Snake Keylogger is again in motion with a model new malspam marketing campaign spreading by way of phishing emails despatched to company IT enterprises’ managers. Bitdefender Antispam Labs found the marketing campaign on 23 August 2022.
What’s a Keylogger?
A keylogger is a sort of malicious software program that information your keystrokes and sends them to a hacker. Keyloggers might be put in in your pc with out your information, often by means of a malicious electronic mail attachment or contaminated web site.
In some instances, attackers might use a bodily keylogger in your gadget in form of a malicious USB drive or a custom-made cellphone charging cable, and so on.
Marketing campaign Evaluation
In line with Bitdefender analysts, the IP addresses used within the assault originated from Vietnam, whereas the marketing campaign’s major targets have been positioned within the USA, and hundreds of inboxes have acquired the phishing electronic mail.
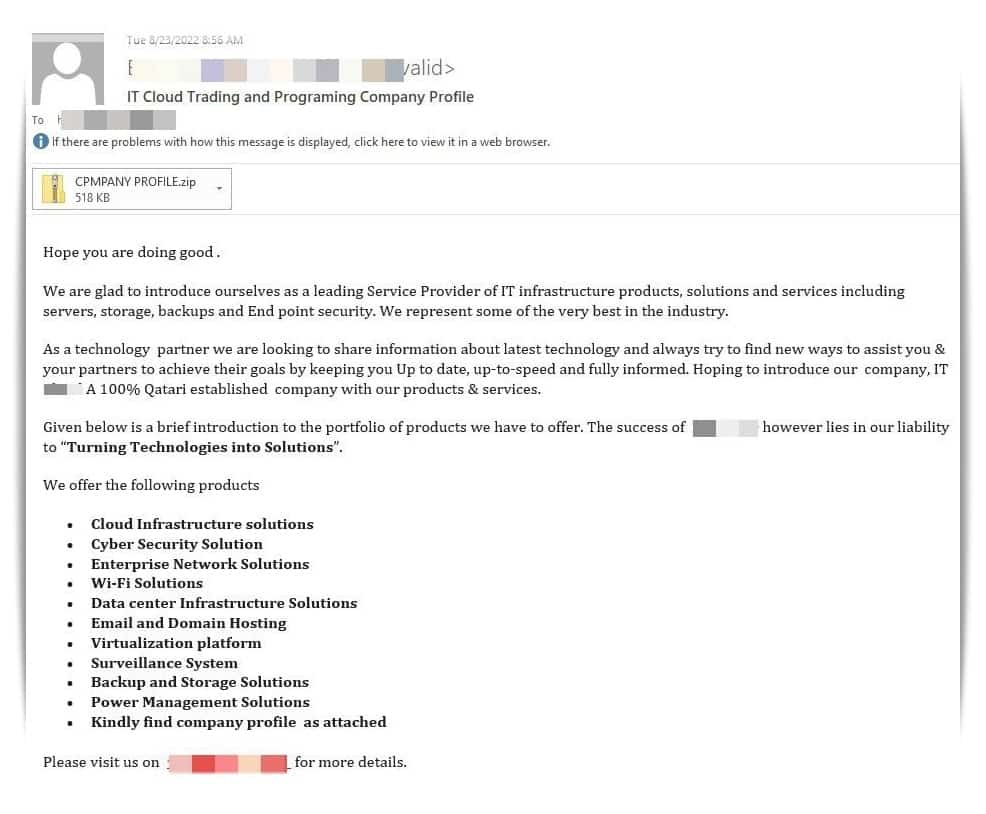
Attackers leverage the company profile of one among Qatar’s main IT and cloud providers suppliers to entice victims into opening a ZIP archive. This archive has an executable file titled “CPMPANY PROFILE.exe.”
This file, in line with Bitdefender’s weblog publish, hundreds the infamous Snake Keylogger payload on the focused system’s host. The information is exfiltrated by means of SMTP.
What’s Snake Keylogger?
It’s an notorious credential and info-stealing malware that exfiltrates delicate knowledge from contaminated machines. It has screenshot capturing and keyboard logging capabilities. It’s a large menace to enterprises due to its spying and knowledge harvesting options.
Along with that, it could steal info from system clipboards. Additionally it is known as 404 Keylogger. The trojan surfaced in 2020 and is at present out there at underground marketplaces/message boards for just a few hundred {dollars}. The malware is used generally in financially motivated campaigns, together with identification theft and fraud-based campaigns.
Methods to Shield Your self?
A keylogger information each keystroke you make, giving hackers entry to your private info, passwords, and monetary knowledge. However there are steps you may take to guard your self.
One of the simplest ways to guard your gadget is by verifying the validity and origin of correspondence earlier than clicking on any attachment. Additionally, set up the business’s most dependable safety options and defend your accounts with 2FA or MFA processes.
Associated Information
- US Warns Companies About North Korean Hackers Posing as IT Employees
- Cisco Confirms Breach After Worker’s Google Account was Hacked
- Twitter Confirms Knowledge Breach as 5.4M Accounts Bought on Hacker Discussion board
- Hackers posing as LinkedIn recruiters to rip-off army, aerospace companies
- Hackers hit Europe’s largest healthcare supplier with Snake ransomware