Understanding the connection between GRC and cybersecurity
When speaking about cybersecurity, Governance, Danger, and Compliance (GRC) is usually thought of the least thrilling a part of enterprise safety. Nonetheless, its significance cannot be ignored, and that is why.
Whereas cybersecurity focuses on the technical facet of defending techniques, networks, gadgets, and knowledge, GRC is the instrument that may assist all the group perceive and talk find out how to do it.
What does it imply?
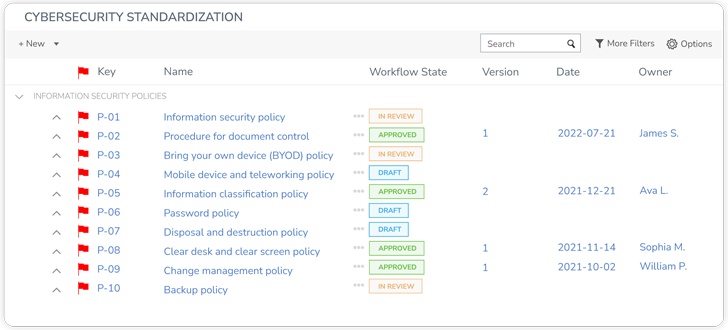
GRC instruments like StandardFusion assist firms outline and implement the very best practices, procedures, and governance to make sure everybody understands the dangers related to their actions and the way they will have an effect on enterprise safety, compliance, and success.
In easy phrases, GRC is the medium for creating consciousness round cybersecurity’s greatest practices to scale back dangers and obtain enterprise targets.
Why is cybersecurity extra related than ever earlier than
Cybersecurity goals to guard delicate enterprise knowledge, mental property, private and well being data, and different firm techniques from cyber-attacks and threats. Nonetheless, this process has develop into more and more more durable over the previous few years.
Why is that?
Properly, due to the ever-increasing world connectivity, new hybrid work fashions, the popularization of cloud companies, and the evolution of know-how, amongst others. Though all of those are nice from a enterprise perspective, they introduce new dangers and challenges.
Here is the reality:
Cybersecurity has at all times been a essential a part of organizations; nevertheless, in at the moment’s technological and interconnected panorama, they cannot exist with out it, a minimum of in the long run.
Understanding the ideas of GRC
Governance, Danger, and Compliance (GRC) is a enterprise technique for managing an organization’s general governance, enterprise danger administration, and regulatory compliance.
From a cybersecurity standpoint, GRC is a structured strategy to aligning IT (individuals and operations) with enterprise aims whereas successfully managing dangers and assembly regulatory wants.
On this context, to realize enterprise aims and maximize the corporate’s backside line, organizations must comply with the very best practices and procedures. For this reason GRC exists… to mitigate any menace to productiveness and the corporate’s worth by creating requirements, insurance policies, laws, and processes.
Extra importantly, GRC helps construct belief within the group. This belief comes from improved efficiencies, higher communication, staff’ confidence to share data, and enhanced enterprise outcomes.
That is not all.
GRC empowers firms to create a tradition of worth, giving everybody the schooling and company to grasp how they will defend the enterprise’s worth, repute and make higher selections.
The essential function of GRC in cybersecurity
Organizations should align individuals, techniques, and applied sciences with enterprise aims to realize strong and efficient cybersecurity. This implies everybody ought to know and take the correct actions when executing their duties — it is all about consciousness and data.
Governance, Danger, and Compliance is the very best instrument to create an built-in system that focuses on reaching aims whereas addressing dangers and performing with integrity.
GRC is essential as a result of it helps cybersecurity with important enterprise actions, resembling:
- Standardizing the very best practices for everybody to behave with integrity and safety.
- Assigns roles and tasks to enterprise models and customers, enhancing communication.
- Serving to with the implementation of knowledge manipulation procedures.
- Unifies vocabulary throughout departments and groups.
- Supporting inside audits and encourages steady management monitoring.
- Aiding with danger mitigation internally and externally
- Supporting assembly business and authorities laws.
GRC additionally supplies a framework to combine safety and privateness with the group’s general targets. Why is that this vital? As a result of it permits companies to make knowledgeable selections concerning knowledge safety dangers rapidly whereas mitigating the danger of compromising privateness.
The function of GRC in cybersecurity – technical advantages
The next are a few of the important advantages GRC presents cybersecurity:
Third-party vendor choice: Many organizations will use a third-party scorecard to collect fundamental details about potential distributors. This data contains: Company repute, financials, community safety, historical past of cyber breaches, geographic location, and extra. A strong GRC mannequin would help IT and safety groups choose and vet potential third-party distributors. Extra importantly, GRC will help the creation of vendor assessments and mitigation methods.
Danger mitigation: IT can use GRC to grasp the scope of cybersecurity and doc the strengths and limitations of the present safety program. GRC permits organizations to stipulate and act on various kinds of threats, potential damages, mitigation plans, and danger therapies.
Regulatory compliance: GRC is important in protecting compliance within the loop as new laws evolve worldwide. Furthermore, it brings these evolving adjustments to the safety group’s consideration forward of time, offering time to plan and reply. Total, GRC will assist develop and handle the insurance policies, laws, and requirements to satisfy the often-updated enterprise and business laws.
Audit help: Fashionable organizations lengthen their procedures and protocols to offer proof and audit materials to their auditors. Making certain processes and greatest practices are properly documented will present that the home is stored so as. Vital audit materials might embody: Incident response, cybersecurity consciousness coaching, inside management take a look at outcomes, cybersecurity compliance opinions, and extra. GRC helps craft and preserve a single supply of reality for compliance that enables everybody to be on the fitting web page.
