The SOVA Android banking trojan is constant to be actively developed with upgraded capabilities to focus on a minimum of 200 cellular functions, together with banking apps and crypto exchanges and wallets, up from 90 apps when it began out.
That is in response to the most recent findings from Italian cybersecurity agency Cleafy, which discovered newer variations of the malware sporting performance to intercept two-factor authentication (2FA) codes, steal cookies, and increase its concentrating on to cowl Australia, Brazil, China, India, the Philippines, and the U.Ok.
SOVA, that means Owl in Russian, got here to gentle in September 2021 when it was noticed hanging monetary and buying apps from the U.S. and Spain for harvesting credentials by overlay assaults by making the most of Android’s Accessibility providers.
In lower than a yr, the trojan has additionally acted as a basis for one more Android malware referred to as MaliBot that is designed to focus on on-line banking and cryptocurrency pockets clients in Spain and Italy.
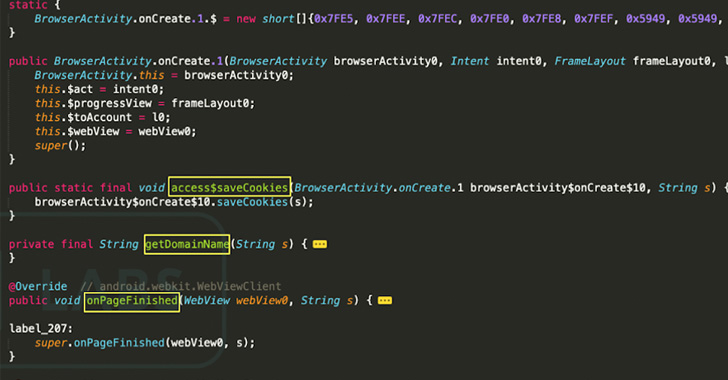
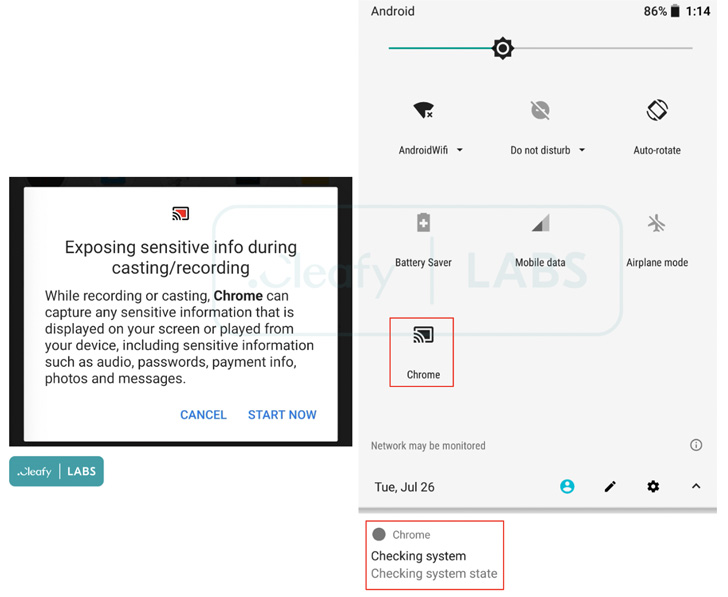
The newest variant of SOVA, dubbed v4 by Cleafy, conceals itself inside faux functions that function logos of official apps like Amazon and Google Chrome to deceive customers into putting in them. Different notable enhancements embody capturing screenshots and recording the machine screens.
“These options, mixed with Accessibility providers, allow [threat actors] to carry out gestures and, consequently, fraudulent actions from the contaminated machine, as we’ve got already seen in different Android Banking Trojans (e.g. Oscorp or BRATA),” Cleafy researchers Francesco Iubatti and Federico Valentini mentioned.
SOVA v4 can also be notable for its effort to assemble delicate info from Binance and Belief Pockets, corresponding to account balances and seed phrases. What’s extra, all of the 13 Russian and Ukraine-based banking apps that have been focused by the malware have since been faraway from the model.
To make issues worse, the replace allows the malware to leverage its wide-ranging permissions to deflect uninstallation makes an attempt by redirecting the sufferer to the house display and displaying the toast message “This app is secured.”
The banking trojan, feature-rich as it’s, can also be anticipated to include a ransomware part within the subsequent iteration, which is presently beneath growth and goals to encrypt all recordsdata saved within the contaminated machine utilizing AES and rename them with the extension “.enc.”
The enhancement can also be prone to make SOVA a formidable risk within the cellular risk panorama.
“The ransomware function is kind of fascinating because it’s nonetheless not a standard one within the Android banking trojans panorama,” the researchers mentioned. “It strongly leverages on the chance that has arisen in recent times, as cellular gadgets turned for most individuals the central storage for private and enterprise information.”