Former members of the Conti cybercrime cartel have been implicated in 5 completely different campaigns focusing on Ukraine from April to August 2022.
The findings, which come from Google’s Risk Evaluation Group (TAG), builds upon a prior report printed in July 2022, detailing the continued cyber exercise aimed on the Japanese European nation amid the continuing Russo-Ukrainian battle.
“UAC-0098 is a risk actor that traditionally delivered the IcedID banking trojan, resulting in human-operated ransomware assaults,” TAG researcher Pierre-Marc Bureau mentioned in a report shared with The Hacker Information.
“The attacker has lately shifted their focus to focusing on Ukrainian organizations, the Ukrainian authorities, and European humanitarian and non-profit organizations.”
UAC-0098 is believed to have functioned as an preliminary entry dealer for ransomware teams similar to Quantum and Conti (aka FIN12, Gold Ulrick, or Wizard Spiker), the previous of which was subsumed by Conti in April 2022.
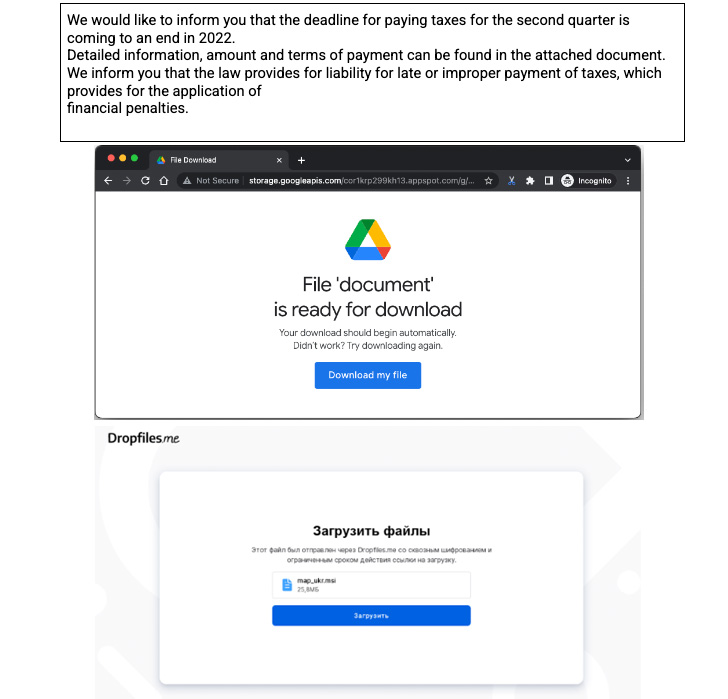
One of many distinguished campaigns undertaken by the group in June 2022 entailed the abuse of Follina vulnerability (CVE-2022-30190) within the Home windows working system to deploy CrescentImp and Cobalt Strike Beacons on to focused hosts in media and significant infrastructure entities.
However this seems to be part of a collection of assaults that commenced manner again in late April 2022, when the group carried out an electronic mail phishing marketing campaign to ship AnchorMail (aka LackeyBuilder), a variant of the TrickBot group’s AnchorDNS implant that makes use of SMTP for command-and-control.
Subsequent phishing campaigns distributing IcedID and Cobalt Strike have been directed towards Ukrainian organizations, repeatedly hanging the hospitality sector, a few of which impersonated the Nationwide Cyber Police of Ukraine or representatives of Elon Musk and StarLink.
Round mid-Might, UAC-0098 can also be mentioned to have leveraged a compromised account of a resort in India to ship malware-laced attachments to organizations working within the hospitality business in Ukraine, earlier than increasing to humanitarian NGOs in Italy.
Comparable assaults have additionally been noticed towards entities within the know-how, retail and authorities sectors, with the IcedID binary hid as a Microsoft replace to set off the an infection. Put up-exploitation steps carried out following a profitable compromise haven’t been recognized.
UAC-0098 is way from the one Conti-affiliated hacking group to set its sights on Ukraine for the reason that onset of the battle. In July 2022, IBM Safety X-Power disclosed that the TrickBot gang orchestrated six completely different campaigns to systematically goal the nation with a plethora of malware.
“UAC-0098 actions are consultant examples of blurring traces between financially motivated and authorities backed teams in Japanese Europe, illustrating a development of risk actors altering their focusing on to align with regional geopolitical pursuits,” Bureau mentioned.
“The group demonstrates sturdy curiosity in breaching companies working within the hospitality business of Ukraine, going so far as launching a number of distinct campaigns towards the identical resort chains.”