In keeping with the 2022 Malwarebytes Menace assessment, 40M Home windows enterprise computer systems’ threats have been detected in 2021. And malware evaluation is critical to fight and keep away from this sort of assault. On this article, we are going to break down the objective of malicious packages’ investigation and how one can do malware evaluation with a sandbox.
What’s malware evaluation?
Malware evaluation is a means of finding out a malicious pattern. Through the research, a researcher’s objective is to know a computer virus’s sort, features, code, and potential risks. Obtain the knowledge group wants to reply to the intrusion.
Outcomes of research that you just get:
- how malware works: for those who examine the code of this system and its algorithm, it is possible for you to to cease it from infecting the entire system.
- traits of this system: enhance detection by utilizing information on malware like its household, sort, model, and so on.
- what’s the objective of malware: set off the pattern’s execution to take a look at what information it’s focused at, however in fact, do it in a secure setting.
- who’s behind the assault: get the IPs, origin, used TTPs, and different footprints that hackers conceal.
- a plan on how one can forestall this sort of assault.
Forms of malware evaluation
 |
| Static and dynamic malware evaluation |
Key steps of malware evaluation
Throughout these 5 steps, the principle focus of the investigation is to seek out out as a lot as attainable concerning the malicious pattern, the execution algorithm, and the best way malware works in varied situations.
We consider that the simplest technique to investigate malicious software program is to combine static and dynamic strategies. Here’s a brief information on how one can do malware evaluation. Simply comply with the next steps:
Step 1. Set your digital machine
You may customise a VM with particular necessities like a browser, Microsoft Workplace, select OS bitness, and locale. Add instruments for the evaluation and set up them in your VM: FakeNet, MITM proxy, Tor, VPN. However we are able to do it simply in ANY.RUN sandbox.
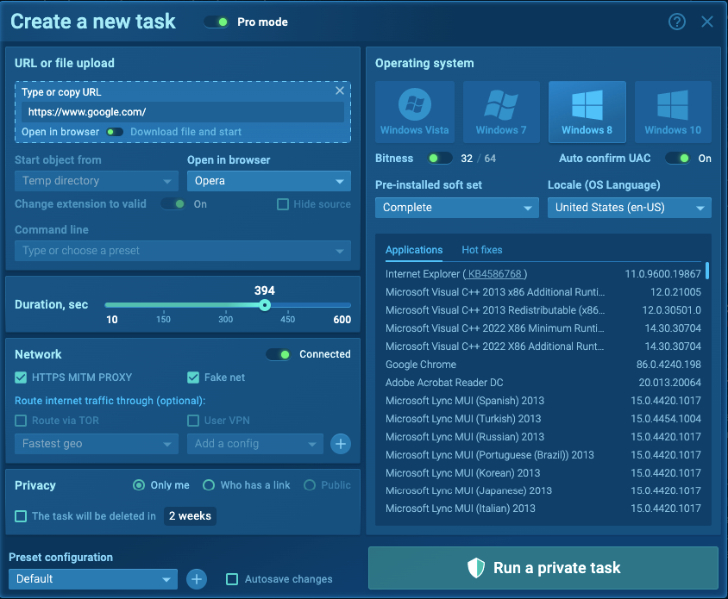 |
| VM customization in ANY.RUN |
Step 2. Overview static properties
It is a stage for static malware evaluation. Study the executable file with out operating it: test the strings to know malware’s performance. Hashes, strings, and headers’ content material will present an outline of malware intentions.
For instance, on the screenshot, we might see hashes, PE Header, mime sort, and different information of the Formbook pattern. To take a quick thought about performance, we are able to check out the Import part in a pattern for malware evaluation, the place all imported DLLs are listed.
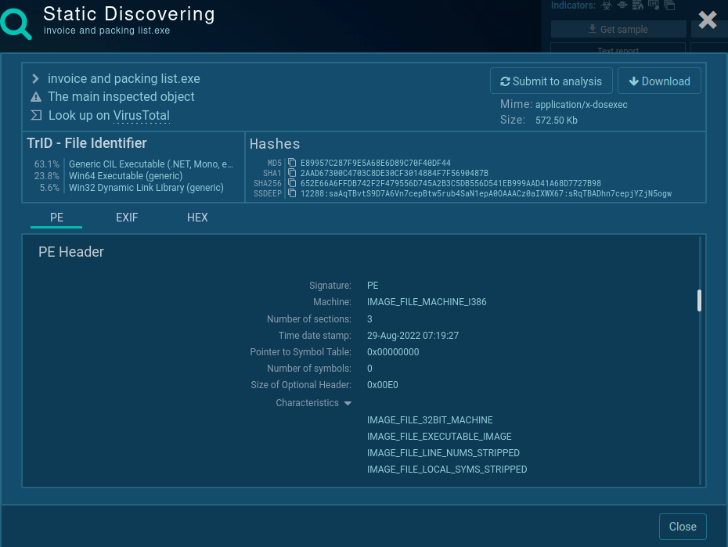 |
| Static discovering of the PE file |
Step 3. Monitor malware habits
Right here is the dynamic method to malware evaluation. Add a malware pattern in a secure digital setting. Work together with malware on to make this system act and observe its execution. Test the community site visitors, file modifications, and registry modifications. And every other suspicious occasions.
In our on-line sandbox pattern, we could have a look contained in the community stream to obtain the criminal’s credentials information to C2 and data that was stolen from an contaminated machine.
