The Nationwide Institute of Requirements and Know-how (NIST) is likely one of the standard-bearers in world cybersecurity. The U.S.-based institute’s cybersecurity framework helps organizations of all sizes perceive, handle, and scale back their cyber-risk ranges and higher defend their knowledge. Its significance within the struggle in opposition to cyberattacks cannot be overstated.
Whereas NIST hasn’t instantly developed requirements associated to securing the SaaS ecosystem, they’re instrumental in the best way we method SaaS safety.
NIST just lately launched its Information to a Safe Enterprise Community Panorama. In it, they focus on the transformation from on-premise networks to a number of cloud servers. Entry to those servers, and the accompanying SaaS apps, is thru each safe and unsecured gadgets and areas throughout disparate geography.
The transfer to the cloud has successfully obliterated the community perimeter. In consequence, firms have elevated their assault floor and are experiencing an escalation of assaults that span throughout community boundaries.
Moderately than concentrate on network-centric safety, safety should take a three-pronged method. The consumer, endpoint, and utility are keys to defending knowledge. This new paradigm emphasizes the significance of id, location, and contextual knowledge related to the consumer, gadget, and repair.
Learn the way Adaptive Defend can assist implement NIST compliance.
The Instruments to Meet At present’s Challenges
At present’s safety instruments have to scale to fulfill the amount, velocity, and number of in the present day’s functions. They should combine seamlessly with SaaS functions and supply protection for the complete SaaS stack.
To be efficient, these instruments want to attenuate human intervention for monitoring and remediation. Automation is crucial for an ecosystem that calls for safe configurations for every consumer account that has entry to the applying. Giant organizations might have thousands and thousands of configurations to safe throughout their total SaaS stack; closing them manually is an inconceivable activity.
SaaS Monitoring
SaaS safety instruments should be capable of combine with all of the apps on the stack and determine every utility by way of the SaaS app’s APIs. As soon as related, it should monitor the safety configurations, staying alert to any adjustments. This configuration drift can have extreme penalties, because it exposes SaaS functions by eradicating the safeguards put in place to forestall unauthorized entry. It must repeatedly monitor functions, and subject alerts as danger will increase.
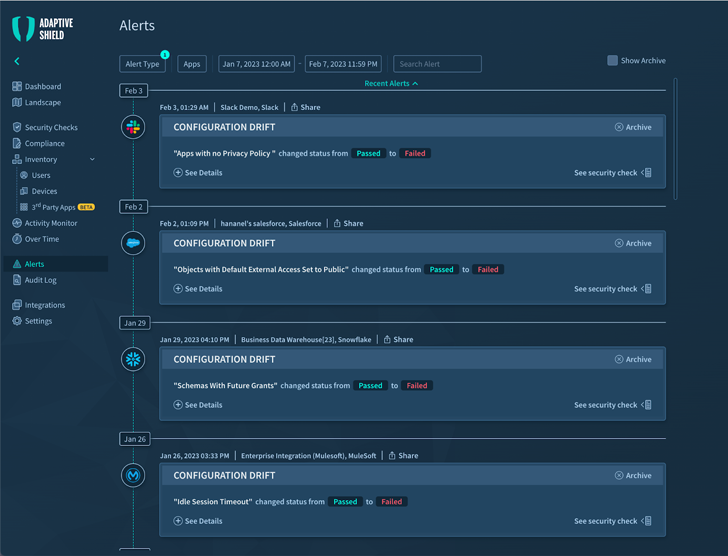 |
| Determine 1. SaaS Monitoring in Adaptive Defend Platform |
Contextual Knowledge
Efficient SaaS safety instruments use contextual knowledge to detect threats to the applying and its knowledge. These threats can come from people and machines and will have entry to the system utilizing verified credentials.
Contextual knowledge from throughout the SaaS stack can assist determine paradoxical journey, spikes in failed authentication makes an attempt from the identical IP tackle for a number of accounts, or makes an attempt the place automated instruments check weak and customary passwords in opposition to identified consumer names. It may possibly additionally acknowledge malicious third-party functions which might be considerably overprivileged for his or her performance.
