Safety researchers are warning of “a trove of delicate info” leaking via urlscan.io, an internet site scanner for suspicious and malicious URLs.
“Delicate URLs to shared paperwork, password reset pages, crew invitations, fee invoices and extra are publicly listed and searchable,” Constructive Safety co-founder, Fabian Bräunlein, stated in a report revealed on November 2, 2022.
The Berlin-based cybersecurity agency stated it began an investigation within the aftermath of a notification despatched by GitHub in February 2022 to an unknown variety of customers about sharing their usernames and personal repository names (i.e., GitHub Pages URLs) to urlscan.io for metadata evaluation as a part of an automatic course of.
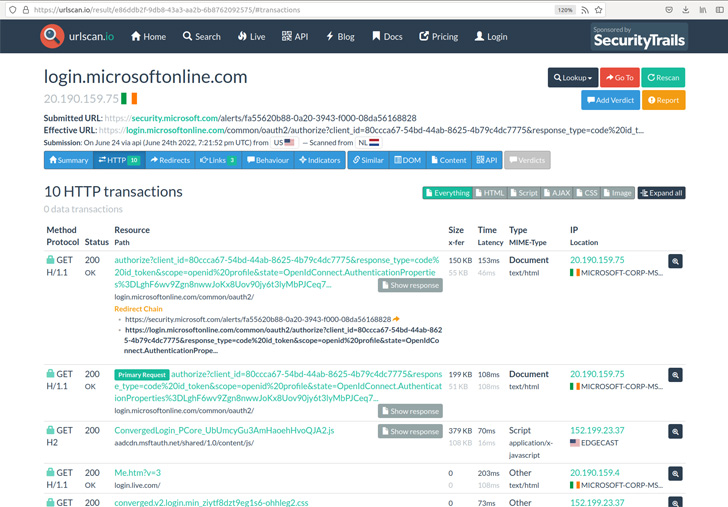
Urlscan.io, which has been described as a sandbox for the online, is built-in into a number of safety options through its API.
“With the kind of integration of this API (for instance through a safety software that scans each incoming e mail and performs a urlscan on all hyperlinks), and the quantity of information within the database, there may be all kinds of delicate knowledge that may be looked for and retrieved by an nameless person,” Bräunlein famous.
This included password reset hyperlinks, e mail unsubscribe hyperlinks, account creation URLs, API keys, details about Telegram bots, DocuSign signing requests, shared Google Drive hyperlinks, Dropbox file transfers, invite hyperlinks to companies like SharePoint, Discord, Zoom, PayPal invoices, Cisco Webex assembly recordings, and even URLs for package deal monitoring.
Bräunlein identified that an preliminary search in February revealed “juicy URLs” belonging to Apple domains, a few of which additionally consisted of publicly-shared hyperlinks to iCloud recordsdata and calendar invite responses, and have since been eliminated.
Apple is claimed to have requested an exclusion of its domains from the URL scans such that outcomes matching sure predefined guidelines are periodically deleted.
Constructive Safety additional added that it reached out to various these leaked e mail addresses, receiving one response from an unnamed group that traced the leak of a DocuSign work contract hyperlink to a misconfiguration of its Safety Orchestration, Automation, and Response (SOAR) resolution, which was being built-in with urlscan.io.
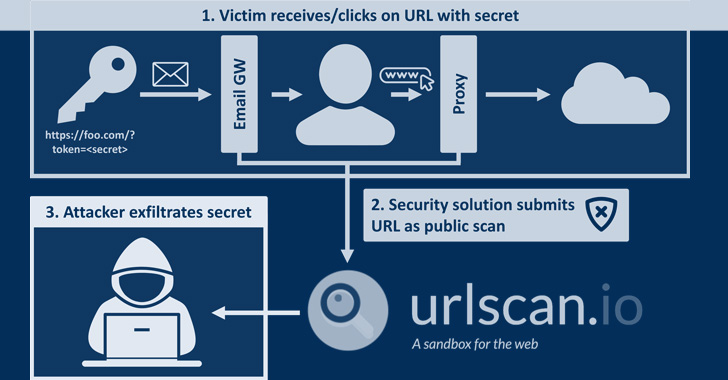
On high of that, the evaluation has additionally discovered that misconfigured safety instruments are submitting any hyperlink acquired through mail as a public scan to urlscan.io.
This might have critical penalties whereby a malicious actor can set off password reset hyperlinks for the affected e mail addresses and exploit the scan outcomes to seize the URLs and take over the accounts by resetting to a password of the attacker’s selection.
To maximise the effectiveness of such an assault, the adversary can search knowledge breach notification websites like Have I Been Pwned to find out the precise companies that have been registered utilizing the e-mail addresses in query.
Urlscan.io, following accountable disclosure from Constructive Safety in July 2022, has urged customers to “perceive the totally different scan visibilities, evaluate your individual scans for personal info, evaluate your automated submission workflows, [and] implement a most scan visibility to your account.”
It has additionally added deletion guidelines to often purge delete previous and future scans matching the search patterns, stating it has area and URL sample blocklists in place to forestall scanning of explicit web sites.
“This info could possibly be utilized by spammers to gather e mail addresses and different private info,” Bräunlein stated. “It could possibly be utilized by cyber criminals to take over accounts and run plausible phishing campaigns.”