The menace actor often known as SideWinder has added a brand new customized instrument to its arsenal of malware that is being utilized in phishing assaults towards Pakistani private and non-private sector entities.
“Phishing hyperlinks in emails or posts that mimic authentic notifications and companies of presidency companies and organizations in Pakistan are major assault vectors of the gang,” Singapore-headquartered cybersecurity firm Group-IB mentioned in a Wednesday report.
SideWinder, additionally tracked underneath the monikers Hardcore Nationalist, Rattlesnake, Razor Tiger, and T-APT-04, has been lively since no less than 2012 with a major concentrate on Pakistan and different Central Asian international locations like Afghanistan, Bangladesh, Nepal, Singapore, and Sri Lanka.
Final month, Kaspersky attributed to this group over 1,000 cyber assaults that passed off previously two years, whereas calling out its persistence and complex obfuscation methods.
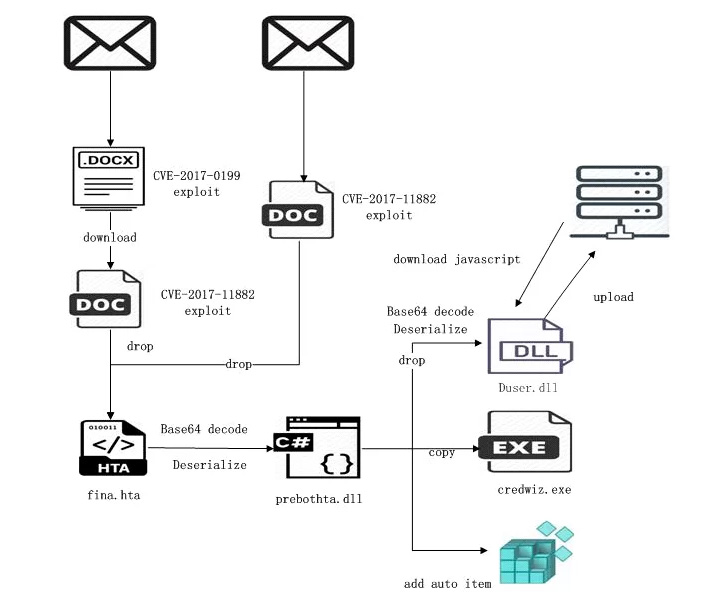
The menace actor’s modus operandi entails using spear-phishing emails to distribute malicious ZIP archives containing RTF or LNK information, which obtain an HTML Software (HTA) payload from a distant server.
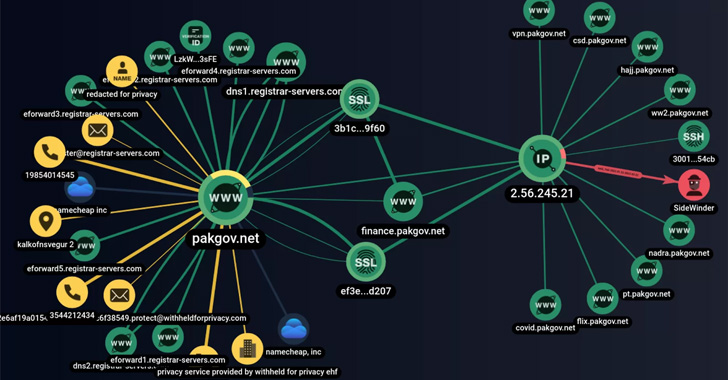
That is achieved by embedding fraudulent hyperlinks which are designed to imitate authentic notifications and companies of presidency companies and organizations in Pakistan, with the group additionally organising lookalike web sites posing as authorities web sites to reap consumer credentials.
The customized instrument recognized by Group-IB, dubbed SideWinder.AntiBot.Script, acts as a visitors path system diverting Pakistani customers clicking on the phishing hyperlinks to rogue domains.
Ought to a consumer whose consumer’s IP handle differs from Pakistan’s faucet on the hyperlink, the AntiBot script redirects to an genuine doc situated on a authentic server, indicating an try to geofence its targets.
“The script checks the consumer browser setting and, primarily based on a number of parameters, decides whether or not to challenge a malicious file or redirect to a authentic useful resource,” the researchers mentioned.
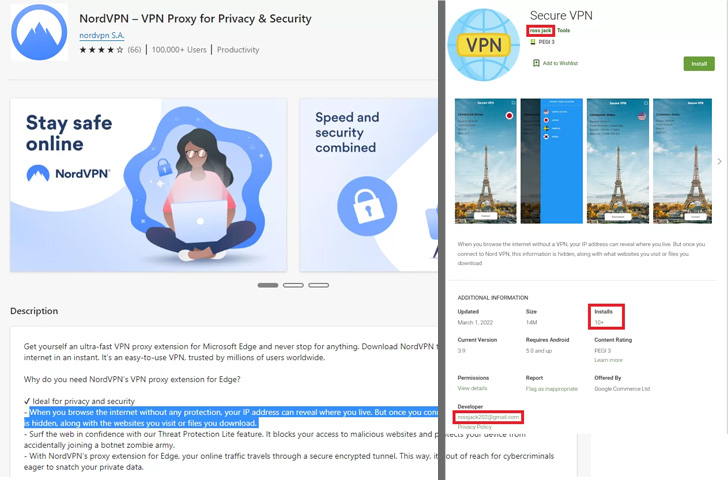
Of particular point out is a phishing hyperlink that downloads a VPN utility known as Safe VPN (“com.securedata.vpn”) from the official Google Play retailer in an try to impersonate the authentic Safe VPN app (“com.securevpn.securevpn”).
Whereas the precise goal of the faux VPN app stays unclear, this isn’t the primary time SideWinder has sneaked previous Google Play Retailer protections to publish rogue apps underneath the pretext of utility software program.
In January 2020, Pattern Micro detailed three malicious apps that had been disguised as pictures and file supervisor instruments that leveraged a safety flaw in Android (CVE-2019-2215) to achieve root privileges in addition to abuse accessibility service permissions to reap delicate info.