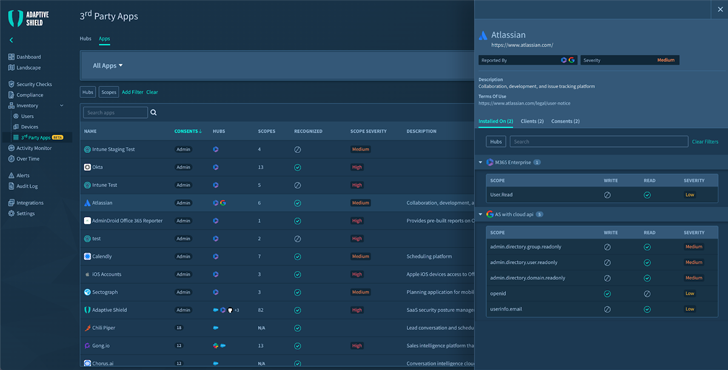 |
| Determine 2. Contextual Knowledge as Seen in Adaptive Defend |
Get a demo of how Adaptive Defend can assist safe your SaaS stack
Gadget Administration
On this planet of SaaS, the gadgets symbolize the community perimeter. Accessing SaaS functions with gadgets which have poor hygiene can put all the information in danger. Compromised gadgets can hand over login credentials to menace actors, who can leverage that into breaching and stealing knowledge.
Efficient SaaS safety instruments companion with endpoint safety suppliers to make sure that the gadgets that entry SaaS apps have an up-to-date working system, all software program has been up to date, and any patches have been utilized.
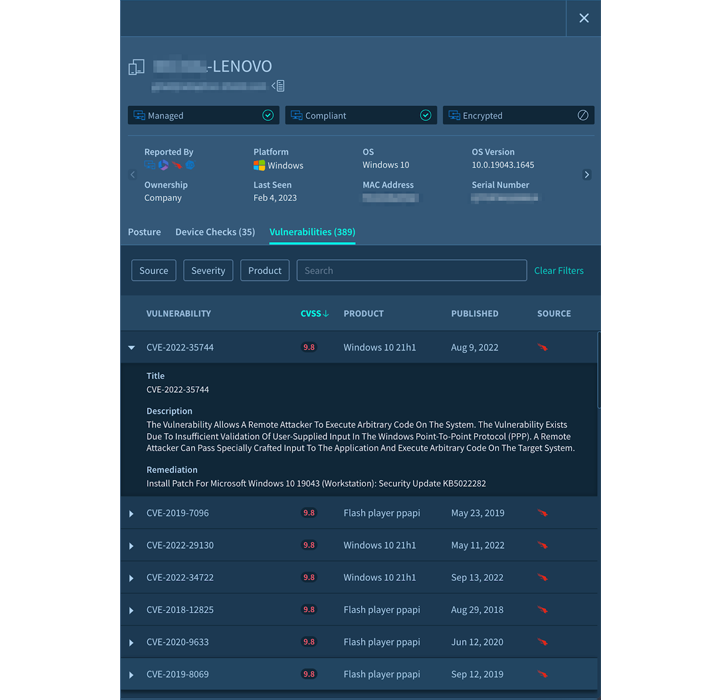 |
| Determine 3. Gadget Administration in Adaptive Defend Platform |
Person Authentication
Whereas gadgets could be the perimeter, consumer ID is the barrier stopping unfettered entry to firm knowledge. Entry must be given utilizing a zero-trust method. All entry must be granted by way of an SSO related to an enterprise-managed IdP. Organizations ought to reinforce this entryway with a phishing-resistant MFA authenticator.
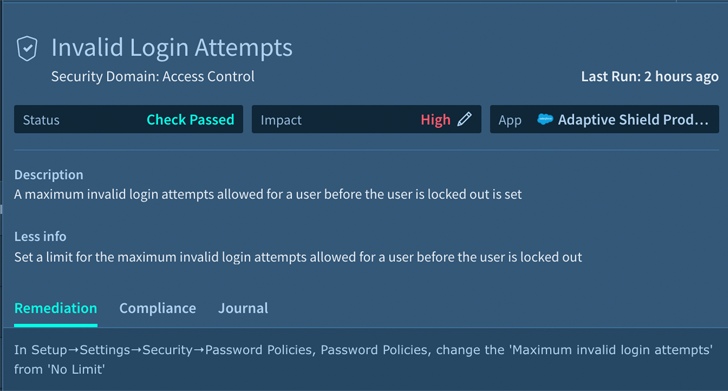 |
| Determine 4. Invalid Login Makes an attempt Alert |
Assembly NIST Requirements
Efficient SSPM platforms are constructed on strong safety checks that overview every SaaS configuration to make sure they’re optimized for defense. Sometimes, safety setting suggestions are influenced closely by NIST’s cybersecurity method, and their steering allows SSPM distributors to watch and observe utilization, customers, and behaviors, in addition to determine threats.
See how Adaptive Defend’s SSPM may defend your SaaS stack


