Just a few days in the past, a buddy and I had been having a relatively partaking dialog that sparked my pleasure. We had been discussing my prospects of turning into a pink teamer as a pure profession development. The explanation I acquired stirred up shouldn’t be that I wish to change both my job or my place, as I’m a cheerful camper being a part of Cymulate’s blue staff.
What upset me was that my buddy couldn’t grasp the concept I needed to maintain working as a blue teamer as a result of, so far as he was involved, the one pure development is to maneuver to the pink staff.
Crimson groups embrace many roles starting from penetration testers to attackers and exploit builders. These roles entice a lot of the buzz, and the numerous certifications revolving round these roles (OSCP, OSEP, CEH) make them appear fancy. Motion pictures normally make hackers the heroes, whereas sometimes ignoring the defending aspect, the complexities and challenges of blue teamers’ roles are far much less identified.
Whereas blue groups’ defending roles won’t sound as fancy and collect little to no buzz, they embrace important and various titles that cowl thrilling and difficult capabilities and, lastly, pay effectively. In truth, Hollywood ought to look into it!
Defending is extra complicated than attacking, and it’s extra essential
Contemplate that you’re a cyber safety defender and that your assigned job is to guard your IT Infrastructure.
- As a defender, you must be taught all kinds of assault mitigation methods to guard your IT infrastructure. Conversely, an attacker can accept gaining proficiency in exploiting only one vulnerability and preserve exploiting that single vulnerability.
- As a defender, you have to be alert 24/7/365 to guard your infrastructure. As an attacker, you both select a particular time/date to launch an assault or run boring brute drive assaults throughout many potential targets.
- As a defender, you should defend all weak hyperlinks in your infrastructure – xerox, machine printer, attendance system, surveillance system, or endpoint utilized by your receptionist – whereas attackers can choose any system related to your infrastructure.
- As a defender, you should comply along with your native regulator whereas performing your every day work. Attackers have the freedom to mess up with legal guidelines and rules.
- As a defender, you’re ready by the pink staff that assists your work by creating assault eventualities to check your capabilities.
Blue groups embrace complicated, difficult, and research-intensive disciplines, and the associated roles will not be stuffed.
Within the dialog talked about above, my buddy assumed that defending roles primarily include monitoring SIEMs (Safety Data and Occasion Administration) and different alerting instruments, which is appropriate for SOC (Safety Operations Heart) analyst roles. Listed below are some atypical Blue Group roles:
- Menace Hunters – Chargeable for proactively looking for threats throughout the group
- Malware Researchers – Chargeable for reverse engineering malware
- Menace Intelligence Researchers – Chargeable for offering intelligence and data relating to future assaults and attributing assaults to particular attackers
- DFIR – Digital Forensics and Incident Responders are accountable for containing and investigating assaults once they occur
These roles are difficult, time intensive, complicated, and demanding. Moreover, they contain working along with the remainder of the blue staff to supply the perfect worth for the group.
In response to a current CSIS survey of IT determination makers throughout eight international locations: “82 % of employers report a scarcity of cybersecurity expertise, and 71 % imagine this expertise hole causes direct and measurable injury to their organizations.” In response to CyberSeek, an initiative funded by the Nationwide Initiative for Cybersecurity Training (NICE), the US confronted a shortfall of virtually 314,000 cybersecurity professionals as of January 2019. To place this in context, the nation’s whole employed cybersecurity workforce is simply 716,000. In response to knowledge derived from job postings, the variety of unfilled cybersecurity jobs has grown by greater than 50 % since 2015. By 2022, the worldwide cybersecurity workforce scarcity has been projected to succeed in upwards of 1.8 million unfilled positions.”
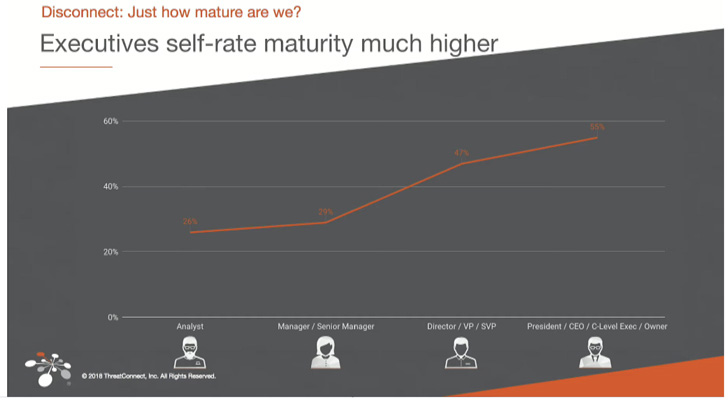
C Stage executives are disconnected from actuality with regards to Inside Blue Groups
The above graph is from a wonderful discuss referred to as “How you can Get Promoted: Creating Metrics to Present How Menace Intel Works – SANS CTI Summit 2019”. It illustrates the disconnect between the high-level executives and “on-the-ground” workers and the way high-level executives assume that their defensive groups are far more mature than their staff self-assessment.
Fixing the Downside
Attempt to show SOC analyst’s new craft
Bringing new and skilled researchers is dear and sophisticated. Maybe organizations ought to attempt to advertise and encourage entry analysts to be taught and experiment with new expertise and applied sciences. Whereas SOC managers would possibly concern that this would possibly intervene with skilled analysts’ every day missions or end in folks leaving the corporate however, paradoxically, it is going to encourage analysts to remain and take a extra lively half in maturing the group’s safety at virtually no additional price.
Cycle workers by positions
Individuals get bored with doing the identical factor daily. Maybe a intelligent technique to preserve workers engaged and strengthen your group is to let folks cycle throughout distinct roles, for instance, by educating risk hunters to conduct risk intelligence work by giving them straightforward assignments or sending them off to programs. One other promising thought is to contain low-tier SOC analysts with actual Incident Response groups and thus advance their expertise. Each organizations and workers profit from such undertakings.
Let our workers see the outcomes of their demanding work
Whether or not low-tier SOC analysts or Prime C-level executives, folks want motivation. Staff want to know whether or not they’re doing their job effectively, and executives want to know their job’s worth and the standard of its execution.
Contemplate methods to measure your Safety Operations Heart:
- How efficient is the SOC at processing necessary alerts?
- How successfully is the SOC gathering related knowledge, coordinating a response, and taking motion?
- How busy is the safety atmosphere, and what’s the scale of actions managed by the SOC?
- How successfully are analysts masking the utmost attainable variety of alerts and threats?
- How sufficient is the SOC capability at every degree, and the way heavy is the workload for various analyst teams?
The desk under comprises extra examples and measures taken from Exabeam.
And, after all, validate your blue staff’s work with steady safety validation instruments equivalent to these on Cymulate’s XSPM platform the place you may automate, customise and scale up assault eventualities and campaigns for quite a lot of safety assessments.
Severely, validating your blue staff’s work each will increase your group’s cyber resilience and supplies quantified measures of your blue staff’s effectiveness throughout time.
Observe: This text is written and contributed by by Dan Lisichkin, Menace Hunter and Menace Intelligence Researcher at Cymulate.