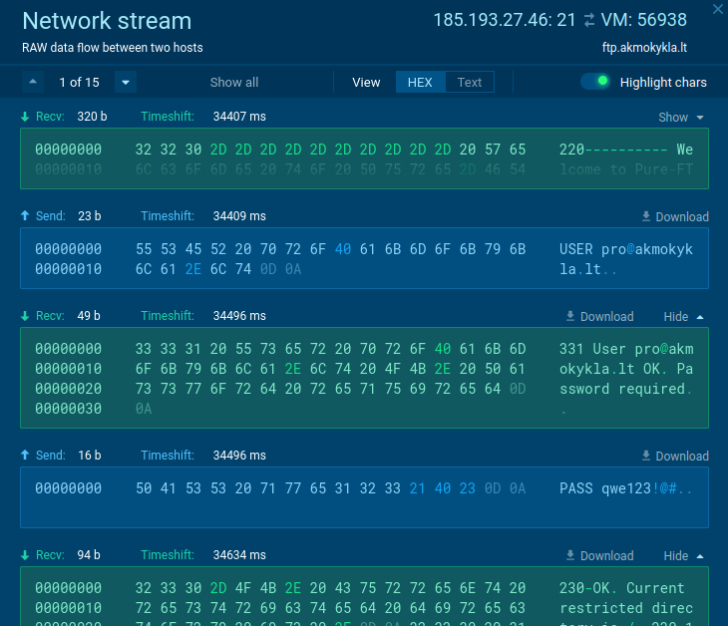 |
| Attacker’s credentials |
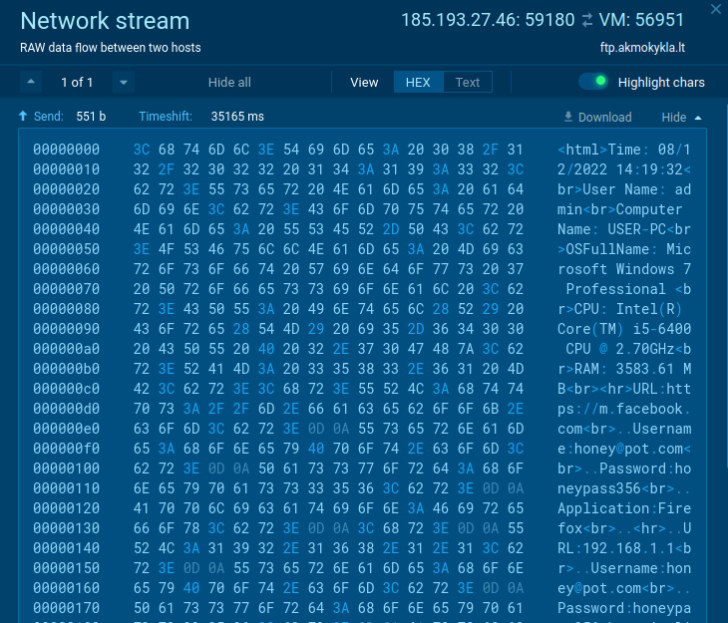 |
| Overview of the stolen information |
Step 4. Break down the code
If menace actors obfuscated or packed the code, use deobfuscation strategies and reverse engineering to disclose the code. Determine capabilities that weren’t uncovered throughout earlier steps. Even simply on the lookout for a operate utilized by malware, chances are you’ll say so much about its performance. For instance, operate “InternetOpenUrlA” states that this malware will make a reference to some exterior server.
Extra instruments, like debuggers and disassemblers, are required at this stage.
Step 5. Write a malware report.
Embody all of your findings and information that you just came upon. Present the next data:
- Abstract of your analysis with the computer virus’s title, origin, and key options.
- Basic details about malware sort, file’s title, measurement, hashes, and antivirus detection capacities.
- Description of malicious habits, the algorithm of an infection, spreading strategies, information assortment, and methods of С2 communication.
- Crucial OS bitness, software program, executables and initialization recordsdata, DLLs, IP addresses, and scripts.
- Overview of the habits actions like the place it steals credentials from, if it modifies, drops, or installs recordsdata, reads values, and checks the language.
- Outcomes of code evaluation, headers information.
- Screenshots, logs, string traces, excerpts, and so on.
- IOCs.
Interactive malware evaluation
The trendy antiviruses and firewalls could not handle with unknown threats akin to focused assaults, zero-day vulnerabilities, superior malicious packages, and risks with unknown signatures. All these challenges will be solved by an interactive sandbox.
Interactive is the important thing benefit of our service. With ANY.RUN you possibly can work with a suspicious pattern straight as for those who opened it in your private pc: click on, run, print, reboot. You may work with the delayed malware execution and work out completely different situations to get efficient outcomes.
Throughout your investigation, you possibly can:
- Get interactive entry: work with VM as in your private pc: use a mouse, enter information, reboot the system, and open recordsdata.
- Change the settings: pre-installed delicate set, a number of OSs with completely different bitness and builds are prepared for you.
- Select instruments in your VM: FakeNet, MITM proxy, Tor, OpenVPN.
- Analysis community connections: intercept packets and get a listing of IP addresses.
- Prompt entry to the evaluation: the VM instantly begins the evaluation course of.
- Monitor methods processes: observe malware habits in real-time.
- Gather IOCs: IP addresses, domains, hashes, and others can be found.
- Get MITRE ATT@CK matrix: assessment TTP intimately.
- Have a course of graph: consider all processes in a graph.
- Obtain a ready-made malware report: print all information in a handy format.
All of those options assist to disclose refined malware and see the anatomy of the assault in real-time.
Write the “HACKERNEWS” promo code within the e mail topic at help@any.run and get 14 days of ANY.RUN premium subscription at no cost!
Attempt to crack malware utilizing an interactive method. In case you use ANY.RUN sandbox, you are able to do malware evaluation and revel in quick outcomes, a easy analysis course of, examine even refined malware, and get detailed studies. Comply with the steps, use good instruments and hunt malware efficiently.


