A China-based superior persistent menace (APT) group is presumably deploying short-lived ransomware households as a decoy to cowl up the true operational and tactical goals behind its campaigns.
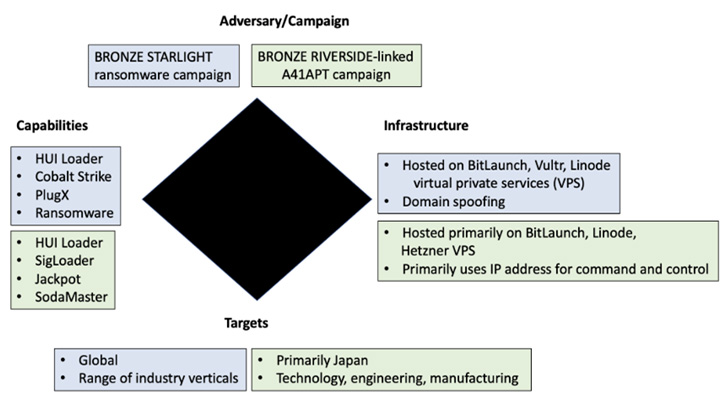
The exercise cluster, attributed to a hacking group dubbed Bronze Starlight by Secureworks, entails the deployment of post-intrusion ransomware similar to LockFile, Atom Silo, Rook, Night time Sky, Pandora, and LockBit 2.0.
“The ransomware might distract incident responders from figuring out the menace actors’ true intent and scale back the probability of attributing the malicious exercise to a government-sponsored Chinese language menace group,” the researchers stated in a brand new report. “In every case, the ransomware targets a small variety of victims over a comparatively transient time period earlier than it ceases operations, apparently completely.”
Bronze Starlight, lively since mid-2021, can also be tracked by Microsoft below the rising menace cluster moniker DEV-0401, with the tech large emphasizing its involvement in all levels of the ransomware assault cycle proper from preliminary entry to the payload deployment.
In contrast to different RaaS teams that buy entry from preliminary entry brokers (IABs) to enter a community, assaults mounted by the actor are characterised by means of unpatched vulnerabilities affecting Change Server, Zoho ManageEngine ADSelfService Plus, Atlassian Confluence (together with the newly disclosed flaw), and Apache Log4j.
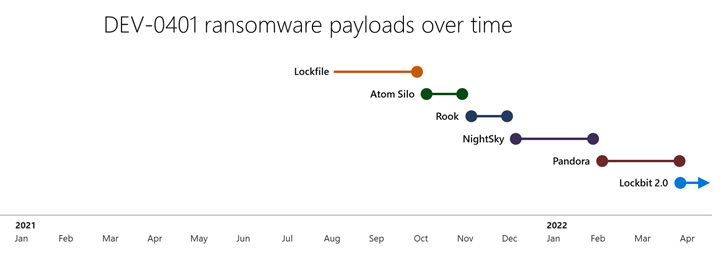
Since August 2021, the group is claimed to have cycled by way of as many as six completely different ransomware strains similar to LockFile (August), Atom Silo (October), Rook (November), Night time Sky (December), Pandora (February 2022), and most just lately LockBit 2.0 (April).
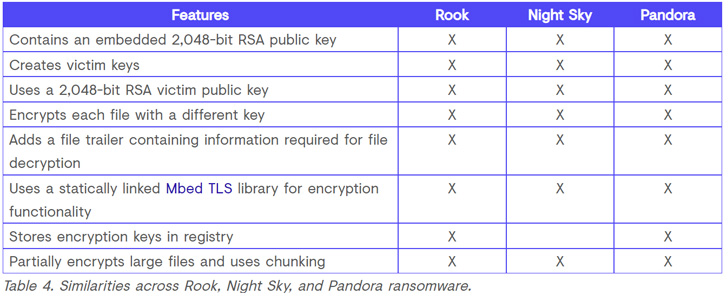
What’s extra, similarities have been uncovered between LockFile and Atom Silo in addition to between Rook, Night time Sky, and Pandora — the latter three derived from Babuk ransomware, whose supply code leaked in September 2021 — indicating the work of a typical actor.
“As a result of DEV-0401 maintains and often rebrands their very own ransomware payloads, they will seem as completely different teams in payload-driven reporting and evade detections and actions in opposition to them,” Microsoft famous final month.
Upon gaining a foothold inside a community, Bronze Starlight is understood to depend on strategies like utilizing Cobalt Strike and Home windows Administration Instrumentation (WMI) for lateral motion, though beginning this month, the group has begun changing Cobalt Strike with the Sliver framework of their assaults.
Different noticed tradecraft pertains to the usage of HUI Loader to launch next-stage encrypted payloads similar to PlugX and Cobalt Strike Beacons, the latter of which is employed to ship the ransomware, however not earlier than acquiring privileged Area Administrator credentials.
“The usage of HUI Loader to load Cobalt Strike Beacon, the Cobalt Strike Beacon configuration data, the C2 infrastructure, and the code overlap recommend that the identical menace group is related to these 5 ransomware households,” the researchers defined.
It is price mentioning that each HUI Loader and PlugX, alongside ShadowPad, are malware traditionally put to make use of by Chinese language nation-state adversarial collectives, lending credence to the likelihood that Bronze Starlight is extra geared in the direction of espionage than instant financial advantages.
On prime of that, the victimology sample spanning throughout the completely different ransomware strains reveals {that a} majority of the targets are more likely to be of extra curiosity to Chinese language government-sponsored teams targeted on long-term intelligence gathering.
The important thing victims embody pharmaceutical firms in Brazil and the U.S., a U.S.-based media group with places of work in China and Hong Kong, digital part designers and producers in Lithuania and Japan, a legislation agency within the U.S., and an aerospace and protection division of an Indian conglomerate.
To that finish, the ransomware operations, in addition to offering a method to exfiltrate knowledge as a part of the double extortion “name-and-shame” scheme, additionally supply twin benefits in that it permits the menace actor to destroy forensic proof of their malicious actions and act as a distraction from knowledge theft.
“It’s believable that Bronze Starlight deploys ransomware as a smokescreen reasonably than for monetary achieve, with the underlying motivation of stealing mental property or conducting espionage,” the researchers stated.