In Half 1 of our tales of real-world cloud assaults, we examined real-world examples of two frequent cloud assaults. The primary ranging from a software-as-a-service (SaaS) market, demonstrating the breadth of potential entry vectors for cloud assaults and the way it can allow lateral motion into different cloud sources, together with an organization’s AWS setting. The second cloud assault demonstrated how attackers take over cloud infrastructure to inject cryptominers for his or her revenue.
As we’ve got witnessed, extra assaults have moved onto the cloud, so it was solely a matter of time earlier than ransomware assaults did, too. Let’s take a look at two eventualities the place attackers leveraged ransomware to realize earnings, and the way distinctive cloud capabilities helped victims keep away from paying the ransom.
MongoDB Ransomware Demand Mitigated
The primary case (or fairly circumstances, as this assault has appeared quite a few occasions) is the infamous MongoDB ransomware, which has been ongoing for years. The assault itself is easy— attackers use a script to scan the web (and now, frequent cloud vendor deal with areas) for hosts working MongoDB uncovered to the web. The attackers then strive to hook up with the MongoDB with the empty admin password. If profitable, the assault erases the database and replaces it with a double ransomware be aware: pay, and your knowledge will likely be returned; do not pay, and your knowledge will likely be leaked.
Intervention was essential to deal with the second a part of the extortion scheme: knowledge leakage. Fortunately, the corporate had knowledge backups, so restoration was simple, however the database contained appreciable quantities of personally identifiable info (PII), which, if leaked, can be a serious disaster for the corporate. This pressured them into the place of both paying a hefty ransom or coping with the press. MongoDB default logging, sadly, can’t present a definitive reply relating to the information accessed, as not all potential sorts of knowledge assortment instructions are logged by default.
That is the place the cloud infrastructure grew to become a bonus. Whereas MongoDB could not log each command, AWS logs the visitors going out and in of servers, as a result of it prices for community prices. Correlating the community visitors going out of the attacked server with the occasions when the attackers had been linked to the compromised MongoDB server offered proof that the information couldn’t have been downloaded by the attackers.
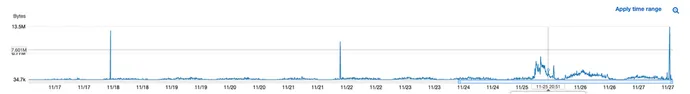
This allowed the corporate to keep away from paying the ransom and ignore the menace. As anticipated, nothing additional was heard from the attackers.
Mitigating Ransomware in a Cloud Atmosphere
One other firm skilled an assault on its primary servers working on AWS EC2, the place it was hit by a ransomware Trojan, not not like these seen on on-premises servers. As typically happens lately, this was one other double-extortion ransomware assault and the corporate wanted assist coping with each points.
Fortunately, as a result of firm’s cloud structure and preparedness, there have been AWS snapshots of the setting going again 14 days. The attackers had been unaware of the snapshots and had not disabled them of their assault. This allowed the corporate to right away revert to the day earlier than the information encryption, resolving the primary a part of the assault with minimal effort. That also left two challenges to take care of: the potential knowledge leak and the eradication of the attackers from the setting.
To deal with these challenges, there was a full investigation of the breach, which turned out to be fairly complicated as a result of hybrid nature of their setting. The attackers compromised a single account with restricted entry, utilized by an IT individual. They then recognized a legacy on-premises server the place that particular person was an admin and used it to take over the Okta service account, permitting privilege escalation. Lastly, utilizing a decommissioned VPN service, they had been in a position to hop to the cloud setting. Utilizing the elevated privileges, they took over the EC2 servers and put in the malware.
The investigation yielded two important findings. The primary was the assault timeline. It confirmed that the compromise of all hosts occurred earlier than the earliest snapshots had been taken, indicating that the recovered servers had been compromised and couldn’t be used. New servers had been put in, the information was transferred to them, and the unique affected servers had been purged.
The second discovering was much more shocking. Malware evaluation recognized that the attackers used rclone.exe to repeat the information to a distant location. The connection credentials had been hardcoded within the malware, so the corporate was ready to hook up with the identical location, determine, and take away their information, eliminating the attackers’ entry to the information, eradicating the extortion side of the assault.
Cloud Breaches Are Right here to Keep
As these real-life eventualities reveal, attackers are infiltrating the cloud and cloud breaches are on the rise. It is time for organizations to organize for cloud incidents. Cybercriminals are leveraging cloud capabilities in assaults, and you must use them, too, to guard your group and forestall a disaster from hitting the headlines.