A brand new assault marketing campaign has focused the gaming and playing sectors since not less than September 2022, simply months previous to the ICE London 2023 gaming trade commerce truthful occasion that is scheduled subsequent week.
Israeli cybersecurity firm Safety Joes is monitoring the exercise cluster underneath the title Ice Breaker, stating the intrusions make use of intelligent social engineering techniques to deploy a JavaScript backdoor.
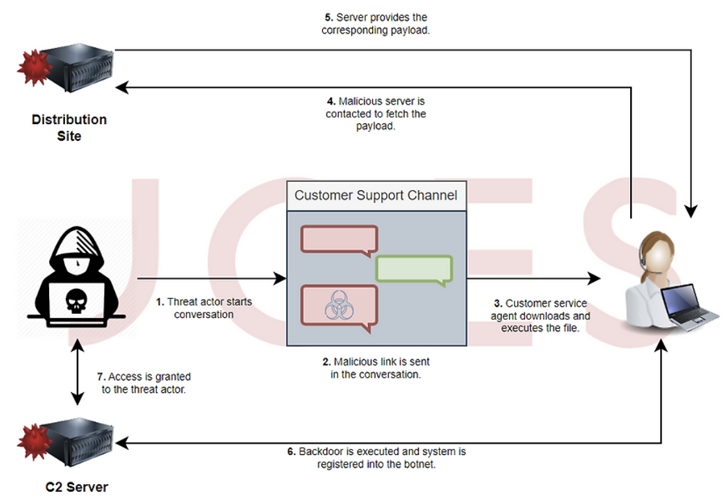
The assault sequence proceeds as follows: The menace actor poses as a buyer whereas initiating a dialog with a assist agent of a gaming web site and urges the person on the opposite finish to open a screenshot picture hosted on Dropbox.
Safety Joes mentioned that the menace actor is “well-aware of the truth that the customer support is human-operated.”
Clicking the malicious hyperlink despatched within the chat results in the retrieval of an LNK payload or, alternatively, a VBScript file as a backup choice, the previous of which is configured to obtain and run an MSI bundle containing a Node.js implant.
The JavaScript file has all of the options of a typical backdoor, enabling the menace actor to enumerate working processes, steal passwords and cookies, exfiltrate arbitrary recordsdata, take screenshots, run VBScript imported from a distant server, and even open a reverse proxy on the compromised host.
Ought to the VBS downloader be executed by the sufferer, the an infection culminates within the deployment of Houdini, a VBS-based distant entry trojan that dates again to 2013.
The menace actors’ origins are at the moment unknown, though they’ve been noticed utilizing damaged English throughout their conversations with customer support brokers. Some indicators of compromise (IoCs) related to the marketing campaign have been beforehand shared by the MalwareHunterTeam in October 2022.
“It is a extremely efficient assault vector for the gaming and playing trade,” Felipe Duarte, senior menace researcher at Safety Joes, mentioned.
“The never-seen-before compiled JavaScript second stage malware is extremely advanced to dissect, exhibiting that we’re coping with a talented menace actor with the potential of being sponsored by an curiosity proprietor.”