Excessive-profile authorities entities in Southeast Asia are the goal of a cyber espionage marketing campaign undertaken by a Chinese language risk actor often known as Sharp Panda since late final yr.
The intrusions are characterised by means of a brand new model of the Soul modular framework, marking a departure from the group’s assault chains noticed in 2021.
Israeli cybersecurity firm Examine Level mentioned the “long-running” actions have traditionally singled out nations comparable to Vietnam, Thailand, and Indonesia. Sharp Panda was first documented by the agency in June 2021, describing it as a “highly-organized operation that positioned vital effort into remaining below the radar.”
Using the Soul backdoor in real-world assaults was first detailed by Broadcom’s Symantec in October 2021 in connection to an unattributed espionage operation focusing on protection, healthcare, and ICT sectors in Southeast Asia.
The implant’s origins, in line with analysis revealed by Fortinet FortiGuard Labs in February 2022, date way back to October 2017, with the malware repurposing code from Gh0st RAT and different publicly accessible instruments.
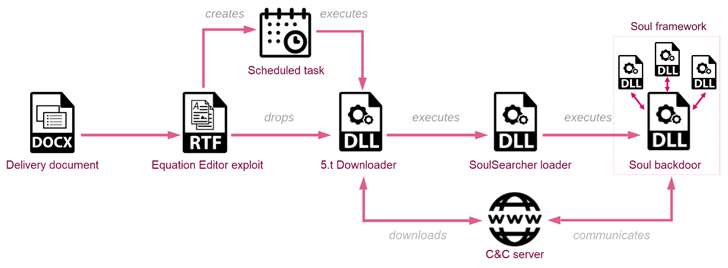
The assault chain documented by Examine Level begins with a spear-phishing electronic mail containing a lure doc that leverages the Royal Highway Wealthy Textual content Format (RTF) weaponizer to drop a downloader by exploiting certainly one of a number of vulnerabilities within the Microsoft Equation Editor.
The downloader, in flip, is designed to retrieve a loader often known as SoulSearcher from a geofenced command-and-control (C&C) server that solely responds to requests originating from IP addresses similar to the focused nations.
The loader is then liable for downloading, decrypting, and executing the Soul backdoor and its different elements, thereby enabling the adversary to reap a variety of knowledge.
“The Soul primary module is liable for speaking with the C&C server and its major function is to obtain and cargo in reminiscence extra modules,” Examine Level mentioned.
Uncover the Hidden Risks of Third-Celebration SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be a part of our webinar to be taught in regards to the varieties of permissions being granted and decrease danger.
“Curiously, the backdoor configuration incorporates a ‘radio silence’-like function, the place the actors can specify particular hours in per week when the backdoor will not be allowed to speak with the C&C server.”
The findings are one more indication of the software sharing that is prevalent amongst Chinese language superior persistent risk (APT) teams to facilitate intelligence gathering.
“Whereas the Soul framework has been in use since not less than 2017, the risk actors behind it have been always updating and refining its structure and capabilities,” the corporate mentioned.
It additional famous that the marketing campaign is probably going “staged by superior Chinese language-backed risk actors, whose different instruments, capabilities and place inside the broader community of espionage actions are but to be explored.”