Knowledge privateness: GRC helps organizations keep on high of the ever-changing panorama of privateness laws. How? by permitting the IT group to make sure that the suitable safety, logging, geographic storage, and many others. are in place to defend prospects’ and staff’ knowledge.
Visibility: GRC’s built-in strategy permits firms to get visibility into each facet of their safety compliance applications. That is important because it allows totally different models, managers, and personnel to see the large image and make data-drive and knowledgeable selections.
In abstract:
A well-planned GRC program allows organizations to:
- Acquire and preserve high-quality data
- Enhance choice making
- Promote collaboration
- Enhance accountability
- Construct a powerful tradition
- Enhance effectivity and agility
- Present visibility
- Reduces prices by supporting appropriate investments
- Enhance integration
- Defend the corporate’s worth and repute
GRC and Cybersecurity: Why do firms want an built-in strategy?
Integrating GRC and cybersecurity is crucial for organizations that need to construct a long-term, profitable safety technique. Apart from quicker communication, congruent metrics, collaboration, and decision-making, the combination of GRC and cybersecurity presents different distinct benefits.
An built-in strategy minimizes handbook enter and the potential for human error, lowering prices and giving organizations extra time to create extra worth for the enterprise.
Extra importantly, a powerful integration helps the board to obviously and comprehensively visualize the group’s safety posture. By understanding the cross-functional posture, enterprise administrators can inform higher safety tales to convey belief to prospects and empower staff.
To sum up:
GRC and cybersecurity work hand in hand towards a lower-risk future and worth creation, — they cannot exist with out one another. Whereas cybersecurity goals to guard techniques, networks, and knowledge (from a technical perspective), GRC communicates the very best technique and practices to realize so.
With an built-in strategy, organizations will:
- Enhance efficiencies
- Improve safety posture
- Inform higher safety tales
- Enhance visibility throughout the board
- Enhance help from management
- Keep away from compliance/regulatory fines
- IT and safety groups set the tone for all the firm
- Hand in hand towards a lower-risk future
Empowering cybersecurity by means of GRC – methodology
The OCEG has developed this Functionality Mannequin (Crimson Ebook) as an open-source methodology that merges the sub-disciplines of governance, danger, audit, compliance, ethics/tradition, and IT right into a unified strategy.
Organizations can evolve this customary to deal with particular conditions, from small tasks to organization-wide rollouts. Some examples are:
- Anti-corruption tasks
- Enterprise continuity
- Third-party administration
The mannequin is vital to framing conversations about GRC capabilities with the board, senior executives, and managers. Additionally, organizations would possibly use this GRC Functionality Mannequin with extra particular useful frameworks, resembling: ISO, COSO, ISACA, IIA, NIST, and others.
The GRC Functionality Mannequin encourages organizations to doc greatest practices to:
- Unify vocabulary throughout disciplines
- Outline frequent parts and components
- Outline frequent data necessities
- Standardize practices for issues like insurance policies and coaching
- Determine communication for everybody concerned.
Now, let’s examine the way it works.
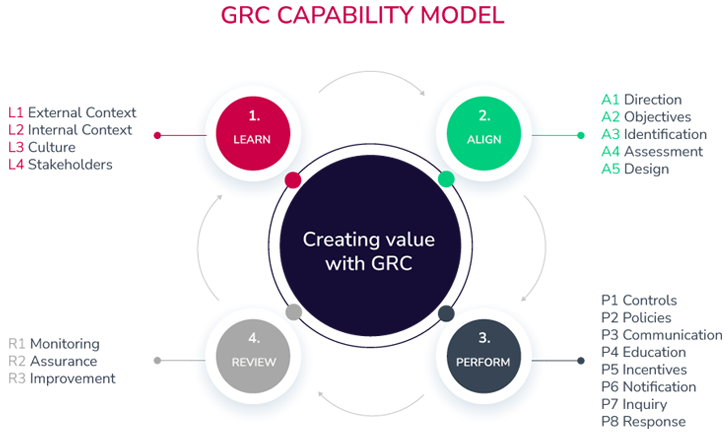
The Functionality Mannequin has 4 elements:
1. Study
The primary thought right here is to establish the enterprise tradition, stakeholders, and group’s enterprise practices to efficiently information their targets, technique, and aims.
As a course of, it might seem like this:
- Studying enterprise plans and targets
- Understanding strategic aims
- Being conscious of the present and future compliance actions
- Connecting with the important thing stakeholders
2. Align
This step focuses on unifying technique with aims and actions with methods. The purpose right here is to have an built-in strategy the place senior management is engaged and helps the method of decision-making.
In easy phrases, this course of wants:
- Align enterprise aims with the technique
- Align executives with stakeholders’ expectations
- Align useful resource allocation planning with aims
3. Carry out
After aligning enterprise targets and aims, it is time to carry out. This step defines implementing acceptable controls and insurance policies, stopping and remediating undesired dangers, and monitoring to detect points as quickly as potential.
4. Assessment
As a closing step, it is crucial to assessment the design and operational efficiency of the present technique and actions. Extra importantly, this step encourages organizations to research aims to continuously improve the built-in GRC actions.
What’s the goal of this mannequin?
To develop a gradual and integral enchancment course of to succeed in optimum efficiency and create worth for the group.
Get your free session with StandardFusion and be taught how one can design an built-in GRC program to strengthen your cybersecurity and defend your group’s worth.