Usually, when menace actors look to infiltrate a corporation’s SaaS apps, they give the impression of being to SaaS app misconfigurations as a way of entry. Nonetheless, workers now use their private units, whether or not their telephones or laptops, and so forth., to get their jobs carried out. If the gadget’s hygiene is less than par, it will increase the danger for the group and widens the assault floor for dangerous actors. And so, Endpoint (Machine) Safety — via EDR, XDR, and vulnerability administration options – has arisen as a important think about SaaS Safety.
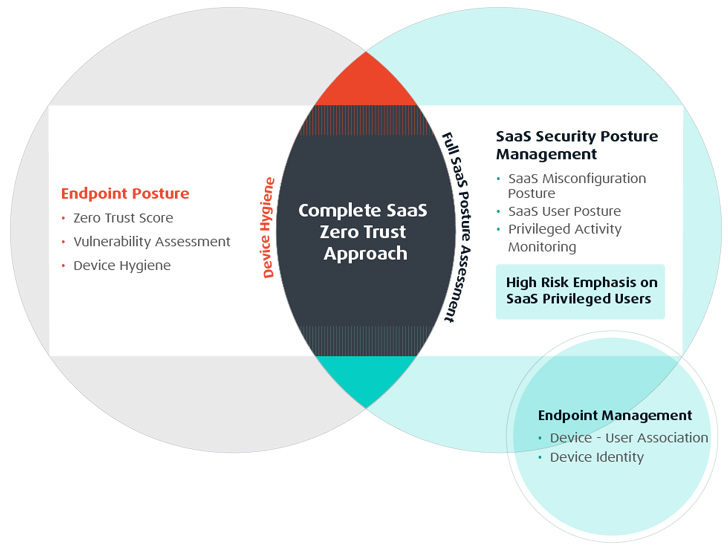
The problem in remediating the threats posed by endpoints and units lies within the means to correlate between the SaaS app customers, their roles, and permissions with their related units’ compliance and integrity ranges. This end-to-end strategy is what’s wanted for the group to implement a holistic, zero-trust strategy for his or her SaaS Safety.
Not a easy feat, nonetheless, automated SaaS Safety Posture Administration options, like Adaptive Protect, can now present visibility that correlates the SaaS consumer and their related units with the gadget’s hygiene rating.
Click on right here to schedule a ten min. demo to see how one can safe your SaaS stack
Excessive-Threat Units
How do you classify high-risk units within the context of SaaS safety?
Units which might be owned, or utilized by customers with excessive ranges of permission to the corporate’s core SaaS apps. For instance, somebody who has excessive ranges of entry to the corporate’s CRM can current a excessive danger to the corporate if their gadget is weak and this must be remediated instantly. These high-risk units function a important menace vector to a corporation’s SaaS setting.
Safety groups ought to repeatedly map units to their customers and their related permissions to get a deal with on which units/customers pose the very best danger.
Correlate Between Person, App, and Machine
As talked about, the extra privileged the consumer, the upper their gadget is in danger. To achieve deep observability into the consumer, app and gadget posture, safety groups must test the hygiene of their customers’ units, for instance, up-to-date OS configurations, and any vulnerabilities. With that evaluation and rating in hand, safety groups can map and monitor the consumer’s SaaS app entry (along with, after all, securing the SaaS apps themselves).
As soon as these cross-references are in place and accessible, organizations can allow “gentle” enforcement enhancements, via insurance policies and organizational greatest practices. This manner safety groups can monitor dangers and threats with out severely limiting the consumer.
Get the Zero Belief Strategy
Zero-trust is an idea a lot batted about in cybersecurity vernacular at present. Whereas many think about it a buzzword, its that means represents an necessary strategy that may not be emphasised sufficient. To wholly safe the group’s SaaS stack, end-to-end, and repeatedly, requires a holistic and automatic resolution.
An SSPM resolution, like Adaptive Protect, has been constructed to resolve not solely the necessity for administration of the SaaS app configurations themselves, but additionally the units the group’s workers use. (To not point out third social gathering app entry — and you may learn extra about that right here.) When built-in with MDM (cell gadget administration) resolution, Adaptive Protect will pull the gadget knowledge and map the gadget to the proprietor.
By wanting on the gadget posture whereas conducting a SaaS safety evaluation, organizations can obtain a holistic zero belief strategy.
Discover ways to get rid of weak hyperlinks in your SaaS safety now.