In 2012, the US Federal Bureau of Investigation (FBI) started investigating an inflow of reported fraud incidents involving risk actors rerouting funds to attacker-controlled accounts. In these incidents, victims obtained seemingly legit emails containing requests to change scheduled funds. The risk actors usually impersonated executives or finance and payroll personnel and satisfied victims to reroute funds to a distinct checking account. These first cases of enterprise e-mail compromise (BEC) kicked off a decade of assaults that use this straightforward but extremely efficient scheme. Whereas the risk has advanced, risk actors proceed to make use of phishing assaults to steal credentials after which ship fraudulent invoices soliciting fee. Hundreds of organizations have misplaced billions of {dollars}.
What Have We Discovered within the Previous Decade?
When BEC was first found, legislation enforcement referred to it as “man within the e-mail” fraud. As a result of a lot of the cash on the time was despatched to China, Japan, and South Korea, legislation enforcement believed that the risk actors could possibly be Asia-based organized crime teams. A number of investigations confirmed that these schemes had been linked and that the cash ultimately ended up with risk actors positioned in Nigeria.
BEC fraud emerged from Nigerian organized crime teams that performed operations corresponding to romance scams, advance-fee schemes (also referred to as “Nigerian prince” or “419” scams), and elder fraud. The low barrier to entry and potential for prime payouts attracted extra risk teams. As a result of the technical features of those schemes are comparatively easy, risk actors with little to no technical capabilities may launch profitable assaults.
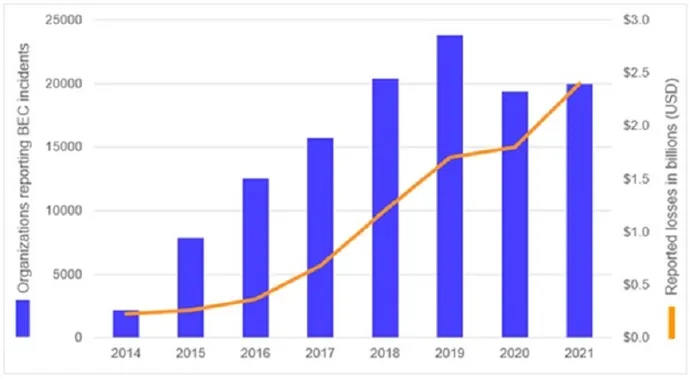
By 2014, cooperation between legislation enforcement and monetary establishments revealed a clearer understanding of BEC schemes. As BEC techniques, methods, and procedures (TTPs) matured, the monetary losses and variety of impacted organizations elevated. In 2014, the US Web Crime Criticism Middle (IC3) obtained 2,417 BEC complaints, with losses totaling $226 million. The numbers grew steadily till a lower in reported incidents in 2020. Nonetheless, that decline was doubtless as a result of COVID-19 pandemic disrupting regular enterprise processes. Momentum resumed in 2021, with 19,954 complaints and adjusted losses of virtually $2.4 billion.
Who Is Connducting BEC Assaults?
To today, the overwhelming majority of BEC operations nonetheless originate in Nigeria. Many Nigerian fraud teams included BEC into their current prison actions and taught different risk actors how one can function the schemes. Every group decided its personal concentrating on, specializing in particular geographic areas, organizational roles (e.g., CFO, finance supervisor, accountant), and industries. In 2016, Secureworks researchers estimated that the GOLD SKYLINE risk group (also referred to as Wire-Wire Group 1) stole roughly $3 million per yr. By 2018, Secureworks analysis indicated that the GOLD GALLEON risk group tried to steal a median of $6.7 million per yr.
Because of the profitability of those schemes, cybercriminals in different areas started adopting BEC. Jap European teams have proven specific sophistication. For instance, Russian cybercrime group Cosmic Lynx has efficiently focused senior-level executives at multinational firms utilizing a twin impersonation scheme. The risk actors impersonate an organization’s CEO after which assume the id of a legit lawyer who’s chargeable for facilitating an acquisition. They immediate victims to ship cash to attacker-controlled accounts.
Regardless of the enlargement of BEC assaults to different areas, none match the amount from Nigeria. The Nigerian fraud ecosystem has grown and flourished over the previous decade. Lots of of social media profiles flaunt wealth obtained from these assaults to recruit individuals in Nigeria, the place the typical month-to-month wage is lower than $800.
Why Is BEC Nonetheless Prevalent?
Regardless of hundreds of BEC arrests, the schemes are nonetheless standard amongst cybercriminals. Enterprise-to-business funds are essentially the most frequent targets, however BEC actors additionally assault different fee strategies. Payroll programs have been manipulated so as to add fictitious workers and ship cash to the related accounts. BEC actors have additionally attacked actual property transactions and rerouted home funds.
Whereas safety controls can detect the compromise of an e-mail account, know-how can solely go to date. Because the risk actor continues to make use of the sufferer’s account or pivots to attacker-controlled infrastructure, detection turns into tougher. Organizations ought to implement technical proactive safety defenses corresponding to multifactor authentication and conditional entry, together with human processes corresponding to verifying requests by way of trusted contact particulars earlier than performing high-risk actions and coaching workers to undertake a “belief however confirm” strategy to e-mail.
Coordination amongst monetary establishments, authorities businesses, personal trade, and legislation enforcement throughout the globe has began to mitigate the impression of BEC assaults. In 2021, the IC3 Restoration Asset Staff helped monetary establishments get well roughly 74% of the stolen funds it pursued. Lowering the profitability of those assaults may reduce the attraction for risk actors and lead to a lower of BEC fraud.


