consciousness within the Enterprise
- ‘Essential Notification’ Phishing Rip-off Concentrating on American Categorical Clients