A .NET XOR encrypted cobalt strike aggressor implementation for chisel to make the most of quicker proxy and superior socks5 capabilities.
Why write this?
In my expertise I discovered socks4/socks4a proxies fairly gradual compared to its socks5 counterparts and an absence of implementation of socks5 in most C2 frameworks. There’s a C# wrapper across the go model of chisel referred to as SharpChisel. This wrapper has just a few points and is not maintained to the newest model of chisel. It didn’t permit utilizing shellcode with donut, reflectio n strategies or execute-assembly. I discovered a repair for this utilizing the SharpChisel-NG undertaking.
For the reason that SharpChisel meeting is round 16.7 MB, execute-assembly(has a hidden measurement limitation of 1 MB) and comparable in reminiscence strategies wouldn’t work. To keep up many of the execution in reminiscence I integrated the NetLoader undertaking by Flangvik which is executed through execute-assembly to reflectively host and cargo a XOR encrypted model of SharpChisel with base64 arguments in reminiscence.
As a substitute, it is usually doable to implement comparable C# proxies like SharpSocks by changing the suitable chisel binaries within the undertaking.
Setup
Be aware: If utilizing a Home windows teamserver skip steps 2 and three.
-
Clone/obtain the repository:
git clone https://github.com/m3rcer/Chisel-Strike.git -
Make all binaries executable:
- Set up
Mingw-w64andmono:
- Import
ChiselStrike.cnain cobalt strike utilizing theScript Supervisor
Recompile binaries from the src folder if wanted.
Utilization
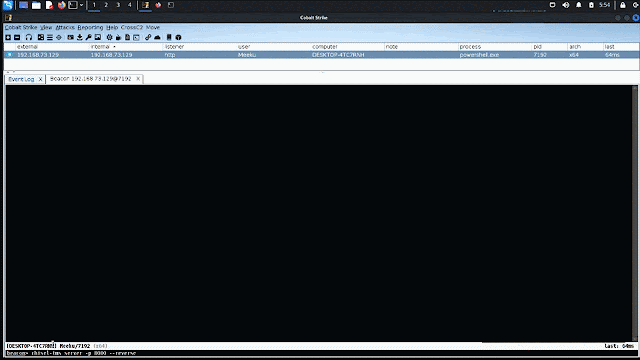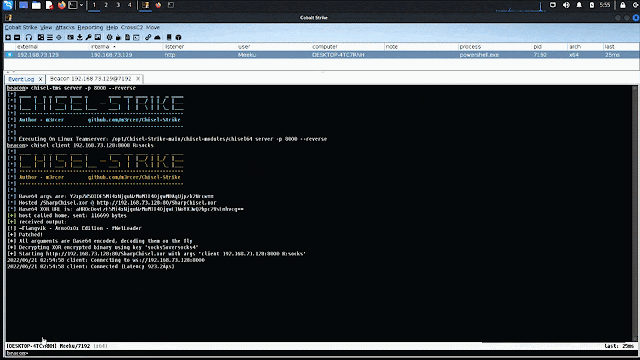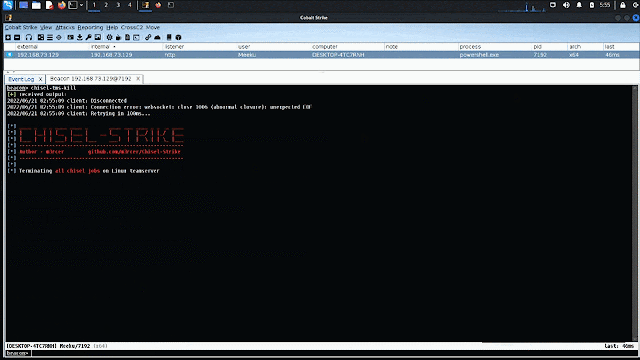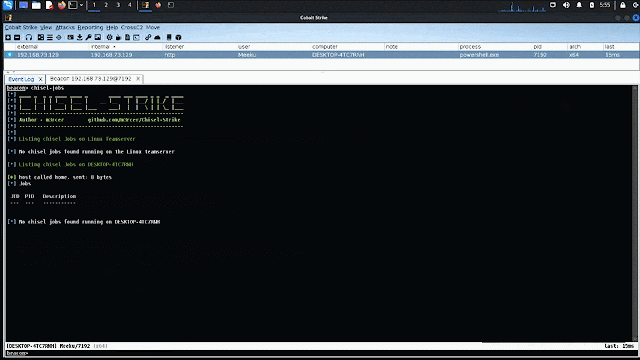
chisel may be executed on each the teamserver (home windows/linux) and the beacon. With both performing because the server/consumer. A standard execution circulate could be to setup a chisel server on the teamserver and create a consumer on the beacon connecting again to the teamserver.
Instructions
-
chisel <consumer/server> <command>: Run Chisel on a beacon -
chisel-tms <consumer/server> <command>: Run Chisel in your teamserver -
chisel-enc: XOR EncryptSharpChisel.exewith a password of selection -
chisel-jobs: Checklist lively chisel jobs on the teamserver and beacon -
chisel-kill: Kill lively chisel jobs on a beacon -
chisel-tms-kill: Kill lively chisel jobs on teamserver
Instance
OPSEC
NetLoader can simply be obfuscated and used to bypass defender utilizing tasks like NimCrypt2 and the like.
But SharpChisel.exe drops a dll on disk attributable to using Costura/Fody packages at a location just like: C:Usersm3rcerAppDataLocalTempCosturaCB9433C24E75EC539BF34CD1AA12B23664main.dll which is detected by defender. It’s suggested to obfuscate chisel dll’s utilizing tasks like gobfuscate within the SharpChisel-NG undertaking and re-build new SharpChisel-NG binaries as proven right here.
TODO
-
Determine a approach to keep away from
SharpChiseldroppingprincipal.dllon disk / Create a brand new C# wrapper for chisel. -
Create a technique to parse command output for the
chisel-tmscommand.
Credit