A suspected state-aligned menace actor has been attributed to a brand new set of assaults exploiting the Microsoft Workplace “Follina” vulnerability to focus on authorities entities in Europe and the U.S.
Enterprise safety agency Proofpoint mentioned it blocked makes an attempt at exploiting the distant code execution flaw, which is being tracked CVE-2022-30190 (CVSS rating: 7.8). A minimum of 1,000 phishing messages containing a lure doc have been despatched to the targets.
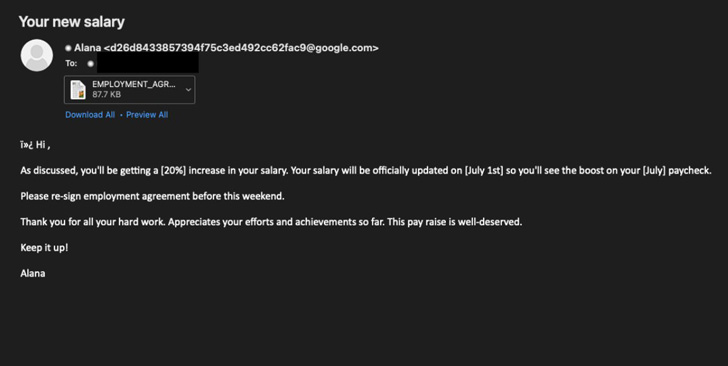
“This marketing campaign masqueraded as a wage improve and utilized an RTF with the exploit payload downloaded from 45.76.53[.]253,” the corporate mentioned in a collection of tweets.
The payload, which manifests within the type of a PowerShell script, is Base64-encoded and features as a downloader to retrieve a second PowerShell script from a distant server named “seller-notification[.]dwell.”
“This script checks for virtualization, steals data from native browsers, mail shoppers and file providers, conducts machine recon after which zips it for exfil[tration] to 45.77.156[.]179,” the corporate added.
The phishing marketing campaign has not been linked to a beforehand identified group, however mentioned it was mounted by a nation-state actor primarily based on the specificity of the focusing on and the PowerShell payload’s wide-ranging reconnaissance capabilities.
The event follows energetic exploitation makes an attempt by a Chinese language menace actor tracked as TA413 to ship weaponized ZIP archives with malware-rigged Microsoft Phrase paperwork.
The Follina vulnerability, which leverages the “ms-msdt:” protocol URI scheme to remotely take management of goal units, stays unpatched, with Microsoft urging clients to disable the protocol to stop the assault vector.
“Proofpoint continues to see focused assaults leveraging CVE-2022-30190,” Sherrod DeGrippo, vp of menace analysis, mentioned in an announcement shared with The Hacker Information.
“The in depth reconnaissance carried out by the second PowerShell script demonstrates an actor thinking about a big number of software program on a goal’s laptop. This, coupled with the tight focusing on of European authorities and native U.S. governments led us to suspect this marketing campaign has a state aligned nexus.”






 – DEV Group
– DEV Group