The superior persistent risk (APT) group often called StrongPity has focused Android customers with a trojanized model of the Telegram app via a faux web site that impersonates a video chat service known as Shagle.
“A copycat web site, mimicking the Shagle service, is used to distribute StrongPity’s cell backdoor app,” ESET malware researcher Lukáš Štefanko stated in a technical report. “The app is a modified model of the open supply Telegram app, repackaged with StrongPity backdoor code.”
StrongPity, additionally recognized by the names APT-C-41 and Promethium, is a cyberespionage group lively since at the least 2012, with a majority of its operations targeted on Syria and Turkey. The existence of the group was first publicly reported by Kaspersky in October 2016.
The risk actor’s campaigns have since expanded to embody extra targets throughout Africa, Asia, Europe, and North America, with the intrusions leveraging watering gap assaults and phishing messages to activate the killchain.
One of many fundamental hallmarks of StrongPity is its use of counterfeit web sites that purport to supply all kinds of software program instruments, solely to trick victims into downloading tainted variations of authentic apps.
In December 2021, Minerva Labs disclosed a three-stage assault sequence stemming from the execution of a seemingly benign Notepad++ setup file to in the end ship a backdoor onto contaminated hosts.
That very same 12 months, StrongPity was noticed deploying a bit of Android malware for the primary time by probably breaking into the Syrian e-government portal and changing the official Android APK file with a rogue counterpart.
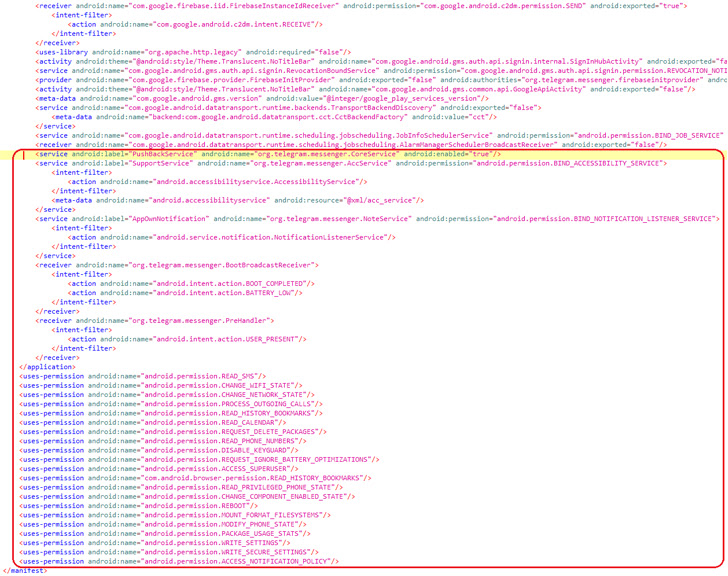
The newest findings from ESET spotlight an analogous modus operandi that is engineered to distribute an up to date model of the Android backdoor payload, which is supplied to report telephone calls, observe gadget areas, and gather SMS messages, name logs, contacts lists, and information.
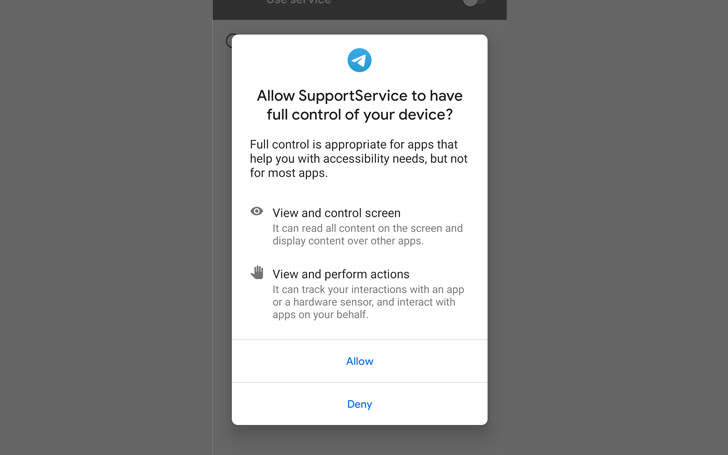
As well as, granting the malware accessibility providers permissions permits it to siphon incoming notifications and messages from varied apps like Gmail, Instagram, Kik, LINE, Messenger, Skype, Snapchat, Telegram, Tinder, Twitter, Viber, and WeChat.
The Slovak cybersecurity firm described the implant as modular and able to downloading extra elements from a distant command-and-control (C2) server in order to accommodate the evolving goals of StrongPity’s campaigns.
The backdoor performance is hid inside a authentic model of Telegram’s Android app that was accessible for obtain round February 25, 2022. That stated, the bogus Shagle web site is now not lively, though indications are that the exercise is “very narrowly focused” because of the lack of telemetry information.
There’s additionally no proof the app was printed on the official Google Play Retailer. It is at the moment not recognized how the potential victims are lured to the faux web site, and if it entails methods like social engineering, search engine poisoning, or fraudulent adverts.
There’s additionally no proof the app (“video.apk“) was printed on the official Google Play Retailer. It is at the moment not recognized how the potential victims are lured to the faux web site, and if it entails methods like social engineering, search engine poisoning, or fraudulent adverts.
“The malicious area was registered on the identical day, so the copycat web site and the faux Shagle app might have been accessible for obtain since that date,” Štefanko identified.
One other notable side of the assault is that the tampered model of Telegram makes use of the identical bundle title as the real Telegram app, which means the backdoored variant can’t be put in on a tool that already has Telegram put in.
“This would possibly imply one in every of two issues – both the risk actor first communicates with potential victims and pushes them to uninstall Telegram from their gadgets whether it is put in, or the marketing campaign focuses on nations the place Telegram utilization is uncommon for communication,” Štefanko stated.